Introduction
AWS Security Hub is a powerful security monitoring and management tool that provides a comprehensive view of your organization's security posture. One of the key features of Security Hub is to centralize alerts and findings from different AWS services like GuardDuty and Amazon Macie.
In this blog post, we will explore the benefits of integrating AWS Security Hub with Slack, and how to set up this integration for your organization. By integrating Security Hub and Slack, you can ensure that your security team has the information they need to quickly identify and respond to potential security threats, helping to keep your organization's data and systems safe from malicious actors.
Whether you are new to AWS Security Hub or an experienced user, this blog post will provide valuable information on how to take advantage of the integration with Slack to improve your organization's security posture.
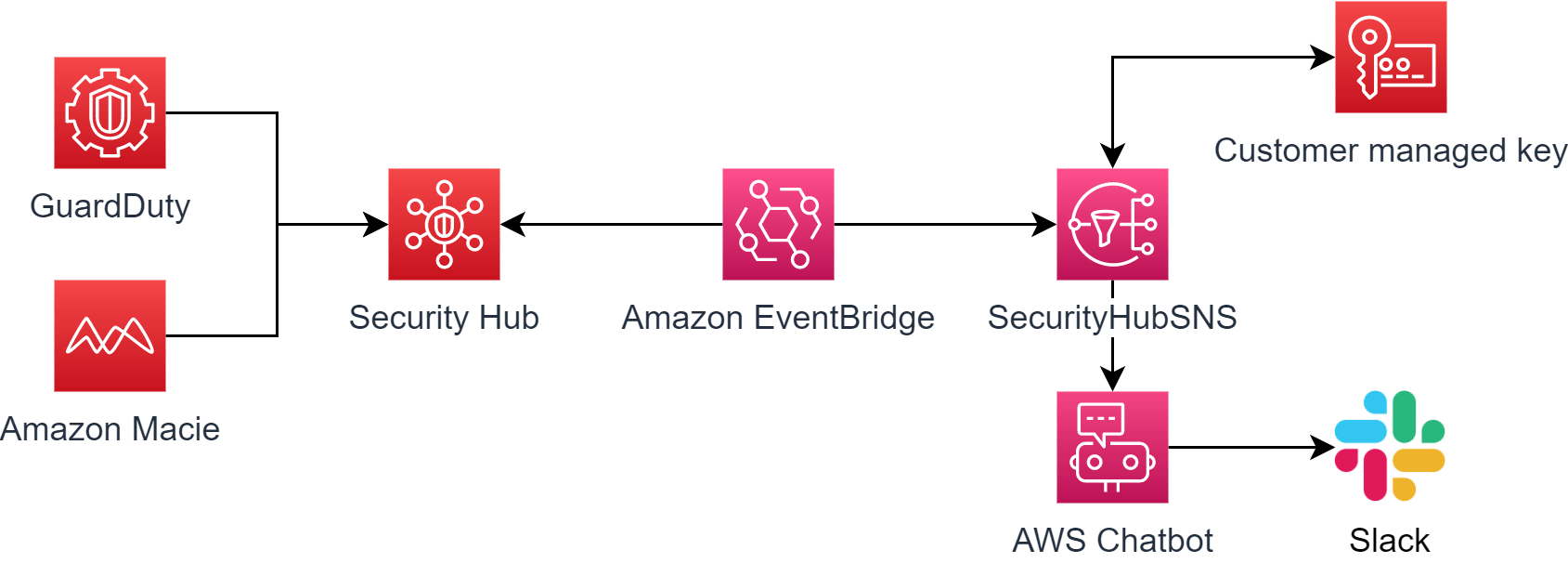
Table of Contents
🧾 Pre-requisites
👨💻 Setup
🔑 Create customer-managed key (CMK)
📥 Create SecurityHubSNS topic
🔔 Integrating Security Hub with Amazon EventBridge
💻 Create a new Slack AWS Chatbot
📨 Receiving Slack messages for Security Hub findings
💭 Conclusion
🧾 Pre-requisites
We need to aggregate alerts and findings of GuardDuty and Amazon Macie in the Security Hub. We can activate that in the settings section of each service.
