Introduction
If you've been following our journey, you'll recall our previous explorations into the AWS Session Manager and AWS Inspector Vulnerability Management. In our ongoing quest for comprehensive cloud security, we've peeled back layers to uncover the practical applications and benefits of these integral AWS services.
Today, our focus shifts to the underlying technology - AWS Systems Manager (SSM). Covering the service that orchestrates the seamless integration of Run Command, Inventory, Session Manager, Compliance, Patch Manager and many more.
So, buckle up as we journey into the heart of SSM, unveiling the possibilities that make it more than just a collection of services – it's a unified powerhouse, engineered to simplify your cloud operations while enhancing the security of your AWS resources.
AWS SSM is the command center for managing and monitoring your AWS resources. It provides a unified user interface that lets you view operational data from multiple AWS services in one place.
Installing AWS Systems Manager: A Swift Guide 🚀
Now that we're set to explore the inner workings of AWS SSM, the first step is to ensure it's seamlessly integrated into your AWS environment. Installing AWS Systems Manager is a straightforward process. To initiate the installation, follow these basic steps:
AWS Identity and Access Management (IAM) Setup
Ensure that your IAM roles are configured appropriately to grant the necessary permissions for Systems Manager. The recommended approach is to leverage the AWS-managed policy, AmazonSSMManagedInstanceCore, which contains the minimum set of permissions required for Systems Manager to interact with your instances.
