Introduction
Previously, we dived into the world of GCP VPC Service Controls, gaining insights into how they enhance the security of our cloud infrastructure.

Now, we take our access management strategy to the next level with an in-depth exploration of the GCP Access Context Manager. Building upon the foundation laid by VPC Service Controls, this powerful service empowers us to achieve even greater precision in our access control measures.
Introduction to GCP Access Context Manager 👨🎓
GCP Access Context Manager is a service that enables you to manage access to resources within GCP. It acts as an added layer of security, allowing you to define granular access policies based on various contextual attributes. By utilizing Access Context Manager, you can control who can access specific resources, under what conditions, and from which devices or locations.
Setup GCP Access Context Manager 🧰
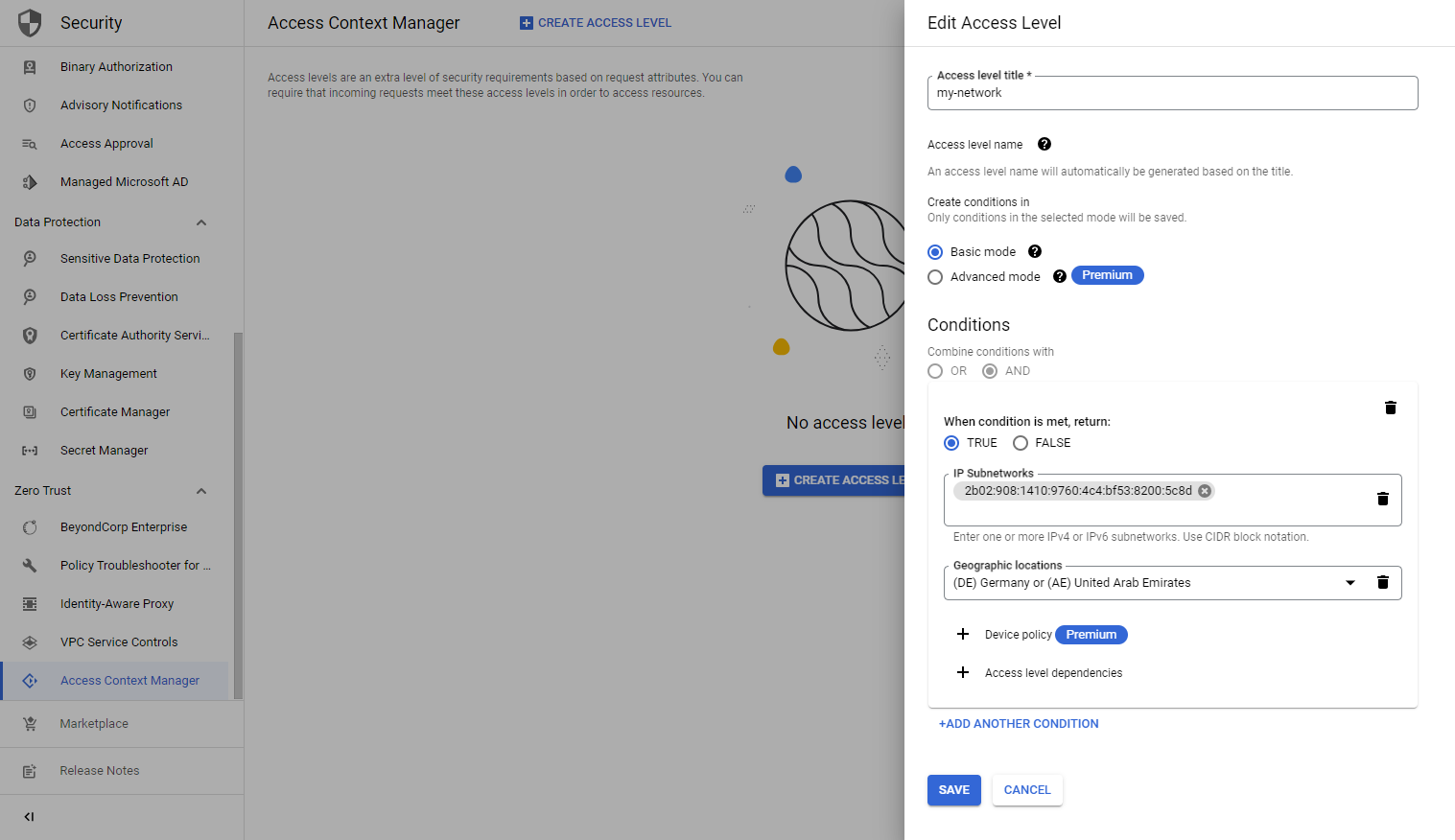
Let's navigate to the GCP Access Context Manager and create a new access level. Here we can choose between basic and advanced modes. The advanced mode utilizes the Common Expression Language (CEL) to create the conditions. The basic mode supports, IP subnetworks, Geographic locations, Device policies, and Access level dependencies. In our example, we want to restrict access to a certain IPv6 subnetwork in the countries of Germany or the United Arab Emirates.
