GuardDuty Unveiled 🧯
Before we dive into the nitty-gritty of runtime protection, let's take a moment to understand what AWS GuardDuty is all about. GuardDuty is like a vigilant digital sentry, constantly scanning your AWS environment for any signs of malicious activity. It uses intelligent threat detection algorithms, machine learning, and anomaly detection to keep a watchful eye on your infrastructure.
The Essence of Runtime Protection
Now, let's zone in on the runtime protection aspect, focusing on our EC2 instances. Runtime, in the computing world, is the period when your application is executing. AWS GuardDuty's runtime protection ensures that during this crucial phase, your EC2 instances remain shielded from potential threats.
We always had a gap, a vulnerability during the runtime, but now GuardDuty bridges that gap, offering a proactive approach.
Key Features of GuardDuty Runtime Protection ✨
1. Real-Time Threat Detection
GuardDuty doesn't believe in 'fashionably late'. It works in real-time, meaning it identifies and alerts you about potential threats the moment they rear their heads. This swift action can be the difference between a minor hiccup and a major security breach.
2. Agent Deployment for Enhanced Protection
To maximize the potency of GuardDuty's runtime protection, deployment of an agent is required. This streamlined process enhances the tool's capabilities.
Setting Up GuardDuty Runtime Protection for EC2 Instances 🔒
Implementing GuardDuty runtime protection for your EC2 instances is a breeze. AWS has designed a user-friendly way that allows you to enable this feature with just a few clicks.