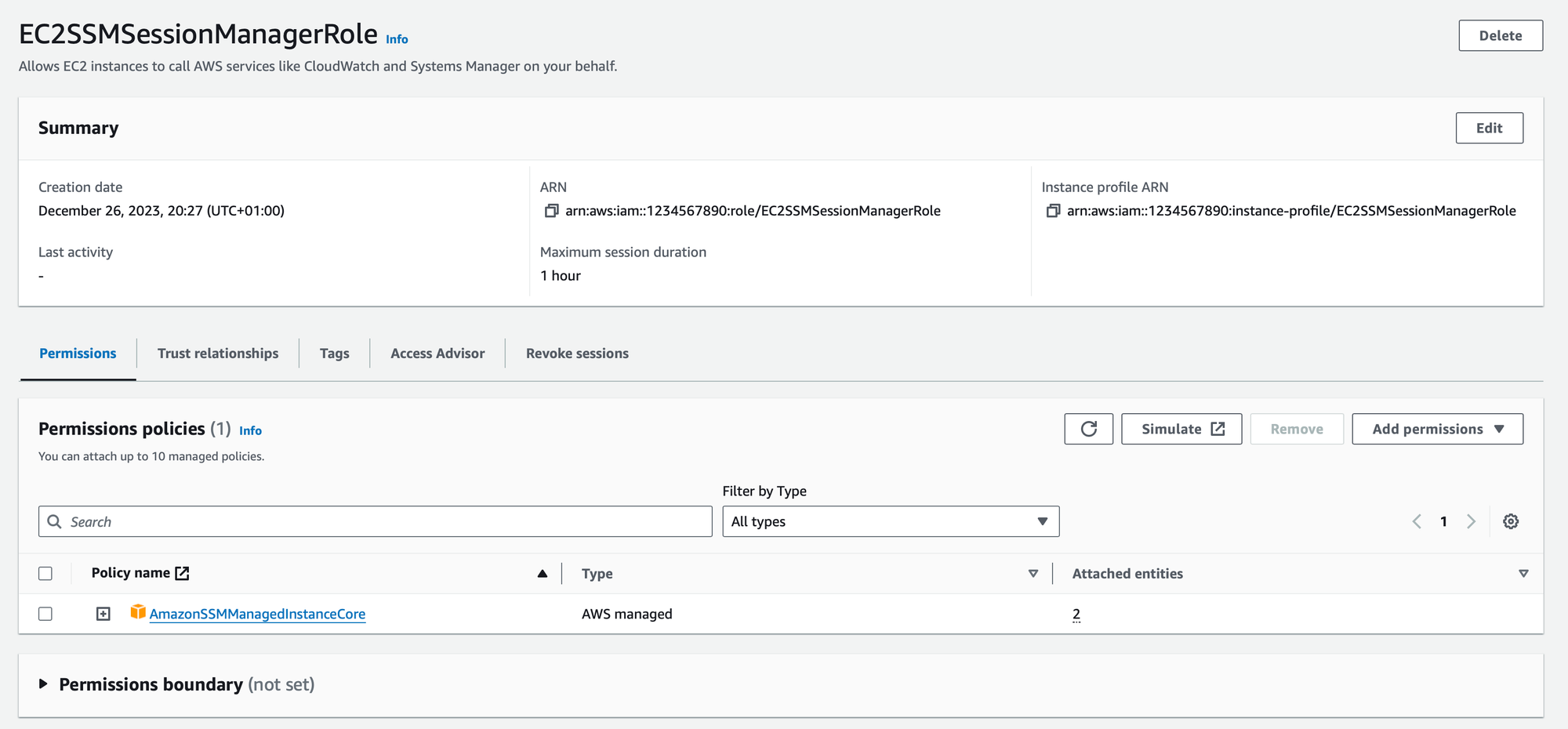
Additionally, you need to define a trust relationship for the IAM role, specifying the services that should be allowed to assume this role. This ensures that Systems Manager has the necessary permissions to execute commands and manage instances on your behalf:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "ec2.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}Instance Preparation
It's essential to ensure that the AWS Systems Manager agent (SSM Agent) is installed and running on each targeted instance. The agent acts as the liaison between your instances and Systems Manager, facilitating seamless communication.
While you can install the AWS SSM Agent manually, you can also automate this process by utilizing AWS EC2 user data. Keep in mind that the user data script may vary based on the operating system and specific configurations of the instances where you want to install SSM.
For example, you can use user data in the EC2 launch configuration (Please adjust the command based on your OS. You can find the right command here):
#!/bin/bash
cd /tmp
sudo yum install -y https://s3.amazonaws.com/ec2-downloads-windows/SSMAgent/latest/linux_amd64/amazon-ssm-agent.rpm
sudo systemctl enable amazon-ssm-agent
sudo systemctl start amazon-ssm-agentVerification and Monitoring
