Introduction
GCP Service Accounts are a crucial component of GCP IAM (Identity and Access Management). 🚀 They enable applications/services running on GCP to authenticate themselves and securely access other GCP services. 🔒 Service Accounts are like user accounts but are associated with applications instead of individuals. 🤖
Table of contents
Creating and Managing GCP Service Accounts 🔑
Attach Service Accounts to GCP Service 📚
Conclusion 🎉
Creating and Managing GCP Service Accounts 🔑
To create and manage GCP Service Accounts, navigate to the IAM & Admin section of the Google Cloud Console. From there, you can access the Service Accounts page.
Click on the "Create Service Account" button and provide a name and description for the Service Account.
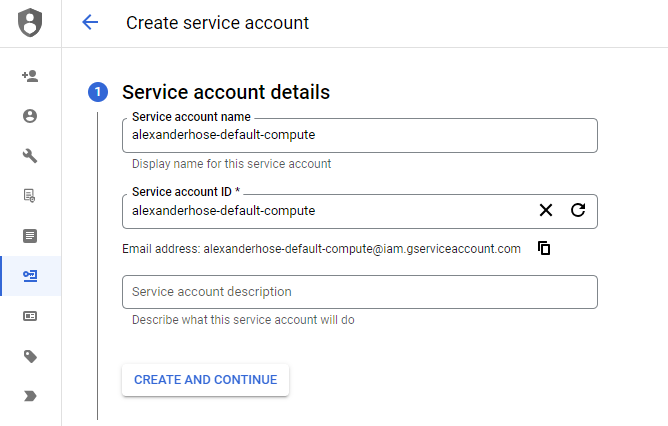
Assign roles to the Service Account based on the level of access it requires. Google Cloud offers a wide range of predefined roles for different services and resources. Select the most appropriate roles for your specific use case.
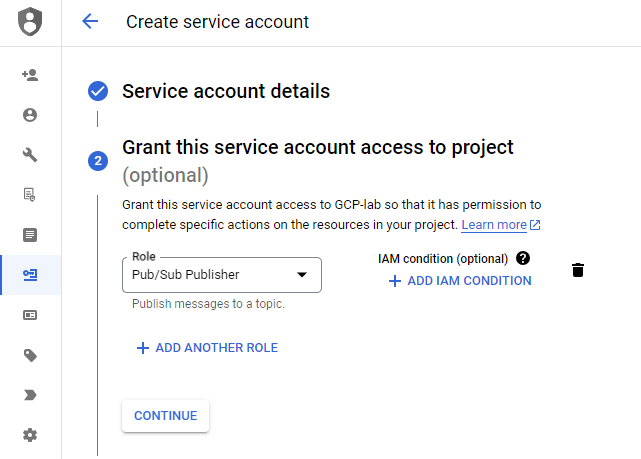
You can skip the third step. If you attach the service account to a GCP service later, you don't require to generate any access keys. The use of service account access keys introduces certain security risks. If these keys are compromised individuals may gain access to sensitive resources and perform malicious actions against your GCP environment.
Attach Service Accounts to GCP Service 📚
You can attach a service account during the creation process of a compute instance or many other services. Simply specify the desired service account in the instance configuration. You can choose the service account in the Identity and API access section of the instance creation.
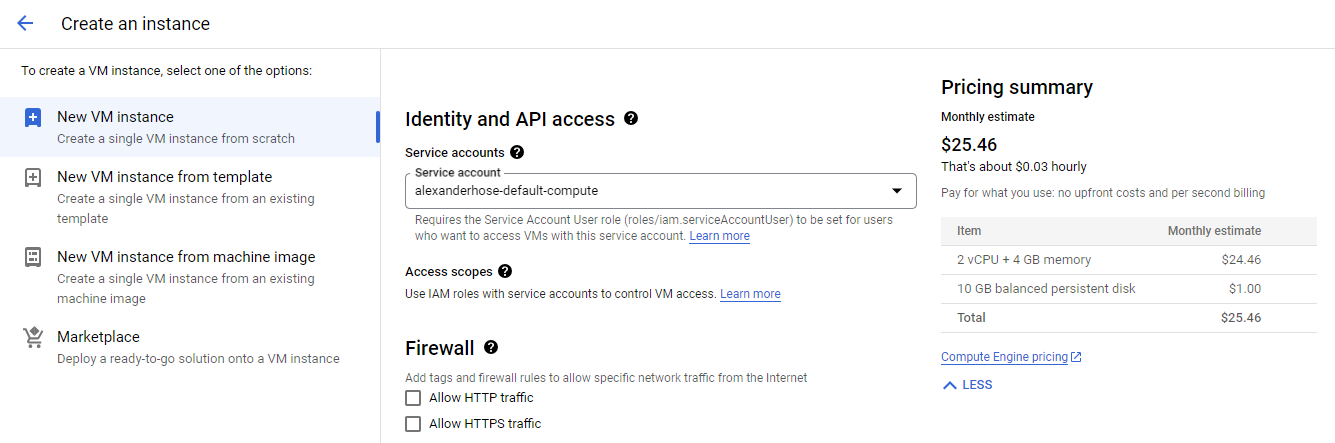
Using the default service account poses potential security risks and should be avoided. 🚫 The default service account typically has broad permissions and is automatically created with new projects. By using the default service account, you increase the attack surface. It is recommended to always create dedicated service accounts with the principle of least privilege tailored to the needs of each application or service.
After the instance is started, it automatically takes the service account for all API calls to other GCP services. You can confirm that if you access the instance and get the gcloud configuration.
alexanderhose@instance:~$ gcloud config list
[core]
account = alexanderhose-default-compute@alexanderhose-gcp-1234567890.iam.gserviceaccount.com
disable_usage_reporting = True
project = alexanderhose-gcp-1234567890You can also use the metadata service and retrieve the token of the service account:
alexanderhose@instance:~$ curl -H "Metadata-Flavor: Google" http://metadata.google.internal/computeMetadata/v1/instance/service-accounts/[email protected]/token
{"access_token":"...","expires_in":3532,"token_type":"Bearer"}Conclusion 🎉
In conclusion, mastering GCP Service Accounts is essential for achieving secure and efficient access management. By leveraging service accounts, you can ensure that applications authenticate themselves and access other resources securely. 🛡️
Following the principle of least privilege is very important here. This means granting service accounts only the necessary permissions required to perform their intended tasks. Minimizing the risk of unauthorized access and potential security breaches. This proactive approach enhances the security posture of your cloud environment. 🔐
Remember to stay updated with the latest best practices and continuously review and audit the permissions assigned to service accounts.







Member discussion