Introduction
Managing AWS instances can be a complex process, often requiring the use of an SSH client to access them. However, using SSH requires opening ports in security groups, 🛡️ it also presents security risks. 💻 An SSH client is unnecessary when using AWS Session Manager as a secure access method for instances.
📖 In this article, we’ll explore the benefits of using AWS Session Manager and provide a step-by-step guide on streamlining instance management.
Table of contents
What is AWS Session Manager? 👋
How to use AWS Session Manager 🛠️
Create a new role for AWS EC2
Install AWS SSM and attach the IAM role
Access the AWS Session Manager 💻
Troubleshooting
Conclusion 🙌
What is AWS Session Manager? 👋
AWS Systems Manager (SSM) includes a tool called AWS Session Manager. Users can access instances without opening ports in security groups or requiring an SSH client.
To access instances through the AWS Management Console, it instead uses an HTTPS connection. It uses the AWS SSM agent which can be installed on all leading operating systems. This makes it more secure in comparison to SSH.
Some benefits of using AWS Session Manager for instance management include:
- 🔒 Improved security: No need to open inbound or outbound ports in security groups.
- 👥 Centralized access: Manage access to multiple instances from a single location and simplify the process of granting permissions.
- 🚀 Streamlined process: Perform actions on instances without the need for an SSH client. This reduces the number of tools you need to use and minimizes the attack surface.
How to use AWS Session Manager 🛠️
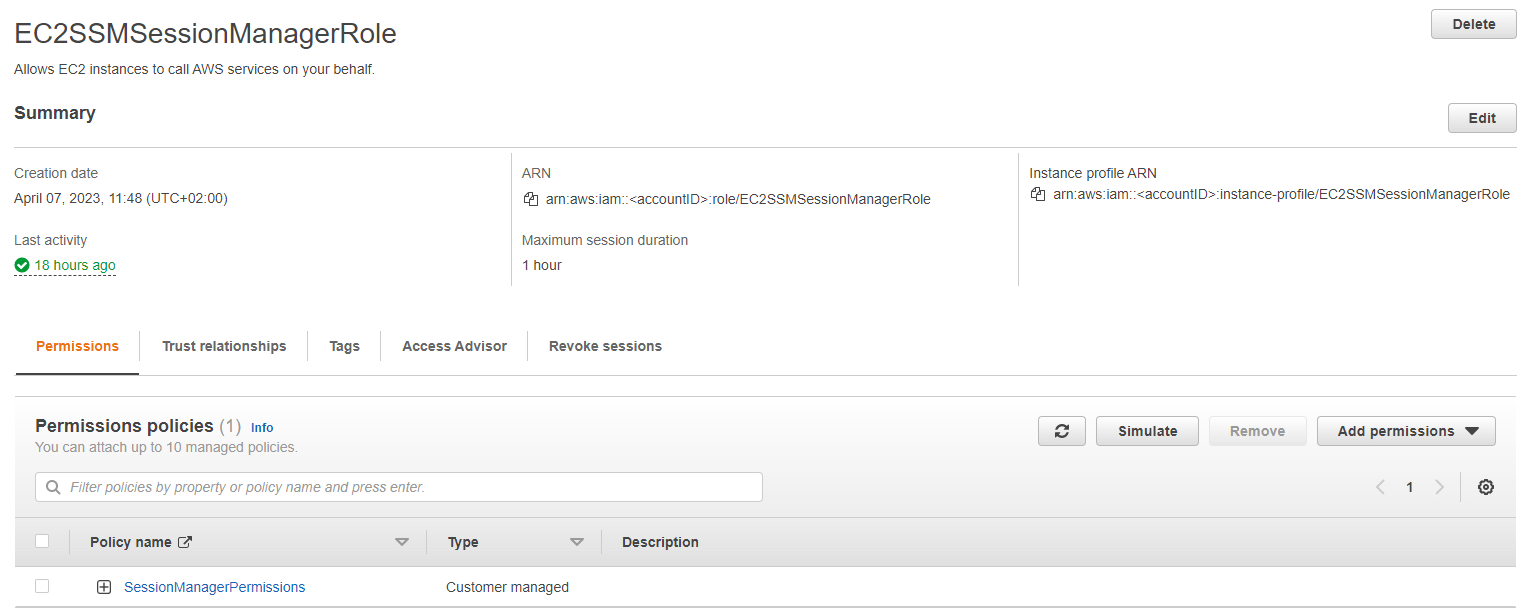
Create a new role for AWS EC2
