Introduction
If you love coding and collaborating with others on software projects, chances are you're already familiar with GitHub. But are you sure the code you are writing is secure? 🔐
That's where GitHub Advanced Security comes into play. This article will explore how to use GitHub Advanced Security CodeQL to secure your code against security vulnerabilities. 🕵️♂️
Understanding GitHub Advanced Security 🏰
GitHub Advanced Security is like a virtual fortress for your code. It's a collection of security tools that work seamlessly with your repositories. This suite of security tools arms you with the necessary insights to identify and address potential threats before they become major issues. Think of it as your cybersecurity assistant, constantly scanning your code and offering insights into potential vulnerabilities.
Introducing CodeQL 🔬
Imagine CodeQL as a detective for your codebase. It's a powerful Static Application Security Testing (SAST) tool that scans your code to uncover vulnerabilities. CodeQL reviews your code and identifies potential weaknesses, making it easier for you to eliminate security risks. You can easily manage how often the checks should run and customize the behavior.
Setting Up CodeQL in Your Repository 📦
Begin by integrating CodeQL into your repository. This involves installing the CodeQL extension and configuring it to align with your project's specifications. In our repository, let's navigate to Security and choose Set up code scanning.
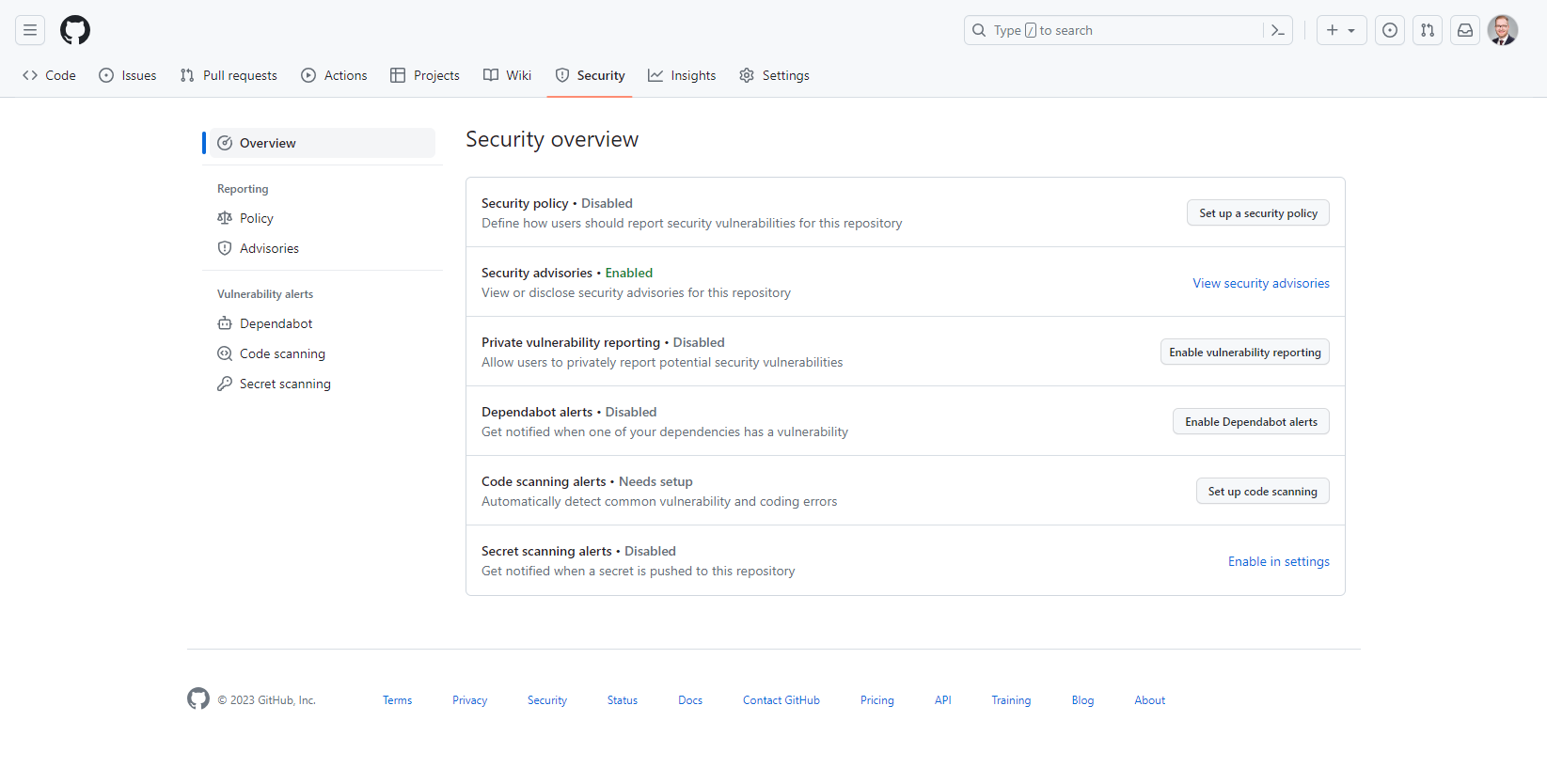
Here we can choose between the Default or Advanced setup. I always recommend advanced, as you have greater control of the configuration.