After installation and activation, it's crucial to verify the connectivity and functionality of AWS SSM on your instances. Utilize Systems Manager Run Command or Session Manager to execute commands or access instances, ensuring everything is in order.
Run Command: Streamlining Operations ⚙️
Run Command is your go-to tool for executing commands across a fleet of instances, be it Windows or Linux, in an automated and secure manner. Whether it's updating software, configuring applications, or troubleshooting, Run Command lets you handle tasks efficiently and at scale. With just a few clicks, you can execute commands across thousands of instances, saving you time and ensuring consistency.
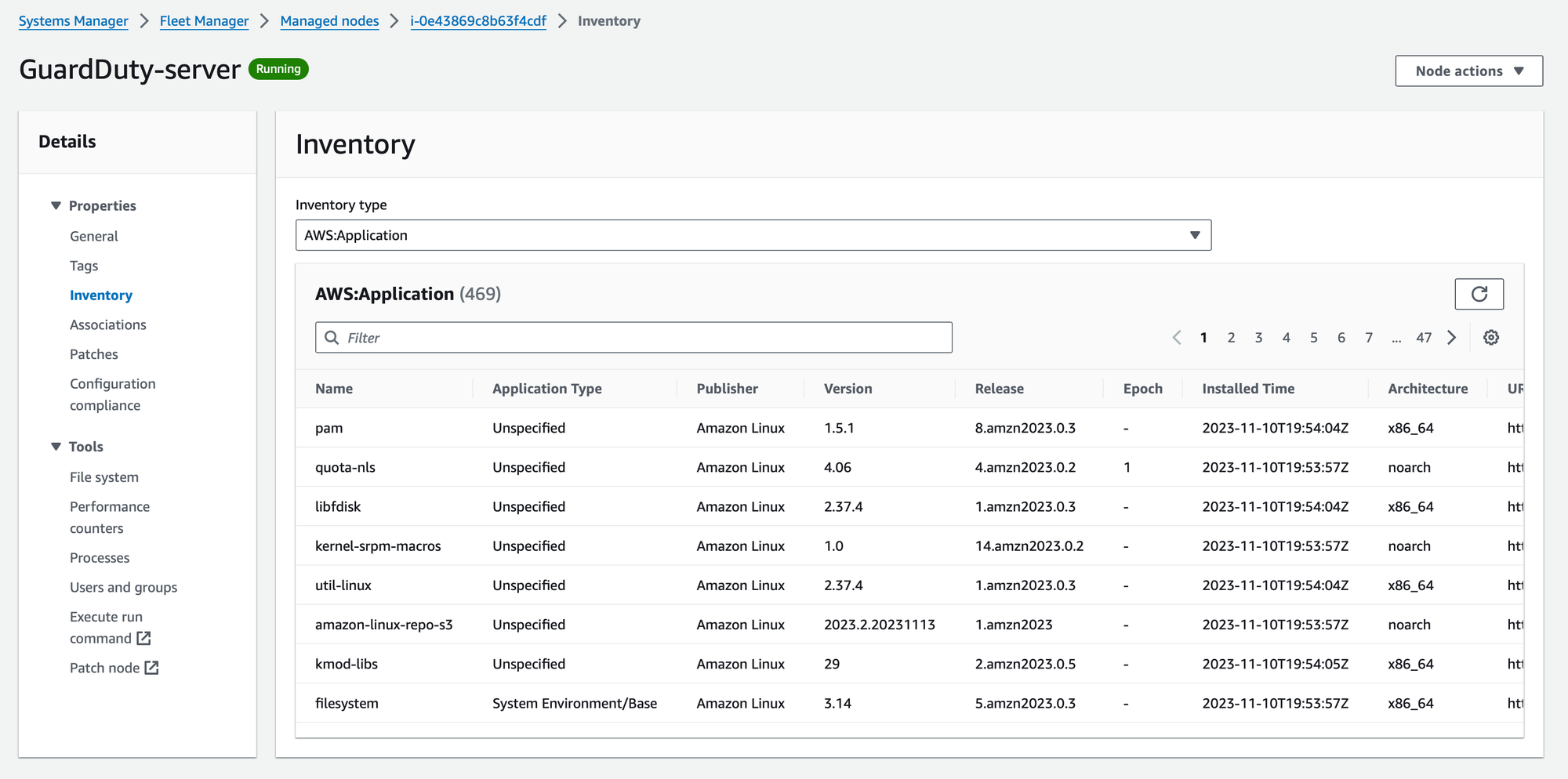
Inventory: Know Your Assets 📊
Knowledge is power, especially in cloud security. Inventory allows you to collect and query crucial metadata from your instances. By maintaining an accurate inventory, you gain a comprehensive understanding of your assets, aiding in security audits, compliance checks, and overall resource management.
Session Manager: Secure Remote Access 🔐
Gone are the days of relying on SSH or RDP for remote access. Session Manager provides a secure and auditable solution for connecting to your instances without the need for open inbound ports. With fine-grained access controls and session logs, you can ensure that only authorized personnel access your instances, enhancing security and simplifying remote management.
Note: For an in-depth dive into AWS SSM Session Manager, be sure to check out our separate blog article.