First, we set up a new AWS IAM role. You can create a new policy, with minimal access. I named the policy SessionManagerPermissions:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"ssm:UpdateInstanceInformation",
"ssmmessages:CreateControlChannel",
"ssmmessages:CreateDataChannel",
"ssmmessages:OpenControlChannel",
"ssmmessages:OpenDataChannel"
],
"Resource": "*"
}
]
}Otherwise, you can also attach the AWS-managed policy AmazonSSMManagedInstanceCore. Lastly, we need to have a trust relationship with EC2:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "ec2.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}
Install AWS SSM and attach the IAM role
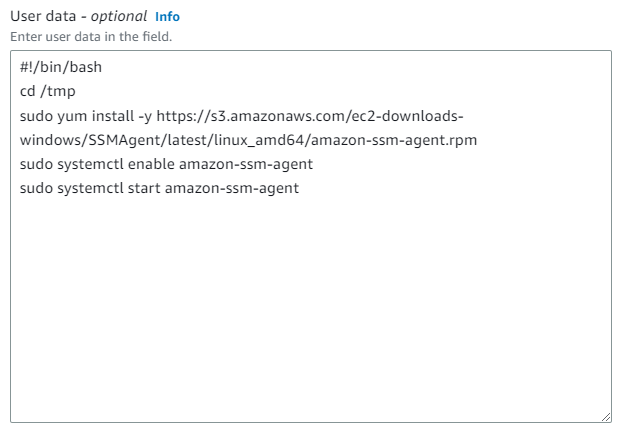
When launching an instance in Amazon EC2, there is an option to pass user data to the instance. This data can be used to perform automated configuration tasks and execute scripts after the instance starts.
I recommend using the user data to install the AWS SSM agent. The following command installs and enables it automatically:
#!/bin/bash
cd /tmp
sudo yum install -y https://s3.amazonaws.com/ec2-downloads-windows/SSMAgent/latest/linux_amd64/amazon-ssm-agent.rpm
sudo systemctl enable amazon-ssm-agent
sudo systemctl start amazon-ssm-agentTo configure the user data you need to navigate to the advanced details of the Launch an instance menu.
You also need to make sure to attach the previously created IAM role. You can also find this option in the advanced details:
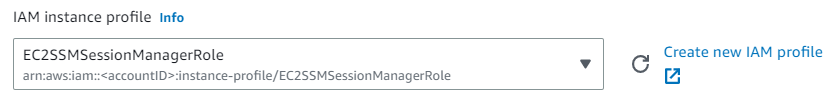
Access the AWS Session Manager 💻
Now everything is set up to access your instance. In the console, you can now navigate to AWS SSM. In the Node Management section, you can start a new session:
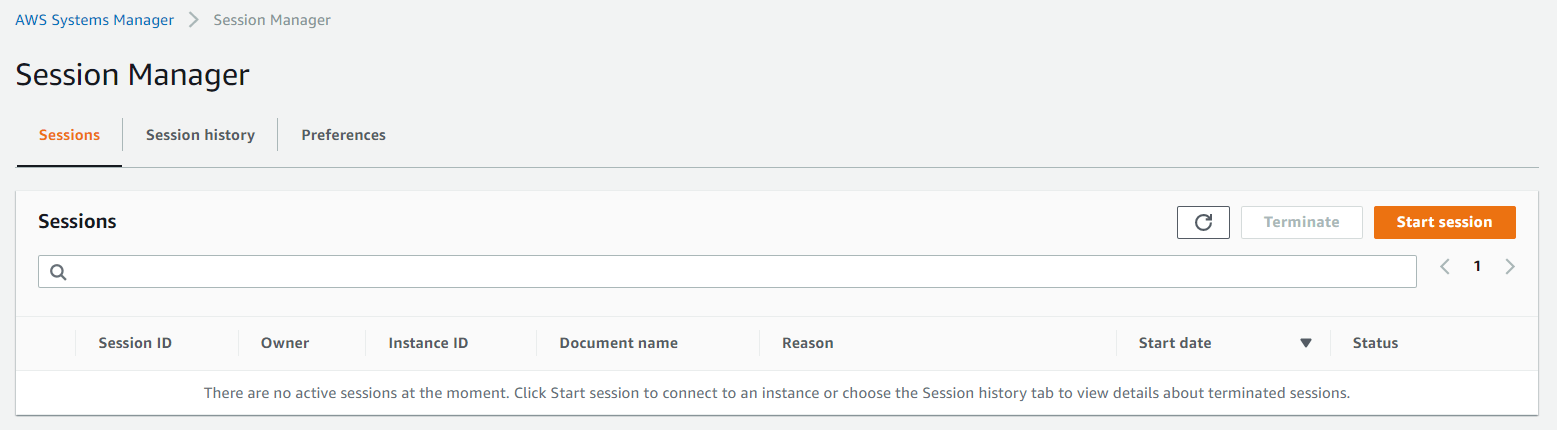
Next, we can choose the instance we want to connect to.