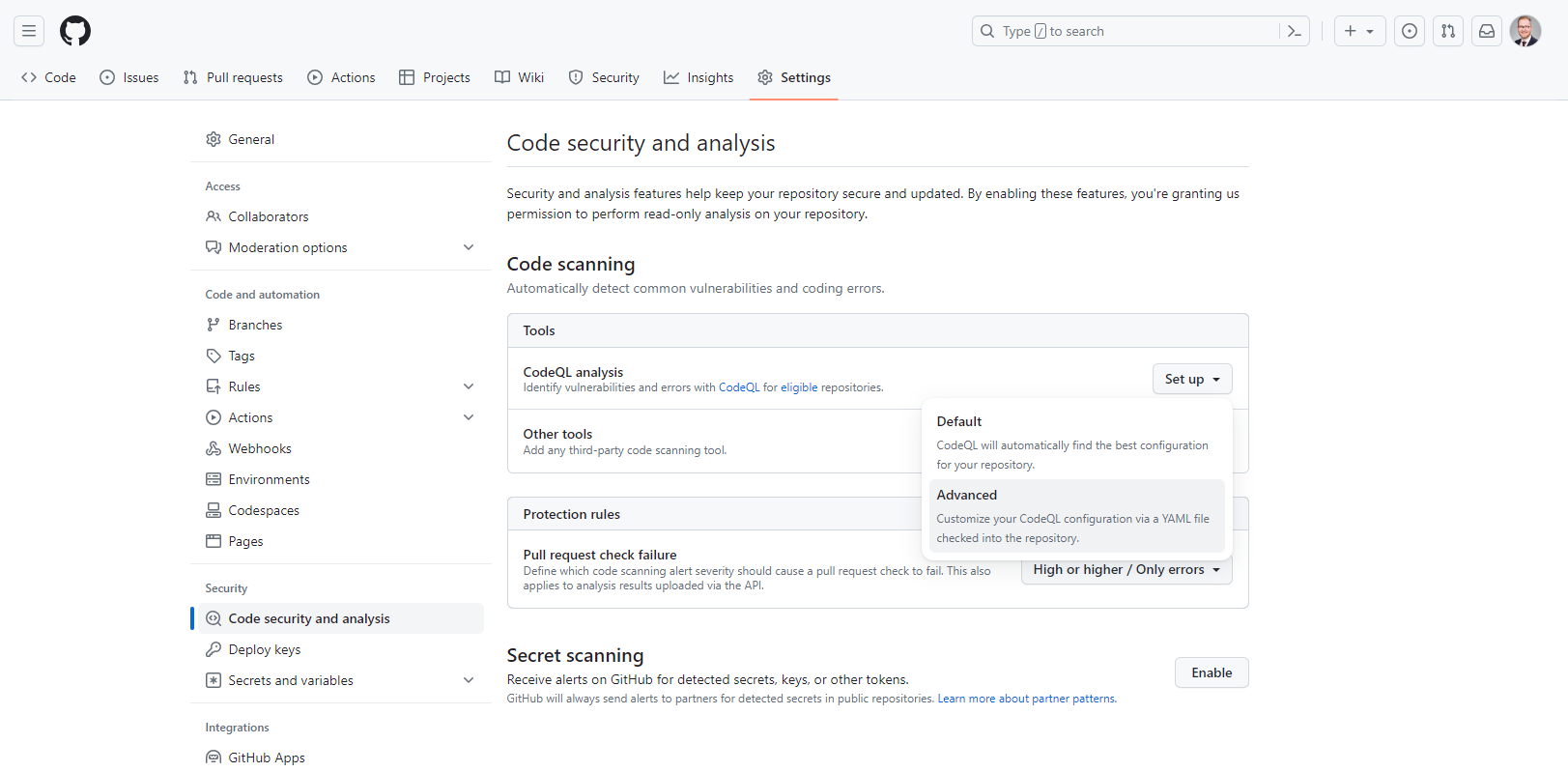
This will automatically create a new folder within .github/workflows. Workflows are defined as YAML files in this directory. They are automated sequences of tasks. Triggered by events like push or pull requests. Each workflow consists of steps that execute actions such as building, testing, and deploying code. In our case, it is checking for vulnerabilities in our code.
We can adjust the configuration to only trigger the action on push on the main branch or also have a schedule for when the action should be run.
An example configuration could look like this:
name: "CodeQL Scan"
on:
push:
branches: [ "main" ]
pull_request:
# The branches below must be a subset of the branches above
branches: [ "main" ]
schedule:
- cron: '17 6 * * 4'
jobs:
analyze:
name: Analyze
runs-on: [ubuntu-latest]
timeout-minutes: 360
permissions:
actions: read
contents: read
security-events: write
strategy:
fail-fast: false
matrix:
language: [ 'python' ]
steps:
- name: Checkout repository
uses: actions/checkout@v3
# Initializes the CodeQL tools for scanning.
- name: Initialize CodeQL
uses: github/codeql-action/init@v2
with:
languages: ${{ matrix.language }}
- name: Autobuild
uses: github/codeql-action/autobuild@v2
- name: Perform CodeQL Analysis
uses: github/codeql-action/analyze@v2
with:
category: "/language:${{matrix.language}}"Analyzing Your Codebase 🔍
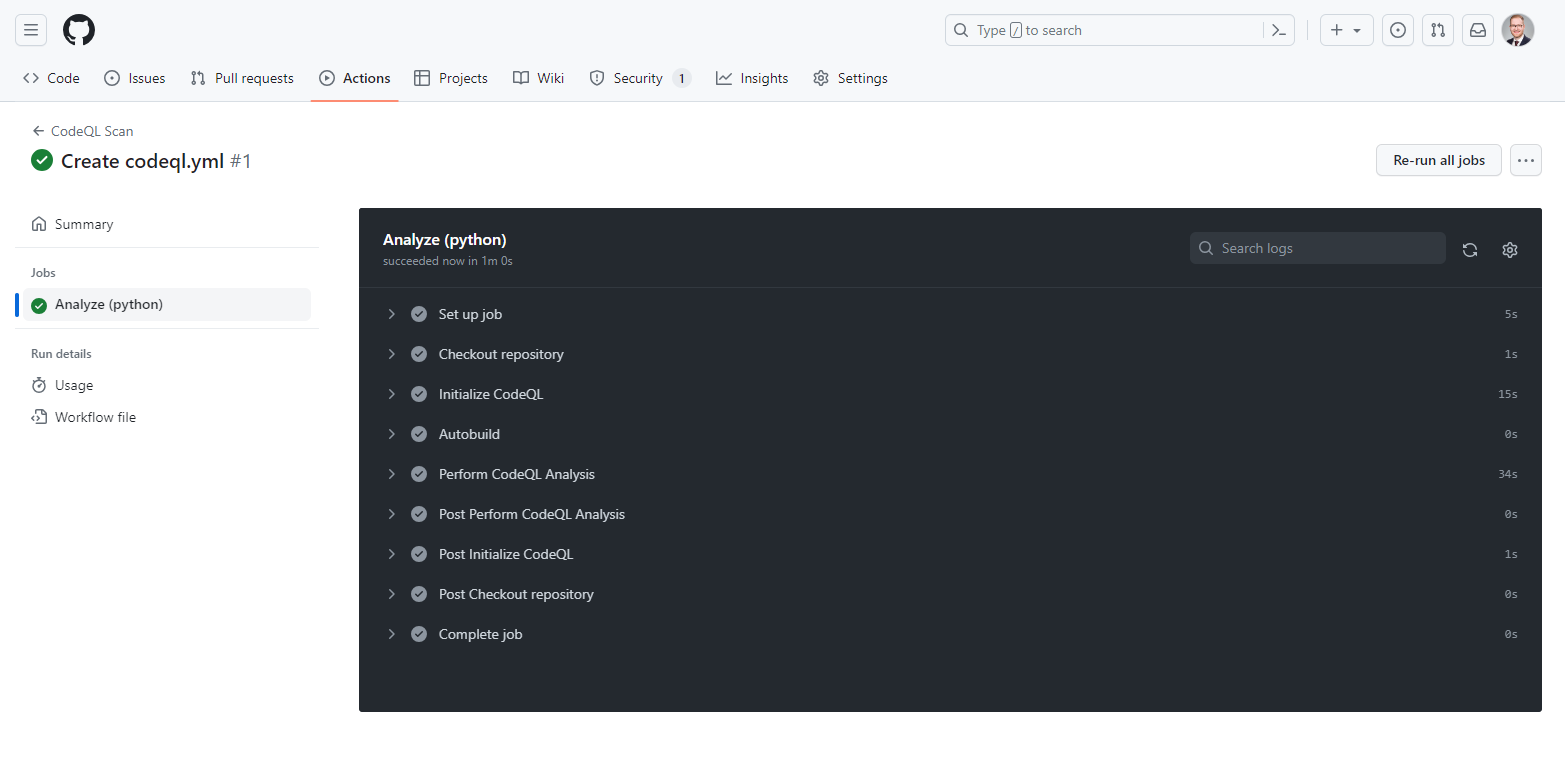
With the GitHub action in place, we can push our code to the main branch and initiate a code analysis. CodeQL will analyze your codebase and identify potential vulnerabilities. In the Action tab, we can check the progress of our GitHub action.
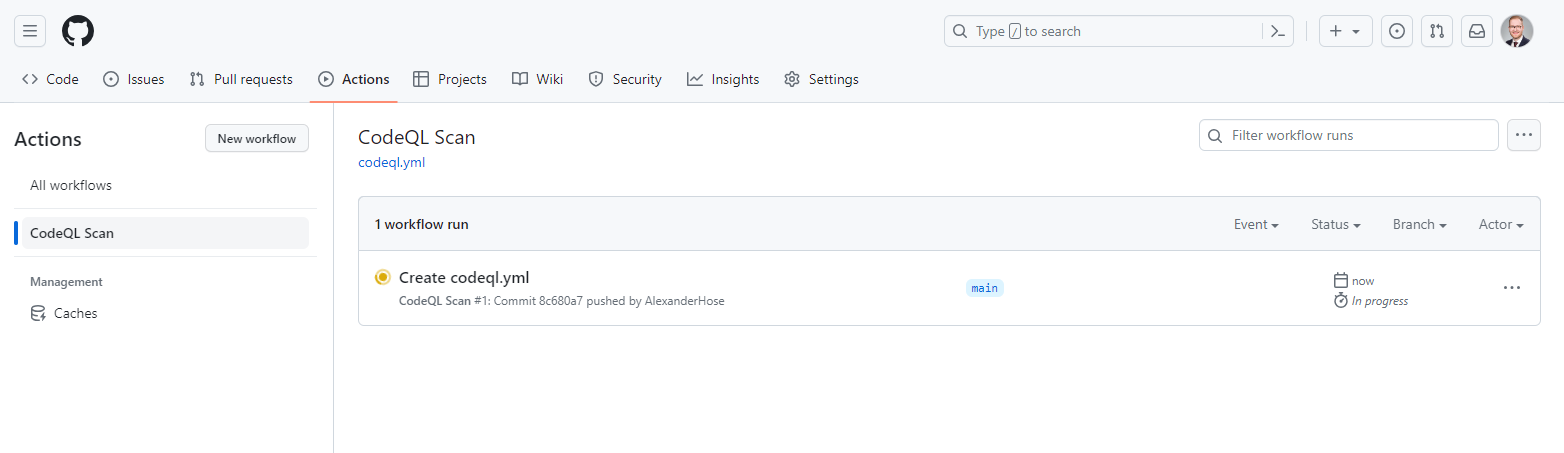
If you select the workflow, you will be able to see the steps from the configuration above.