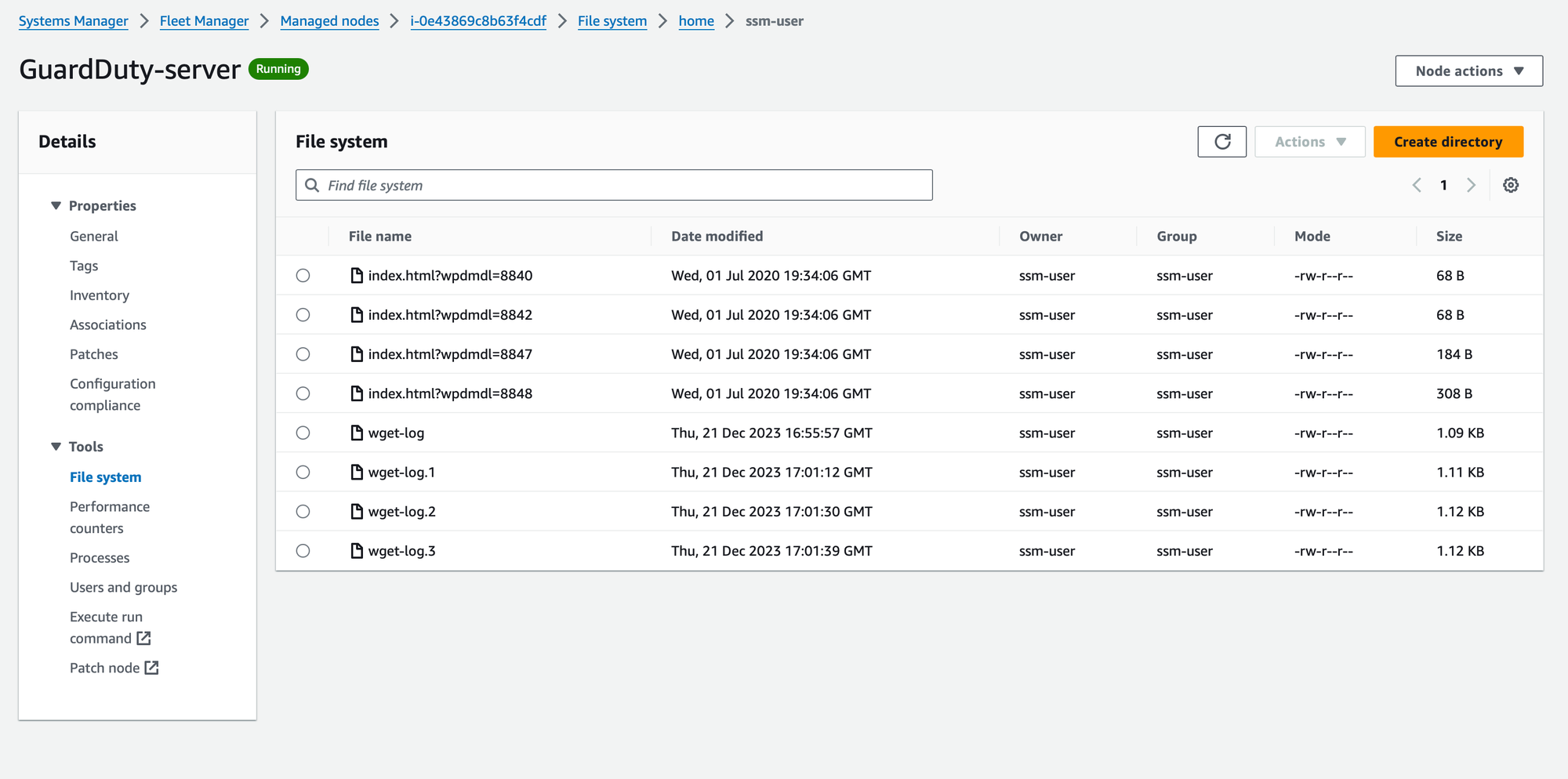
Exploring AWS Systems Manager File Explorer: Navigating Your Cloud File Systems with Ease 🧭
Designed to simplify the management of your instances, File Explorer provides an intuitive interface for browsing and interacting with the file systems of your connected instances.