Installing AWS SSM
AWS Systems Manager acts as the facilitator for deploying and managing agents on your EC2 instances. If you're not familiar with the installation of AWS SSM, check out my detailed guide:

This step is crucial as it lays the foundation for a seamless integration, allowing GuardDuty to leverage SSM capabilities.
Create VPC Endpoint
As GuardDuty's runtime protection for EC2 instances is in preview, establishing a VPC (Virtual Private Cloud) endpoint is a required step to facilitate secure communication with GuardDuty services. Here's a simple guide to creating a VPC endpoint:
- Navigate to the VPC Dashboard in the AWS Management Console.
- Select "Endpoints" from the left-hand navigation pane.
- Click "Create Endpoint" and choose "Other Endpoint Services" as the service category.
- In the "Service Name" field, type:
com.amazonaws.<region>.guardduty-data, replace<region>with the appropriate AWS region code, such as us-east-1.
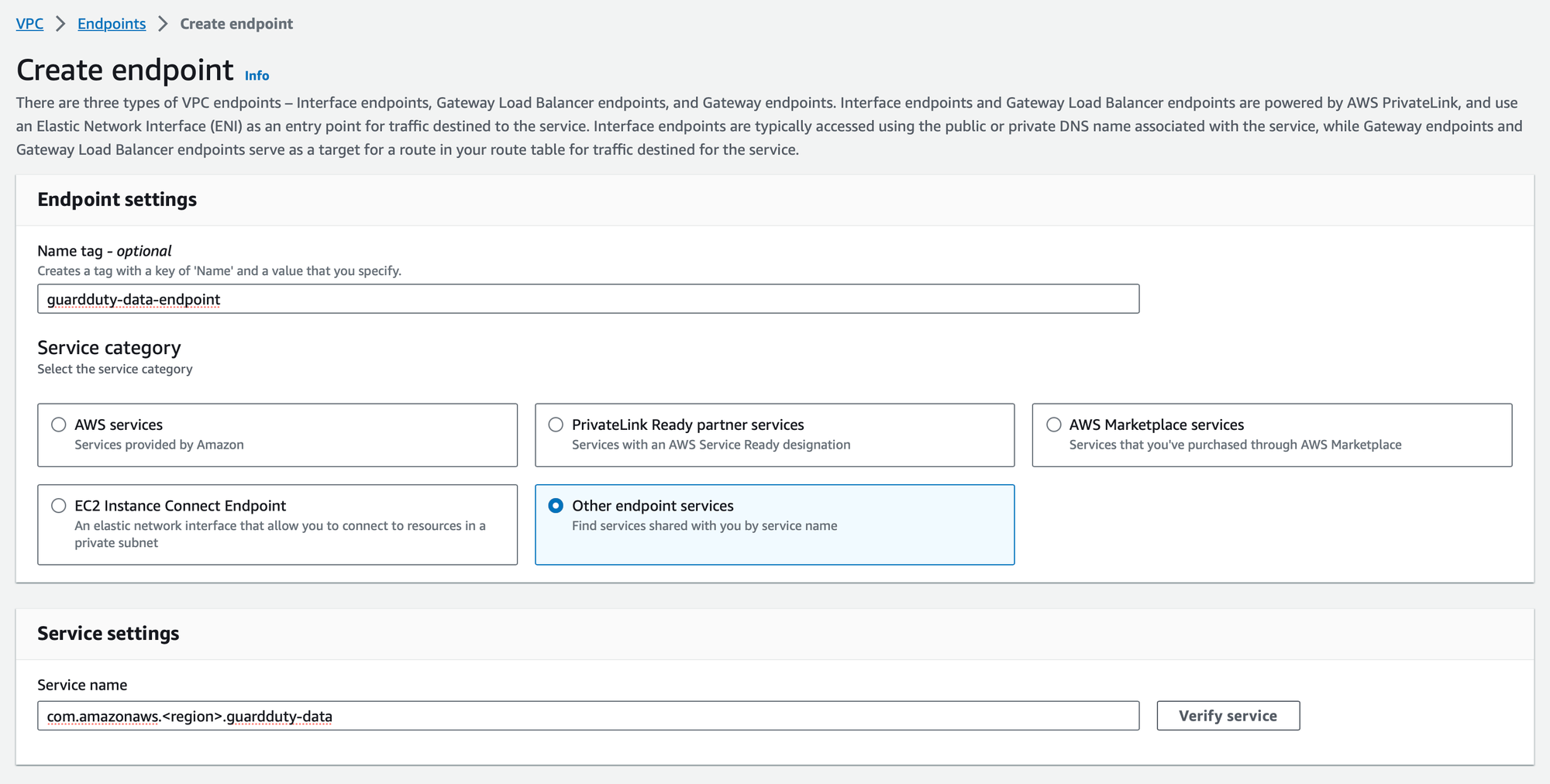
Specify your VPC and ensure to select "Enable DNS name resolution" to allow seamless communication with the GuardDuty service.
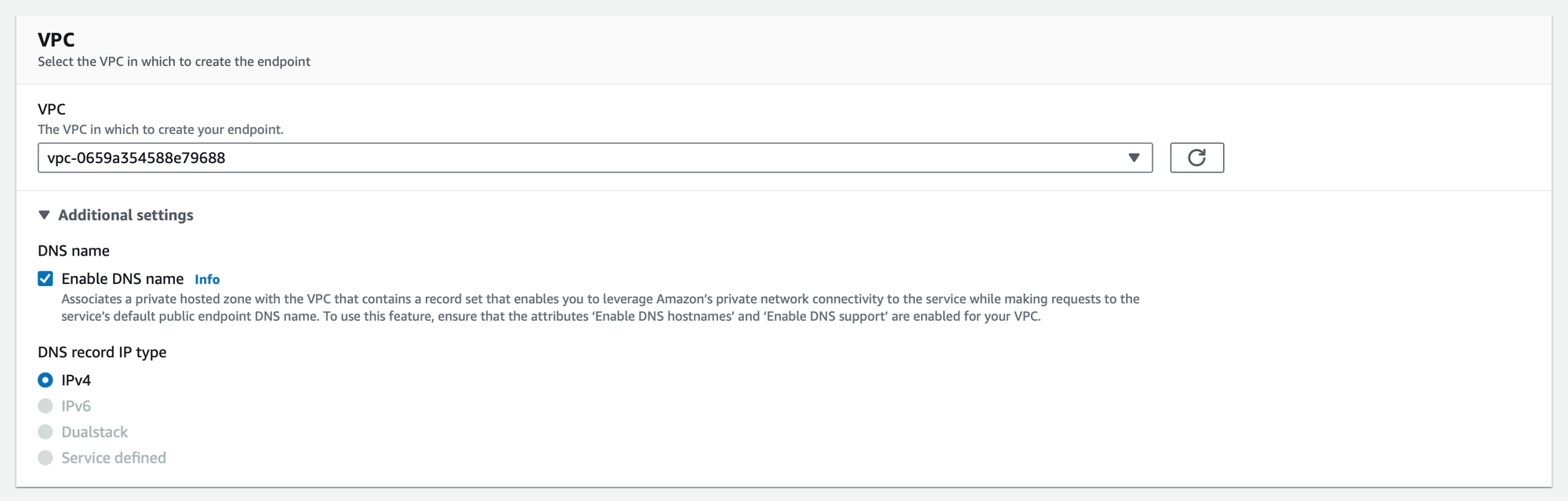
In the "Subnets" section, choose the subnets and availability zones where your EC2 instances reside. Next, for the security group configuration, it is important to verify that the selected security group permits inbound access from either your VPC or individual EC2 instances via port 443. This is crucial for establishing secure communication with GuardDuty.
