Operating systems are becoming increasingly intricate, demanding meticulous configuration to ensure robust security. Nowhere is this more evident than with EC2 instances, where the operating system is dynamic and subject to change. The challenge lies in securing these instances.
Enter the Center for Internet Security (CIS) Benchmarks - a guidance in the complex world of cloud security. With two distinct levels, Level 1 and Level 2, CIS Benchmarks provide a roadmap for configuring operating systems. As operating systems evolve and configurations become more intricate, CIS Benchmarks offer a structured approach to secure your instances.
Understanding CIS Benchmarks
CIS Benchmarks are industry-standard configuration guidelines crafted to enhance the security of systems and applications. These benchmarks offer a comprehensive set of best practices, strategically designed to strengthen the security level across diverse technologies. Structured in two levels - Level 1 and Level 2 - these benchmarks provide a scalable and adaptable approach to enhancing security across different tech landscapes.
Level 1
Level 1 guidelines focuses on changes that are less likely to disrupt the production functionality of your instance. Think of Level 1 as a foundational layer, offering essential security enhancements without causing major operational disruptions. These recommendations provide a balanced approach to secure your system without introducing significant changes.
Level 2
In contrast, Level 2 guidelines dive into more impactful configurations that may have a substantial impact on your instance's production environment. These recommendations are designed for instances where the security benefits outweigh potential operational disruptions. It's crucial to approach Level 2 changes with caution, implementing them judiciously to strike the right balance between security and operational stability.
CIS Scans in AWS: Essential Prerequisites
There are essential prerequisites to meet for a seamless and effective security assessment.
