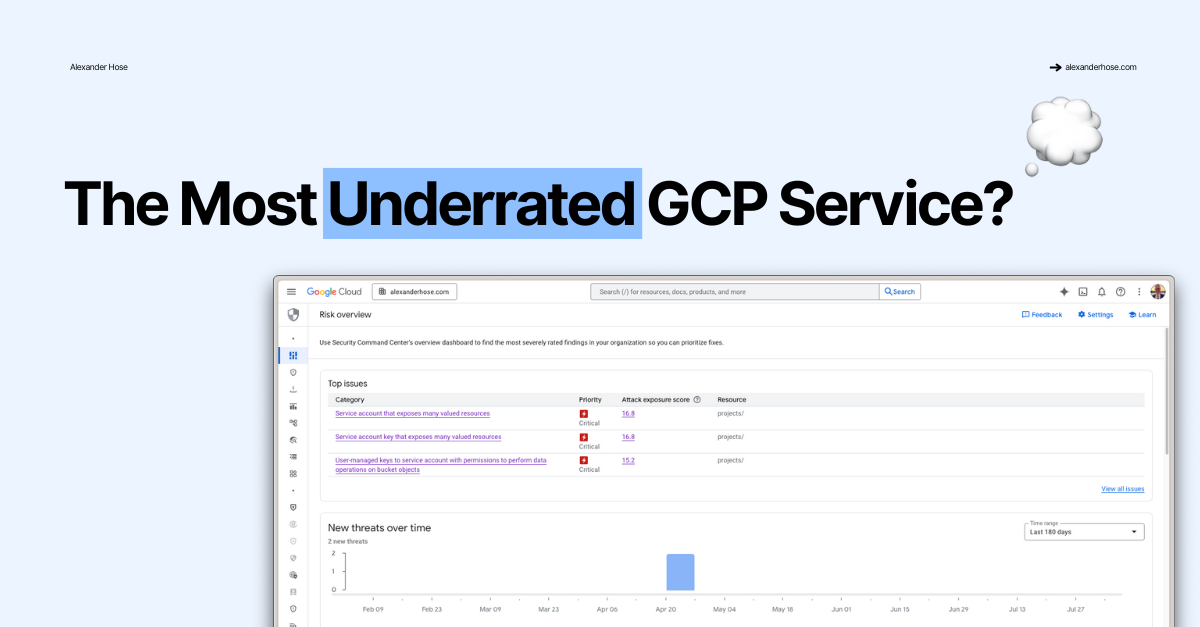
The Most Underrated Service in GCP?
The Most Underrated Service in GCP? It's Not What You Think. In the world of cloud security, we are obsessed with the new, the complex, and the cutting-edge. We talk about advanced threat intelligence feeds, sophisticated eBPF-based runtime security, and AI-powered anomaly detection. But what if the most...