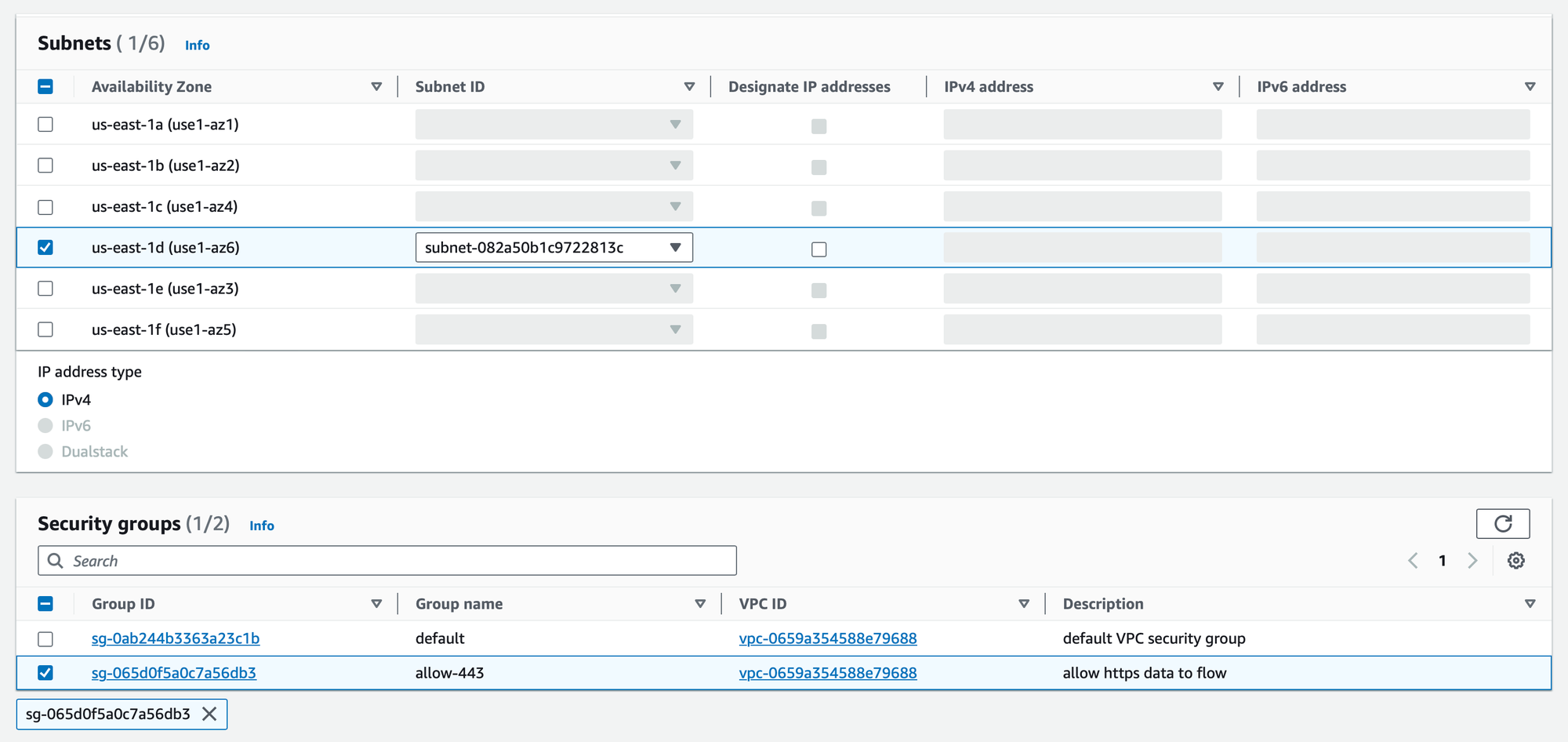
The final step involves crafting a custom policy to regulate access permissions. Here, you have two options for specifying access restrictions within your policy:
"aws:PrincipalAccount": "<accountID>"Use this when you want to restrict access to a specific AWS account. Replace<accountID>with the actual AWS account ID that you want to grant access to. This approach is suitable when you want to allow access exclusively to a single AWS account, ensuring a stringent and focused security measure."aws:PrincipalOrgID": "<OrgID>"Opt for this when you want to control access within an entire AWS Organization. Replace<OrgID>with the appropriate AWS Organization ID. This option is required when you want to extend access to all accounts within your organization, offering a more scalable approach to managing permissions across multiple accounts.
