Understanding AWS Inspector
Before we dive into the configuration process, it's crucial to understand what AWS Inspector is and why it's essential. 🔍 AWS Inspector is a vulnerability management service that helps you identify vulnerabilities within your AWS resources. 🛡️ It performs automated security scans to identify potential package vulnerabilities or network reachability findings that could compromise the integrity of your cloud infrastructure. 🔒
Configuring AWS Inspector Step by Step
Create IAM role
Let's create a role so the EC2 instance has access to SSM. We can use the AWS managed AmazonSSMManagedInstanceCore policy for that.
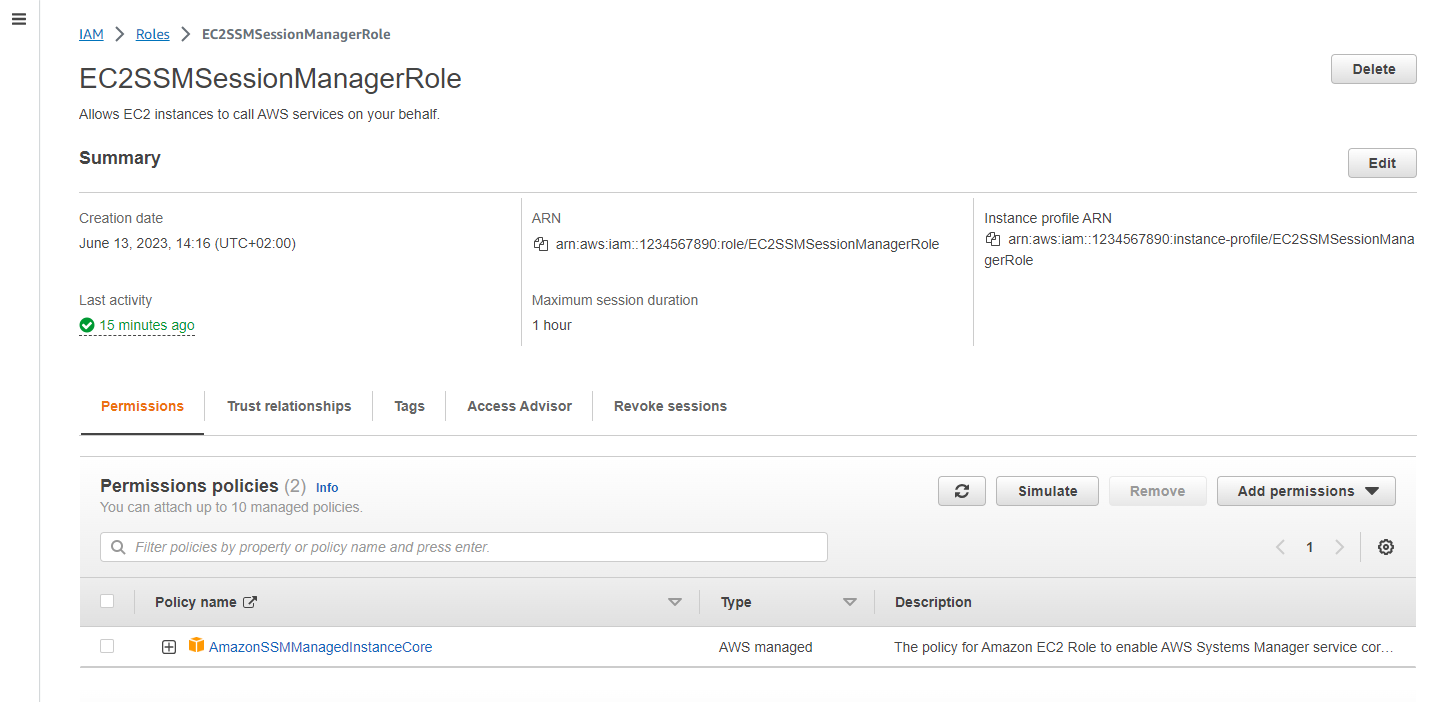
Make sure to create a trust relationship so your EC2 instance can assume the role:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "ec2.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}Install AWS Inspector
AWS Inspector doesn't need to be installed as a separate component on your EC2 instance anymore. It is now part of the AWS Systems Manager (SSM) agent.