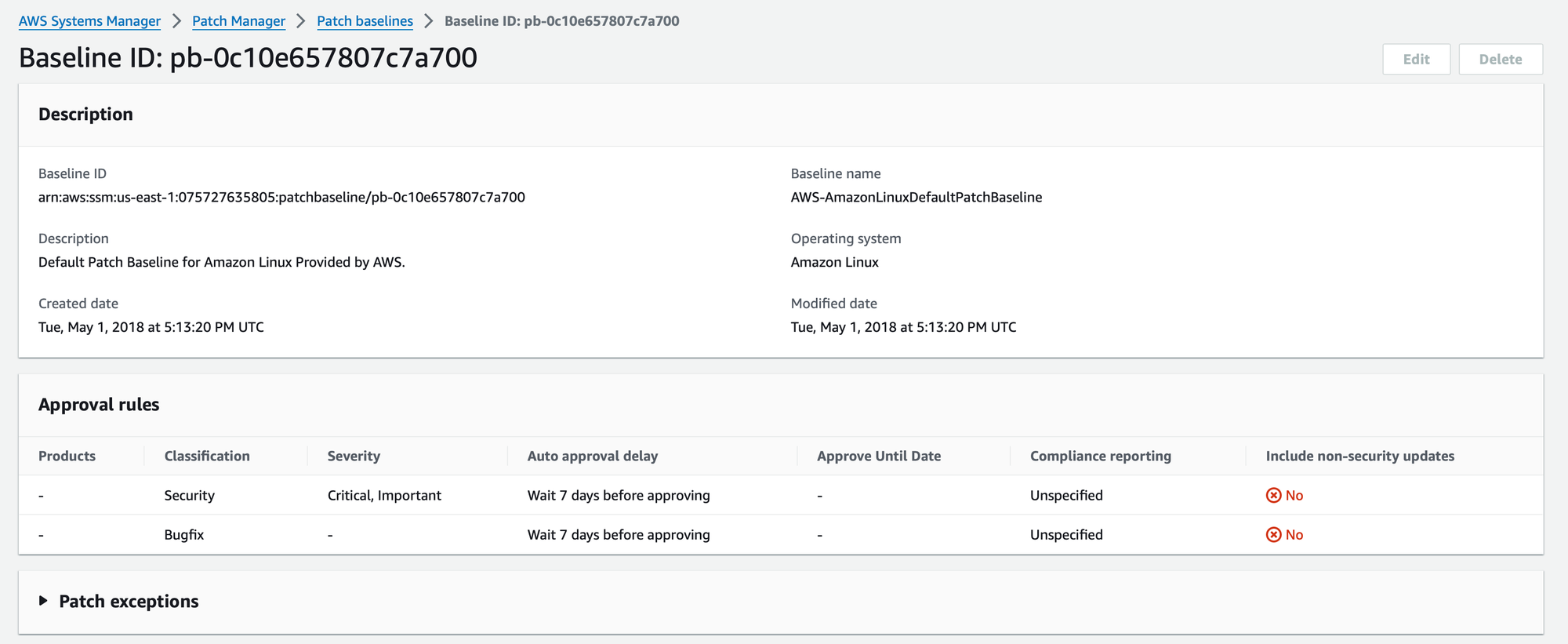
Patch Manager: Keeping Software Up to Date 🛠️
The importance of timely software updates cannot be overstated. Patch Manager automates the process of keeping your instances up to date with the latest security patches. From defining patch baselines to scheduling maintenance windows, Patch Manager streamlines the patching process, reducing vulnerabilities and securing your cloud infrastructure.
Patch baselines in AWS Systems Manager serve as blueprints for the patching process. They allow you to establish rules and controls regarding which patches should be applied to your instances. What sets Patch Manager apart is its adaptability to diverse operating systems, accommodating the unique patching requirements of Windows, Linux, and other supported platforms.
Compliance: Stay Aligned with Best Practices 📜
Compliance empowers you to scan your managed nodes for patch compliance. It assesses whether the installed patches on your instances adhere to the defined patch baselines. Beyond patching, Compliance extends its scrutiny to configuration inconsistencies. It verifies whether the configurations of your instances align with the specified baselines, ensuring that your infrastructure maintains a consistent and secure posture.
Vulnerability Management with AWS Inspector: A Sneak Peek 🔍
AWS Inspector is now an integral part of AWS SSM, enhancing its capabilities by automating the assessment of applications. This collaboration streamlines your security operations, providing a unified platform to manage both operational tasks and vulnerability assessments seamlessly.
Note: For an in-depth dive into AWS Inspector, be sure to check out our separate blog article.