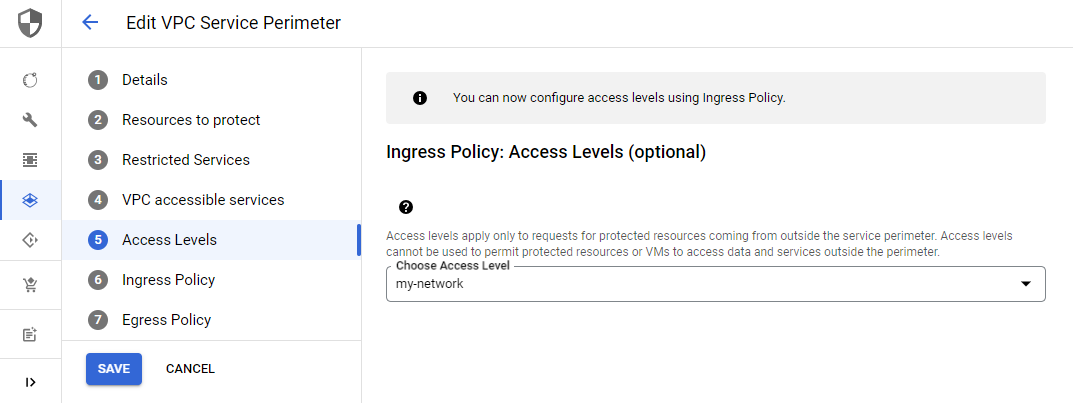
If we want to utilize the access level in our VPC Service Permiter, we need to skip to step 5 in the setup. Here we can choose any of the access levels that we have created.
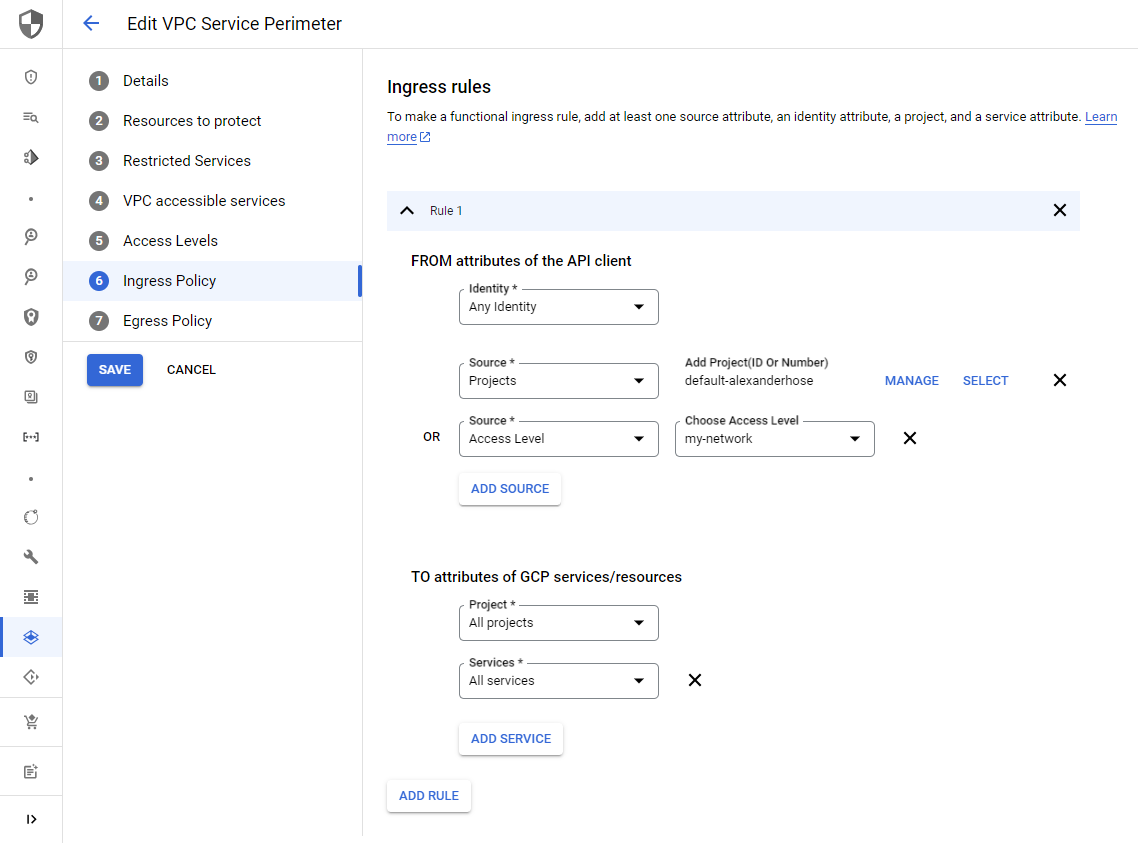
Lastly, ensure that we define the ingress policy in step 6. Here we can choose the access level as the source of the requests.
The generated configuration will look like this:
// Projects (project id)
security-alexanderhose (1234567890)
// VPC Networks
// Services
Cloud Storage API
Ingress Rule 1
From:
Identities: ANY_IDENTITY
Access levels:
accessPolicies/1234567890/accessLevels/my_network
To:
Projects: All projects
Services =
Services name: All services
// No egress policy
// VPC Accessible Services
All services allowed
// Access levels
my-networkConclusion 🎓
By embracing context-based access control, you can mitigate the risks of unauthorized access and potential data breaches from certain countries or devices. The only drawback is that debugging this solution can be quite bothersome and the subnetting is throwing errors regularly. Share your thoughts and challenges in the comment section below.










Member discussion