{
"Version": "2012-10-17",
"Statement": [
{
"Action": "*",
"Resource": "*",
"Effect": "Allow",
"Principal": "*"
},
{
"Condition": {
"StringNotEquals": {
"aws:PrincipalAccount": "<accountID>"
}
},
"Action": "*",
"Resource": "*",
"Effect": "Deny",
"Principal": "*"
}
]
}
Deploy the agent
Leveraging AWS Systems Manager Documents
AWS Systems Manager simplifies the installation process further by providing AWS-owned documents specifically designed for deploying GuardDuty agents. These documents encapsulate the installation and configurations from AWS, ensuring a standardized and secure deployment.
To initiate the installation using AWS Systems Manager Documents:
- Navigate to AWS Systems Manager in the AWS Management Console.
- Select "Documents" from the left-hand navigation pane.
- In the search bar, look for "AmazonGuardDuty".
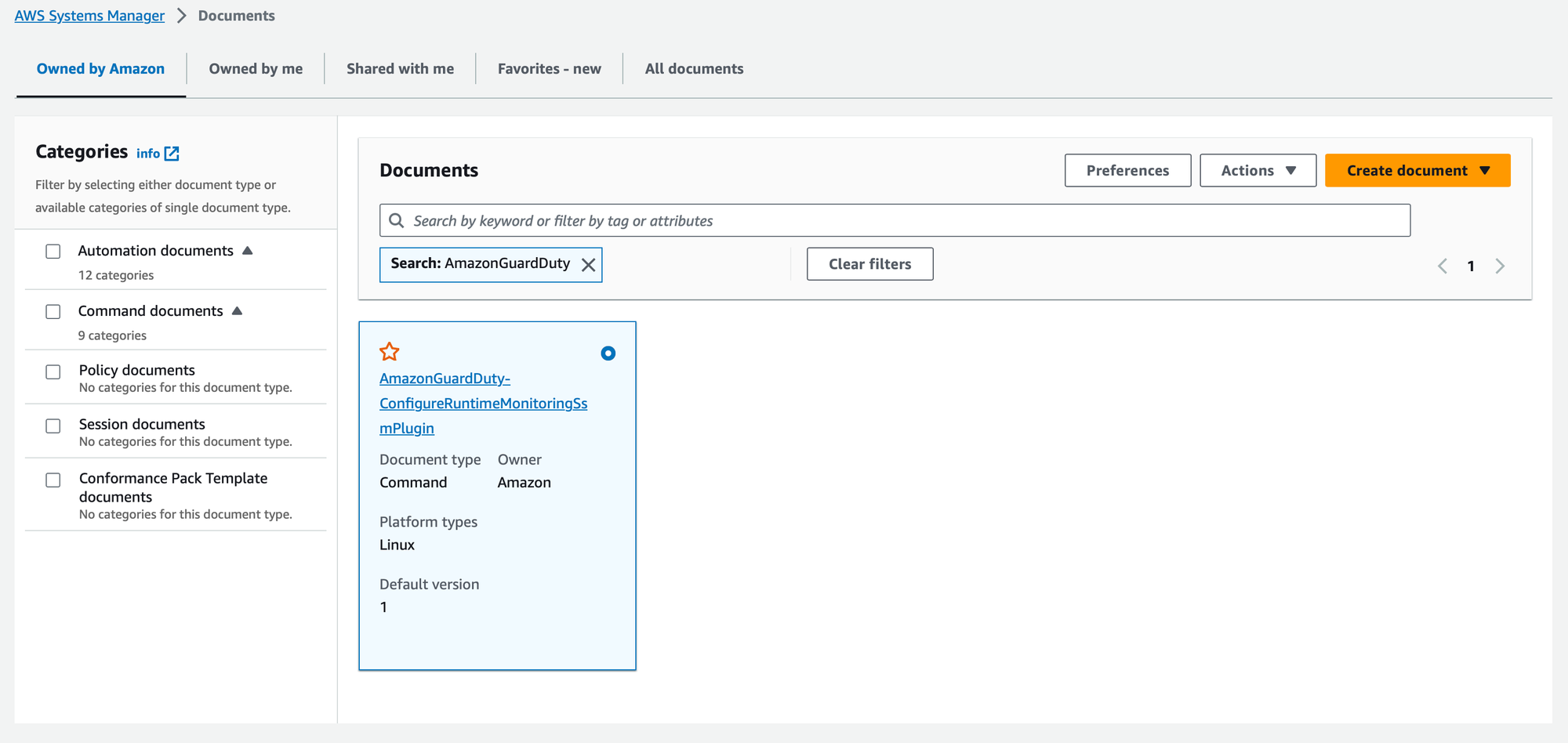
Configure the AWS SSM document
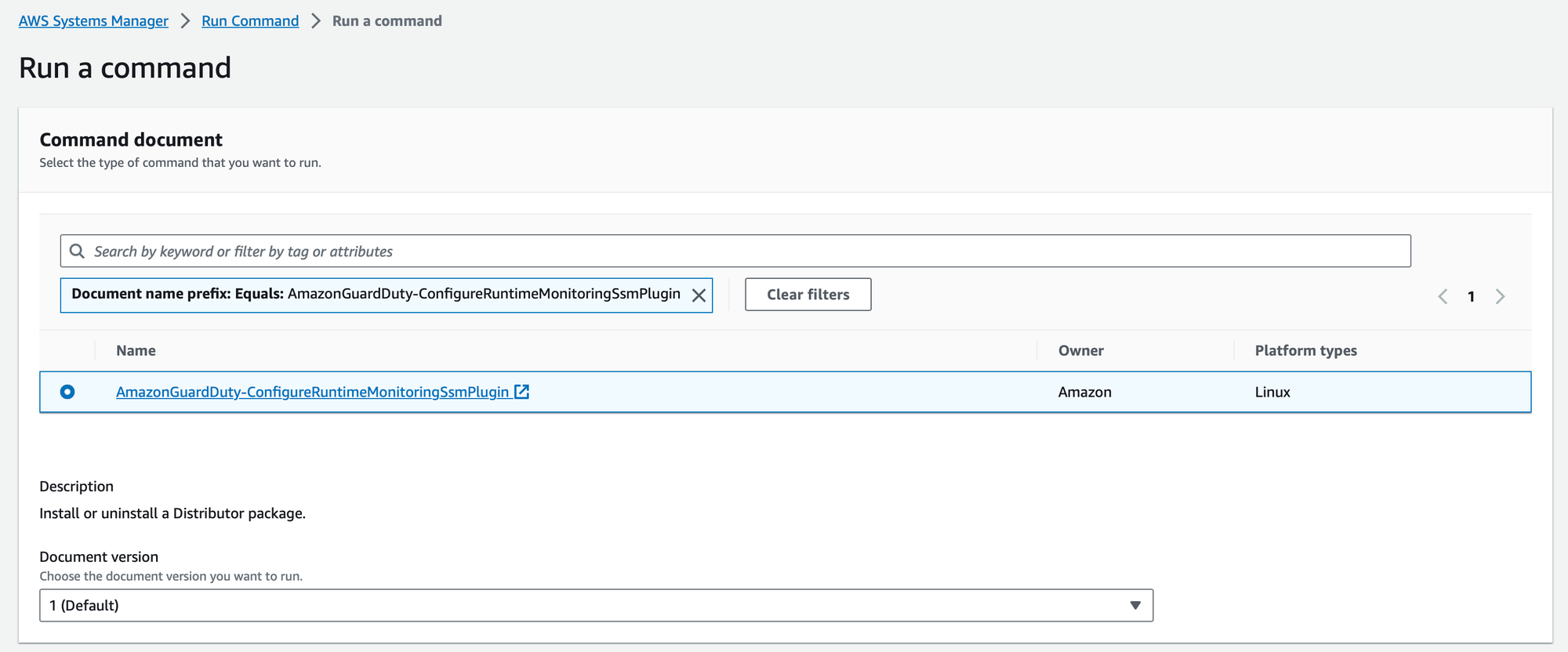
- Document version: Ensure you select the latest version of the document to benefit from the most up-to-date features and security enhancements.