- Supported Operating Systems:
Ensure that your instance operates on one of the supported operating systems for CIS scans. Supported operating systems include Amazon Linux 2, Amazon Linux 2023, Windows Server 2019, and Windows Server 2022. - Amazon EC2 Systems Manager (SSM) Managed Instance:
Your instance must be managed by Amazon EC2 Systems Manager (SSM). If you haven't set up SSM or need assistance, refer to my detailed blog article that provides a step-by-step guide on SSM installation and utilization for seamless instance management.

- Amazon Inspector Deep Inspection Enabled:
Verify that your instance resides in an AWS account with Amazon Inspector deep inspection enabled. - Instance Profile Permissions:
Set up an instance profile with the necessary permissions for SSM to manage the instance and Amazon Inspector to run CIS scans. To grant these permissions, attach theAmazonSSMManagedInstanceCoreandAmazonInspector2ManagedCispolicypolicies to an IAM role. Attach this role to your instance as an instance profile.
Initiating CIS Scans in AWS Inspector
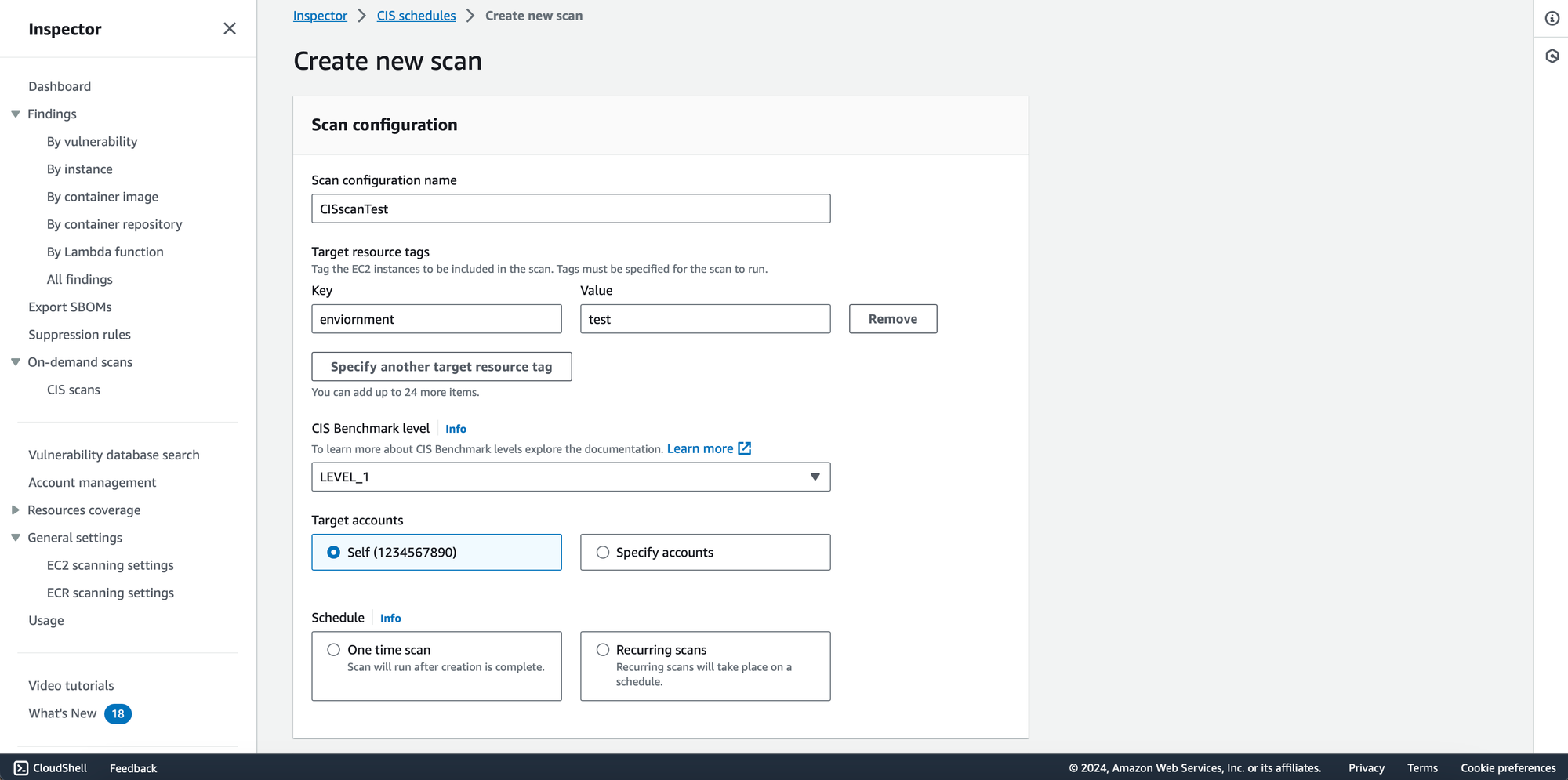
Now that we've laid the groundwork, let's conduct some CIS scans for your EC2 instances using AWS Inspector. Follow these steps to seamlessly initiate the scanning process. In the Inspector console, choose between a one-time scan or a recurring scan based on your specific requirements.
- Define Scan Targets:
Tag your EC2 instances to be included in the scan. Specify relevant tags for the scan to run effectively. Tags help you precisely target the instances you want to assess. - CIS Benchmark Level:
Choose the desired CIS Benchmark level based on your security objectives. You can opt for Level 1 or Level 2, depending on your specific security and compliance needs. - Specify Scan Accounts:
You have the flexibility to specify your AWS account for the scan, or if you're part of an organization, choose multiple accounts within your organization.