I recommend using the EC2 user data to install the AWS SSM agent. The following command installs and enables it automatically (Please adjust the command based on your OS. You can find the right command here):
#!/bin/bash
cd /tmp
sudo yum install -y https://s3.amazonaws.com/ec2-downloads-windows/SSMAgent/latest/linux_amd64/amazon-ssm-agent.rpm
sudo systemctl enable amazon-ssm-agent
sudo systemctl start amazon-ssm-agentPlease make sure you have attached the previously created role to your EC2 instance. Otherwise, you will not receive any alerts in AWS Inspector.
Confirm AWS SSM agent is running
Afterward, you can use SSM Session Manager to connect to your instance. This capability is automatically enabled with the above role. If you want to know more, you can follow my previous article:
Just run sudo systemctl status amazon-ssm-agent to check if the SSM agent is running. The command also depends again on your OS. A full list can be found here.
sh-5.2$ sudo systemctl status amazon-ssm-agent
● amazon-ssm-agent.service - amazon-ssm-agent
Loaded: loaded (/etc/systemd/system/amazon-ssm-agent.service; enabled; preset: enabled)
Active: active (running) since Sat 2023-08-26 18:10:39 UTC; 1h 0min ago
Main PID: 2022 (amazon-ssm-agen)
Tasks: 31 (limit: 1114)
Memory: 114.3M
CPU: 7.782s
CGroup: /system.slice/amazon-ssm-agent.service
├─2022 /usr/bin/amazon-ssm-agent
├─2068 /usr/bin/ssm-agent-worker
├─3633 /usr/bin/ssm-session-worker
└─3645 shInvestigate alerts
We have successfully installed the AWS SSM agent and are ready to check our instance for any vulnerabilities. The agent scans the instance every time any of the following events happens:
- Launching a new EC2 instance.
- Setting up new software on an existing EC2 instance (applicable to Linux exclusively).
- When Amazon Inspector adds a new vulnerability (CVE) to its database, and if it is relevant to your EC2 instance (exclusive to Linux).
Besides package vulnerabilities, AWS Inspector also performs a Network reachability scan for your EC2 instances every 24 hours. This will also be clustered based on the criticality and exploitability of the port on the dashboard.
Give it some time until your findings will flow into the AWS Inspector dashboard.
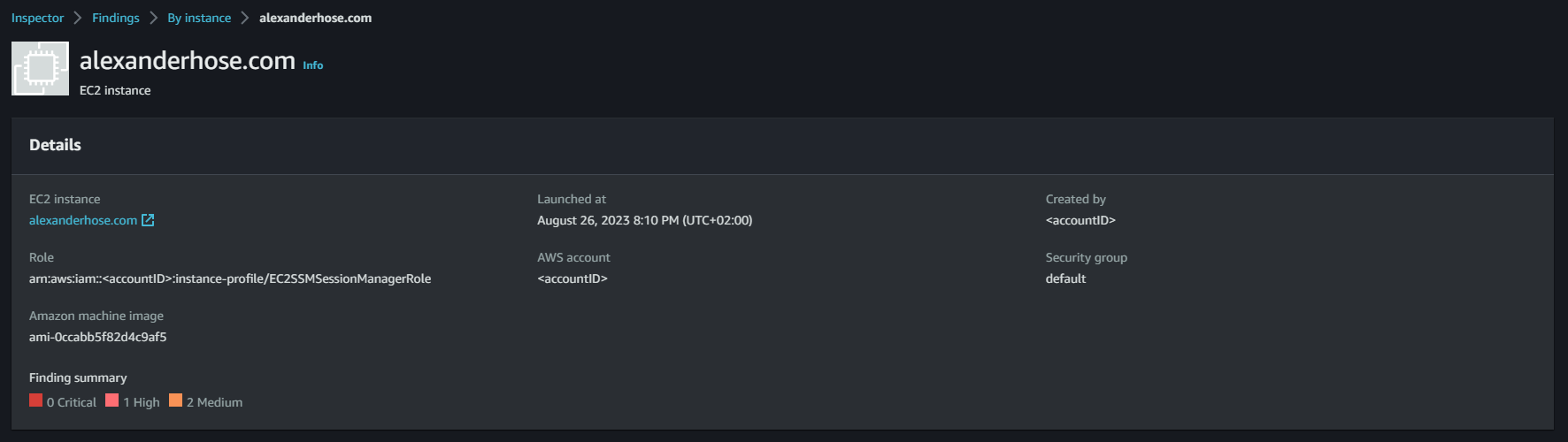
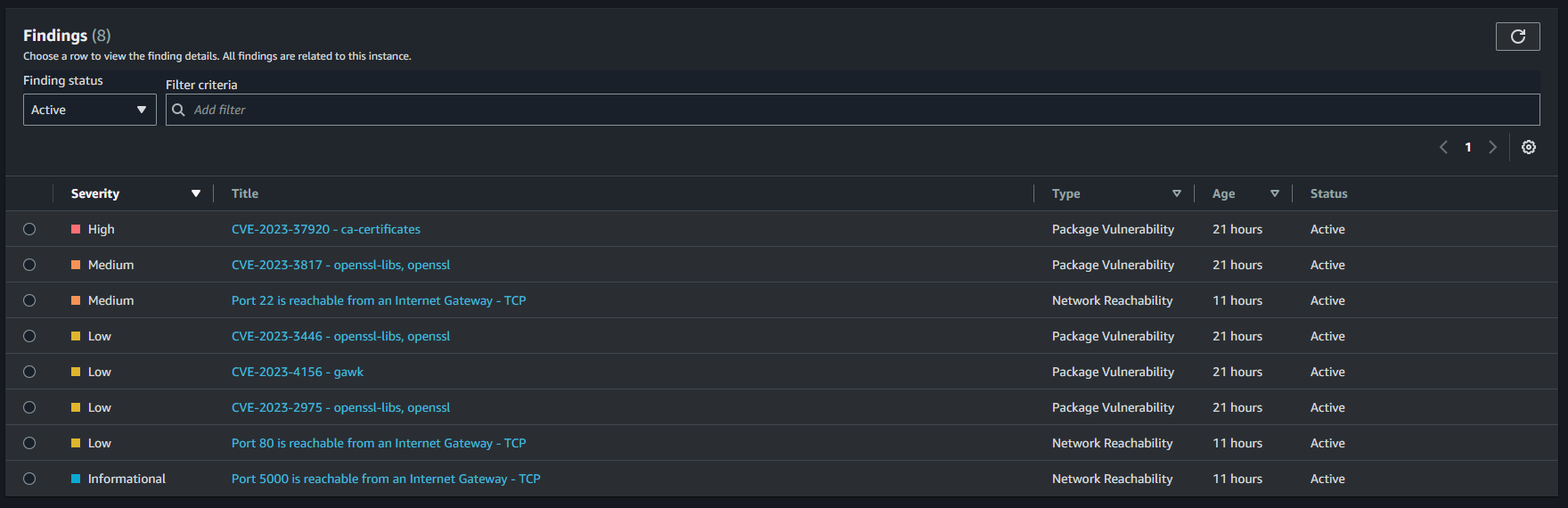
Conclusion 🎓
In conclusion, mastering the art of configuring AWS Inspector for effective vulnerability management is a vital step toward ensuring the security and resilience of your AWS environment. Luckily the setup is straightforward and easy to perform. By following the steps outlined in this guide, you are ready to go.
However, it's essential to note that while AWS Inspector excels at identifying vulnerabilities within your system, it primarily focuses on scrutinizing your setup for weaknesses rather than actively monitoring and thwarting real-time attacks. 🕵️♂️ To achieve comprehensive security, combining AWS Inspector's insights with other security measures such as intrusion detection systems and continuous monitoring is strongly recommended. 🔒 Striking this balance will enable you to protect your AWS resources against both known vulnerabilities and unforeseen threats, safeguarding your assets.





Member discussion