Interpreting Results and Taking Action 🧠
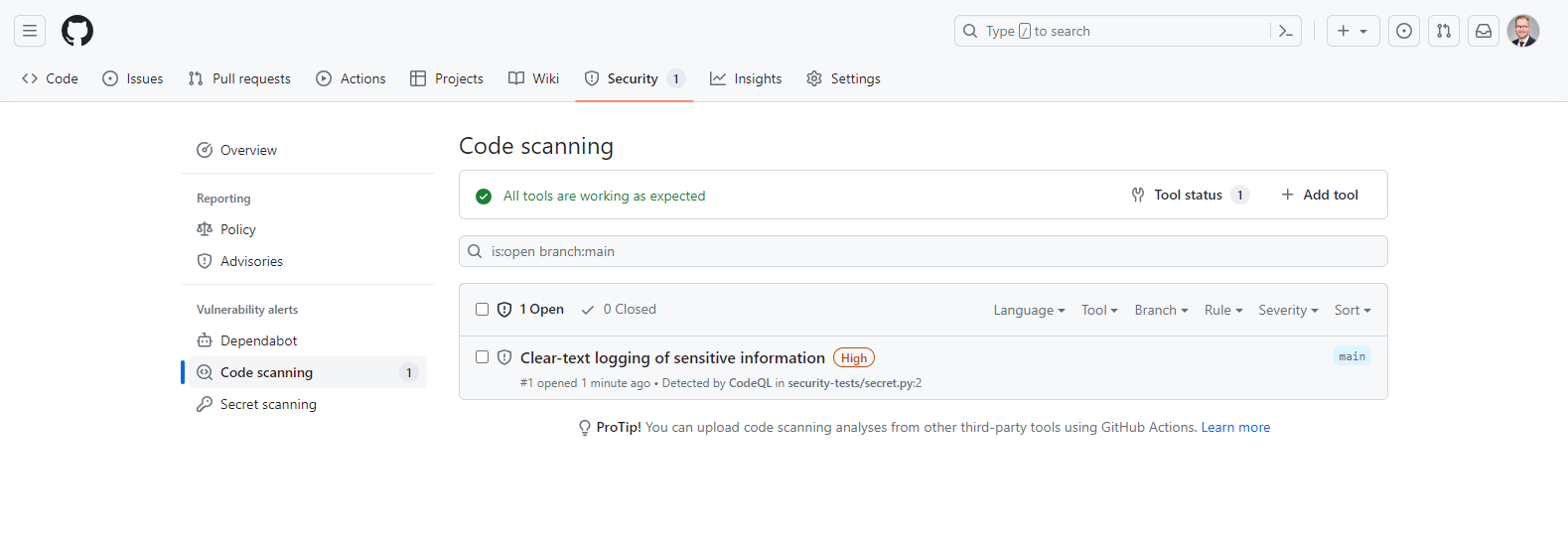
Upon completion of the analysis, CodeQL provides a detailed report outlining the identified vulnerabilities. In the Security tab, you will see an overview of all alerts.