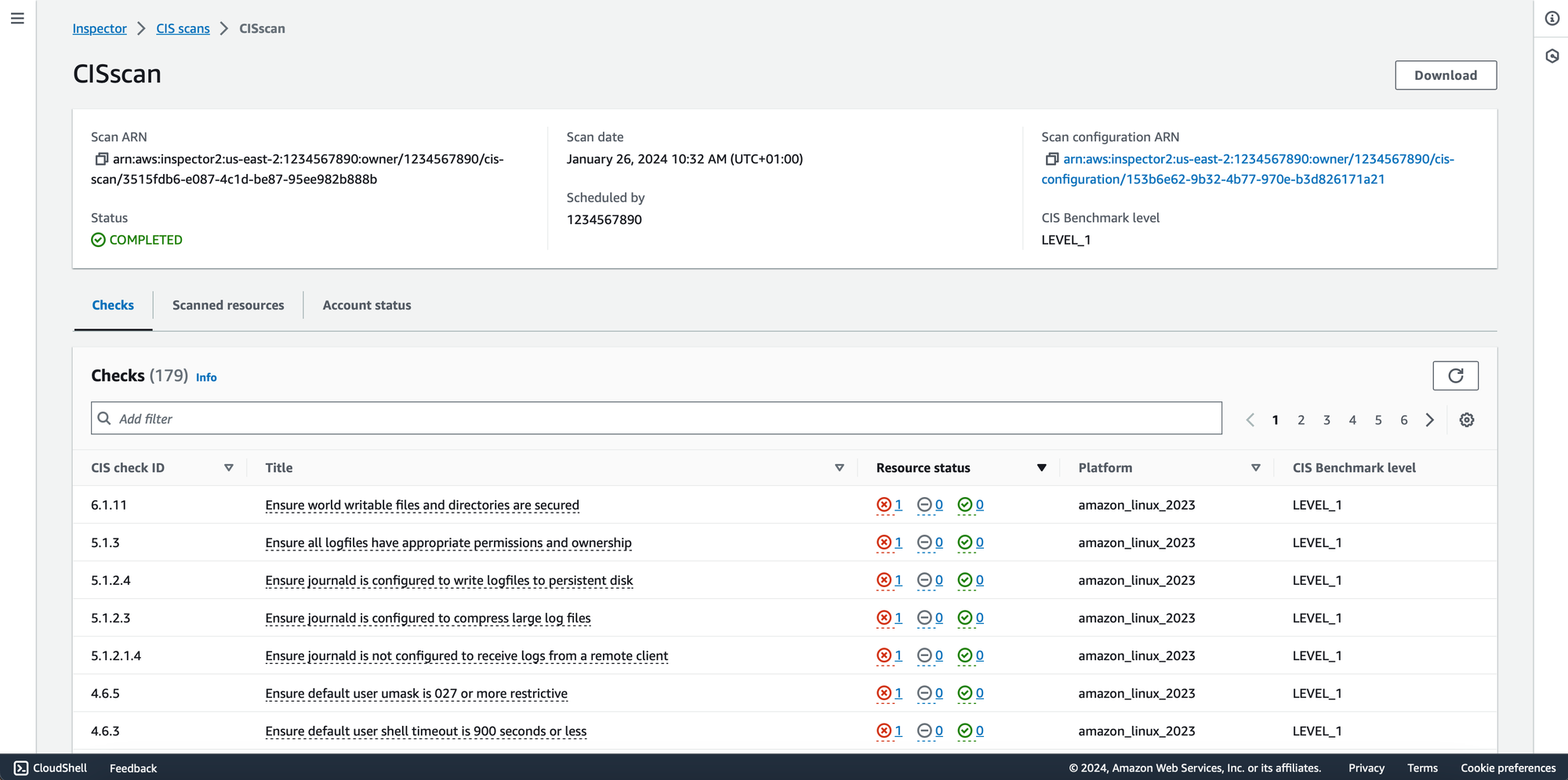
Monitor the scan progress through the Inspector console. AWS Inspector provides real-time updates on the assessment, allowing you to track its status and view detailed findings.
Troubleshooting CIS Scans
Encountering issues with your CIS scans? Here's a quick troubleshooting guide to get you back on track:
Check in SSM:
- Navigate to AWS Systems Manager in the AWS Management Console.
- Review the status of your managed instances within SSM.
- Ensure that the SSM Agent is running and that your instances are successfully communicating with the service.
Inspect State Manager Associations:
- Access State Manager within AWS Systems Manager.
- Verify that all associations required for the CIS scans are applied to your instances.
- If any associations are missing or not applied, consider manually applying them in State Manager to ensure proper configuration.