- Action: Set the action to "Install" to instruct Systems Manager to install the GuardDuty agent on your EC2 instances.
- Name: Assign the name as
AmazonGuardDuty-RuntimeMonitoringSsmPlugin.
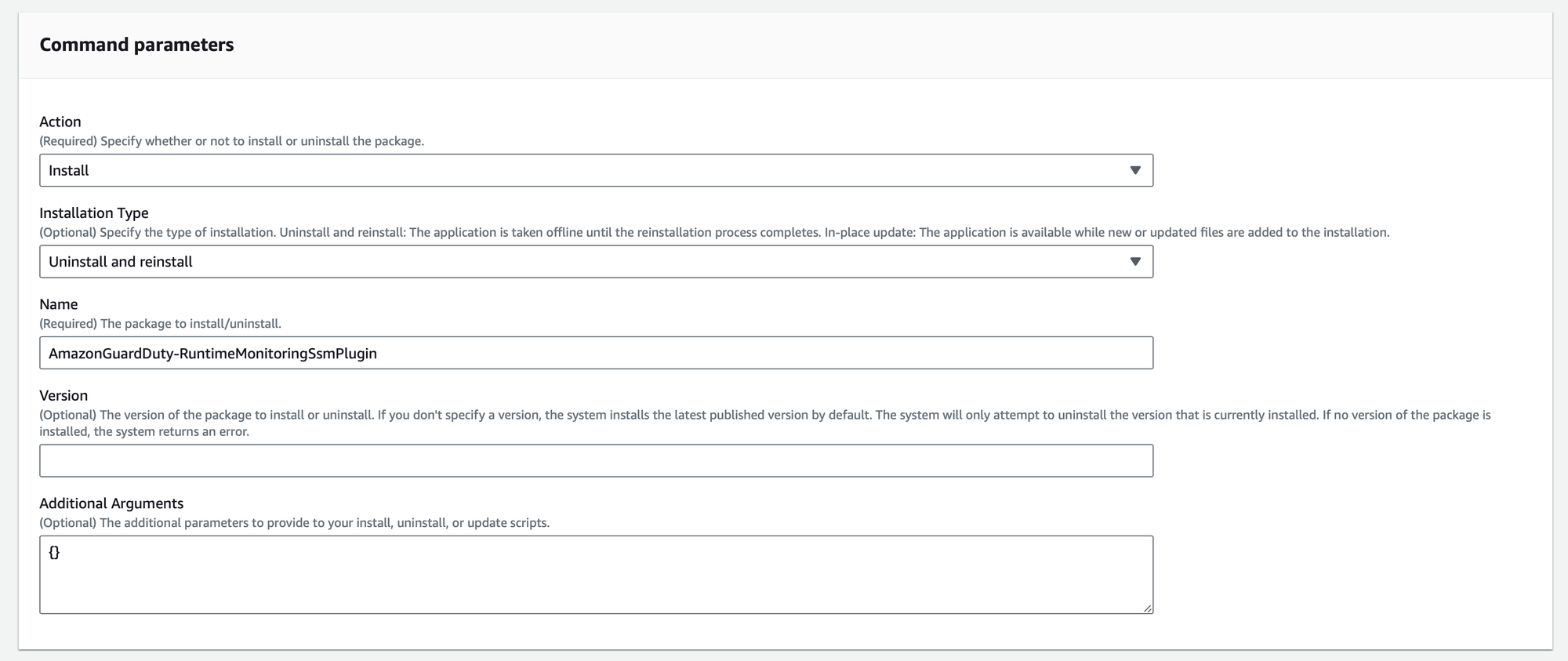
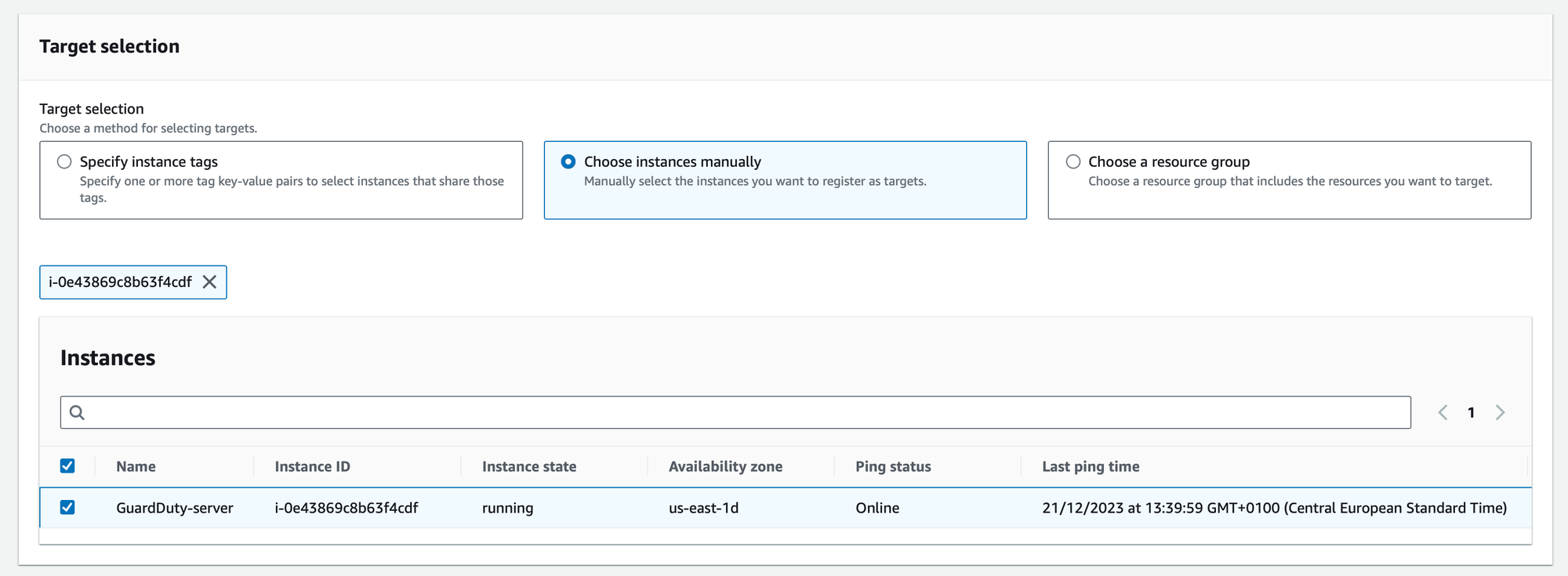
You can specify the EC2 instances that will be covered by this installation. You can select targets based on tags, resource groups, or individual instance IDs.
- Tag-Based Selection: Utilize tag-based targeting to apply the document to instances with specific tags. This approach provides more granular and refined control over the deployment process.
- Choose Instances Manually: For more fine-grained control, manually select specific instances to apply the GuardDuty runtime protection. This option is valuable when you have distinct security requirements for individual instances.
- Resource Groups: If you've organized your EC2 instances into resource groups, you can target the document to an entire group, streamlining the deployment process for multiple instances.