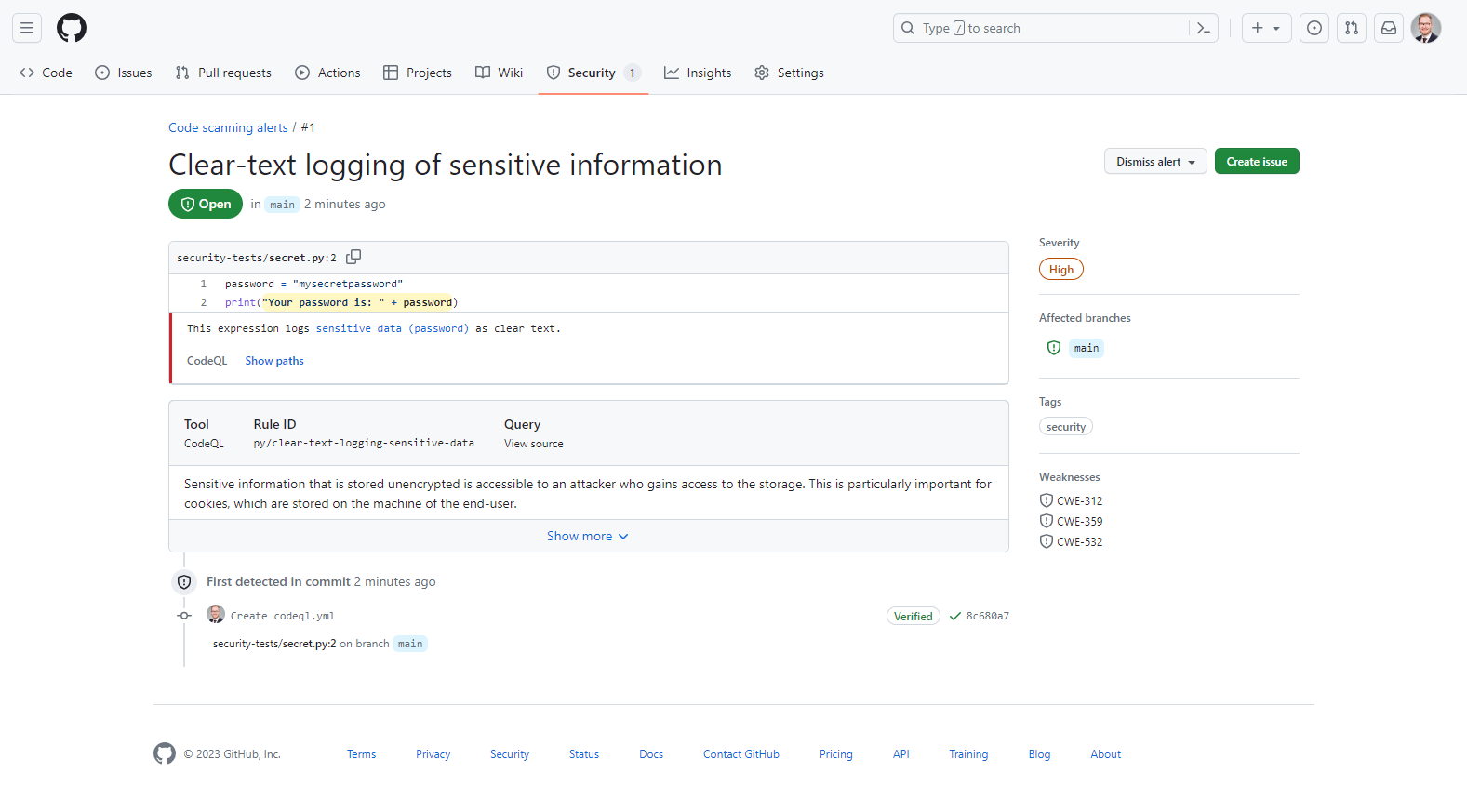
You will be presented with a detailed explanation and CVE references. Prioritize the vulnerabilities based on severity and exploitability, and proceed to rectify them.
Transitioning Toward Enhanced Security 🚀
Transitioning from conventional SAST tools to GitHub CodeQL 🔄 presents a transformative shift in repository security. It seamlessly integrates into your software development process without the overhead of hosting a SAST tool.
The tool's proficiency in uncovering vulnerabilities 🔍 and its adaptability to codebase changes positions it as an indispensable asset in modern software development.
Remember, secure code is the cornerstone of robust software - invest in security today for a resilient tomorrow. 🔐





Member discussion