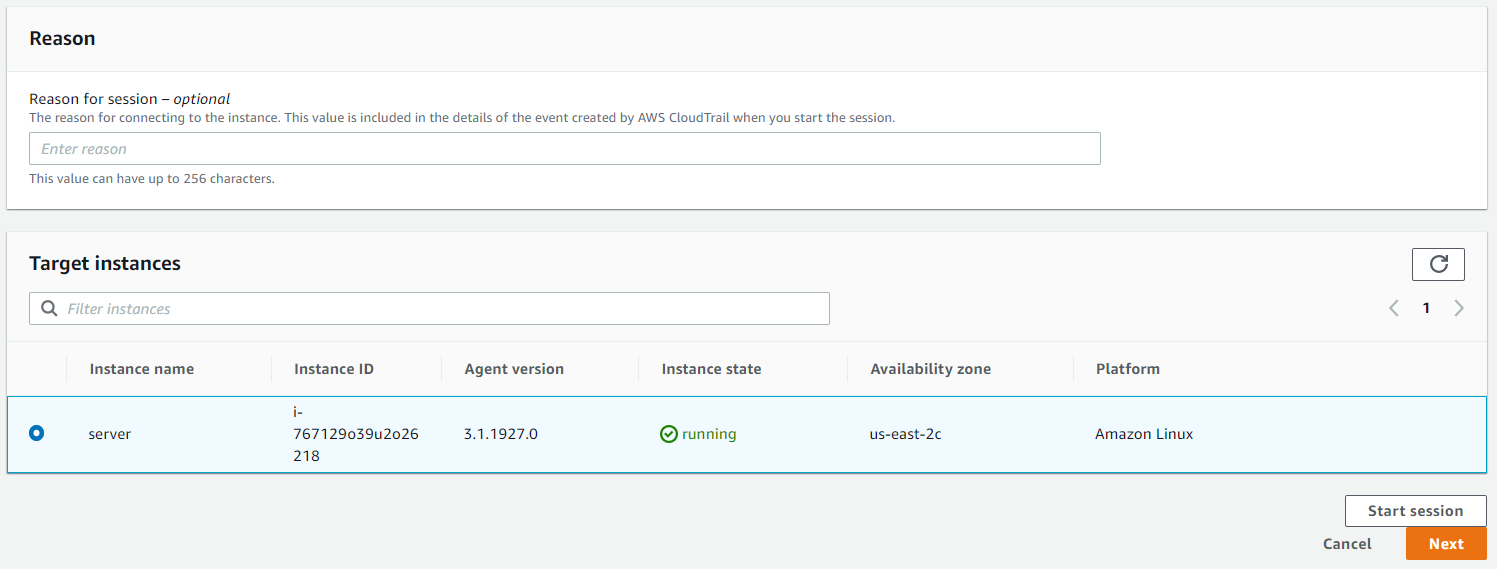
We will be presented with a shell and can run any command from the AWS console.
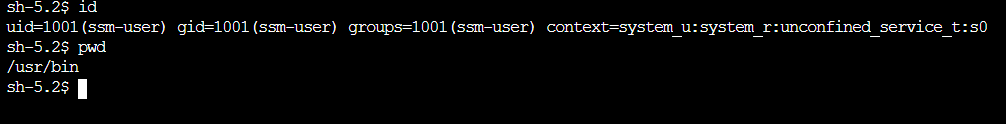
Troubleshooting
If no instance is showing up in the AWS Session Manager console. Check the following two things:
- AWS SSM agent: Ensure the AWS SSM agent is installed via EC2 user data or manually.
- IAM policy: Confirm the custom created
SessionManagerPermissionsor theAmazonSSMManagedInstanceCorepolicy is added to the role. And the role is attached to the EC2 instance.
Conclusion 🙌
AWS Session Manager is a powerful tool that simplifies AWS instance management by providing a secure, centralized, and streamlined way to access and manage instances. With AWS Session Manager, you can reduce the need for SSH and improve the security of your AWS infrastructure. Especially management of SSH keys in large organizations is a cumbersome process and increases the risks for the organizations. 💡 Try out AWS Session Manager and see how it can benefit your instance management process.
Additionally, you can also log all commands from the AWS Session Manager to CloudWatch or S3 for additional governance. You need to adjust the configuration of Session Manager and the attached role for that.




Member discussion