Verify the GuardDuty agent status
Once the AWS GuardDuty agent has been successfully deployed using AWS Systems Manager, it's crucial to ensure its proper functioning. Verify the status of the agent on your EC2 instances by executing the following command sudo systemctl status amazon-guardduty-agent. This command provides a status report, offering insights into the agent's health, configuration, and any potential issues. A successful status indicates that GuardDuty's runtime protection is actively safeguarding your EC2 instances:
sh-5.2$ sudo systemctl status amazon-guardduty-agent
● amazon-guardduty-agent.service - Amazon GuardDuty Agent
Loaded: loaded (/usr/lib/systemd/system/amazon-guardduty-agent.service; enabled; preset: disabled)
Active: active (running) since Thu 2023-12-21 12:47:38 UTC; 1min 43s ago
Main PID: 3639 (amazon-guarddut)
Tasks: 16 (limit: 1114)
Memory: 40.3M (max: 128.0M limit: 128.0M available: 87.6M)
CPU: 1.870s
CGroup: /system.slice/amazon-guardduty-agent.service
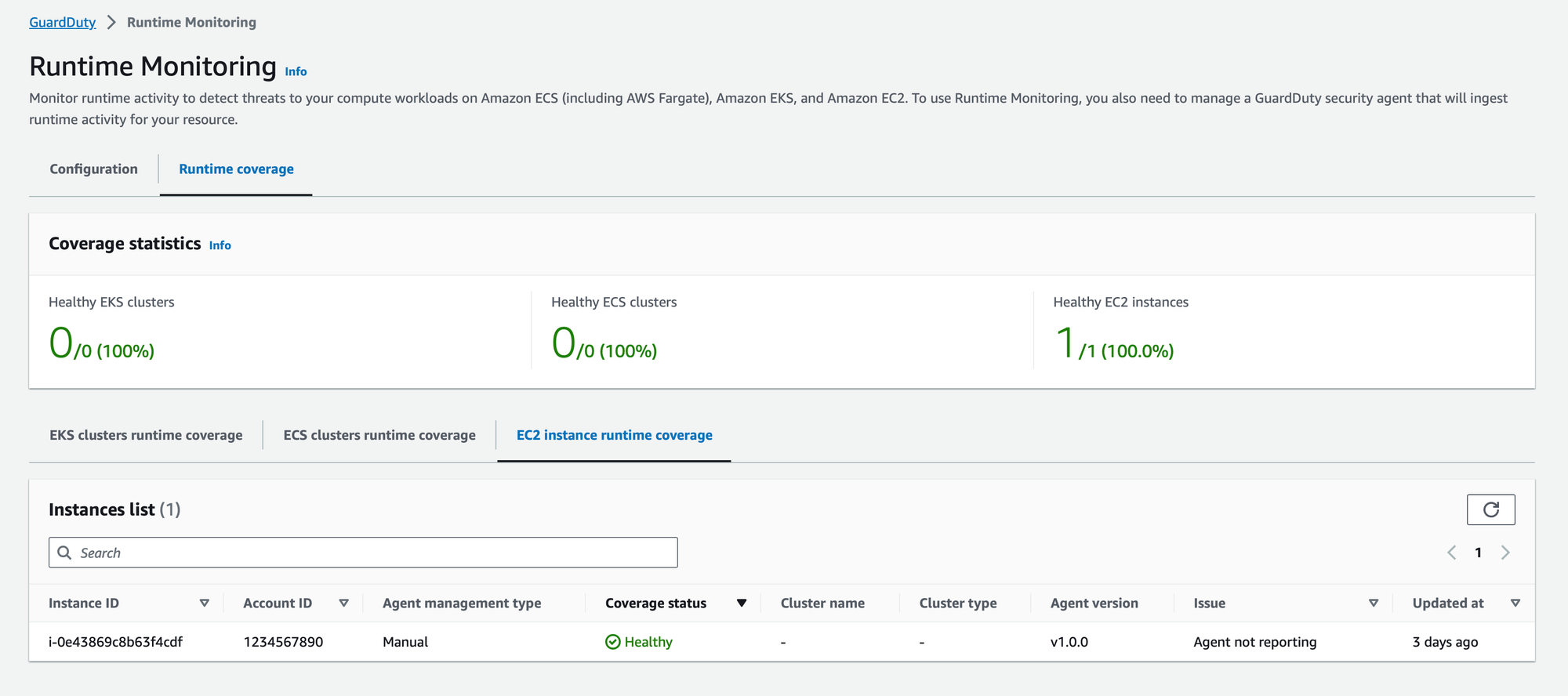
└─3639 /opt/aws/amazon-guardduty-agent/bin/amazon-guardduty-agent --worker-threads 8Alternatively, you can check the status directly from the GuardDuty console. Navigate to "Runtime Monitoring" and then select "Runtime Coverage." Here, you'll find detailed information on the coverage status, ensuring that GuardDuty is effectively monitoring your instances. Regularly monitoring both the console and using the command-line verification step ensures continuous protection and allows you to promptly address any anomalies that may arise.
Conclusion 🎓
Finally, 🎉 the long-awaited feature of AWS GuardDuty's runtime protection for EC2 instances has arrived! It's not just about reacting to threats 🚫 it's about preventing them from taking root in the first place. As we continue our journey into the cloud, having GuardDuty by our side ensures that our cloud environment remains secure, allowing us to focus on innovation and growth. ✨