👨💻 Setup
🔑 Create customer-managed key (CMK)
First, we need to create a new AWS Key Management Service (KMS) CMK. The key requires to have the following policy attached. This way Amazon EventBridge can later access the key.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Enable IAM User Permissions",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::<accountID>:root"
},
"Action": "kms:*",
"Resource": "*"
},
{
"Sid": "Allow EventBridge to use the key",
"Effect": "Allow",
"Principal": {
"Service": "events.amazonaws.com"
},
"Action": [
"kms:Decrypt",
"kms:GenerateDataKey"
],
"Resource": "*"
}
]
}📥 Create SecurityHubSNS topic
Afterward, we created a new SNS topic to retrieve the Security Hub alerts. Name the topic SecurityHubSNS and choose the newly created CMK. The SNS topic should have the following policy attached
{
"Version": "2008-10-17",
"Statement": [
{
"Sid": "default",
"Effect": "Allow",
"Principal": {
"AWS": "*"
},
"Action": [
"SNS:GetTopicAttributes",
"SNS:SetTopicAttributes",
"SNS:AddPermission",
"SNS:RemovePermission",
"SNS:DeleteTopic",
"SNS:Subscribe",
"SNS:ListSubscriptionsByTopic",
"SNS:Publish"
],
"Resource": "arn:aws:sns:<region>:<accountID>:SecurityHubSNS",
"Condition": {
"StringEquals": {
"AWS:SourceOwner": "<accountID>"
}
}
},
{
"Sid": "AWSEvents_SlackDeliveryRule",
"Effect": "Allow",
"Principal": {
"Service": "events.amazonaws.com"
},
"Action": "sns:Publish",
"Resource": "arn:aws:sns:<region>:<accountID>:SecurityHubSNS"
}
]
}🔔 Integrating Security Hub with Amazon EventBridge
By integrating Security Hub with EventBridge, you can enable Security Hub to send alerts and notifications to your EventBridge event bus, which can then be used to trigger various actions such as sending an email, triggering a Lambda function, or invoking an AWS Step Function. In our case, we want to send those alerts to the newly created SNS topic. In the rules section of EventBridge, we will create a new rule with the name SlackDeliveryRule. In the event pattern section, we will customize which findings we want to receive in Slack. In my case, I want to receive findings, with the severity label medium, high or critical.
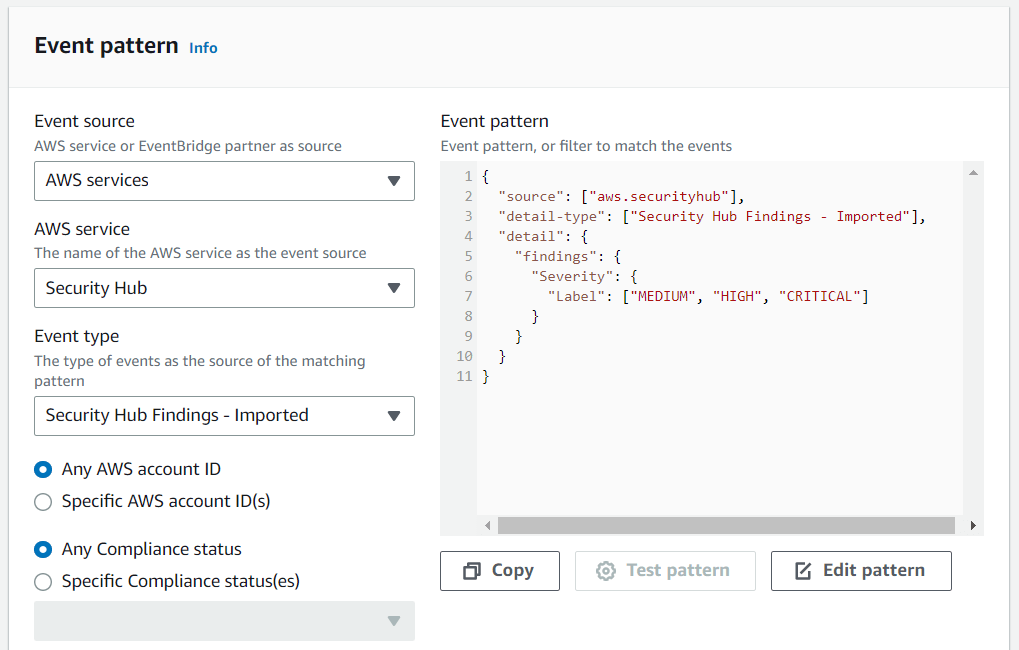
{
"source": ["aws.securityhub"],
"detail-type": ["Security Hub Findings - Imported"],
"detail": {
"findings": {
"Severity": {
"Label": ["MEDIUM", "HIGH", "CRITICAL"]
}
}
}
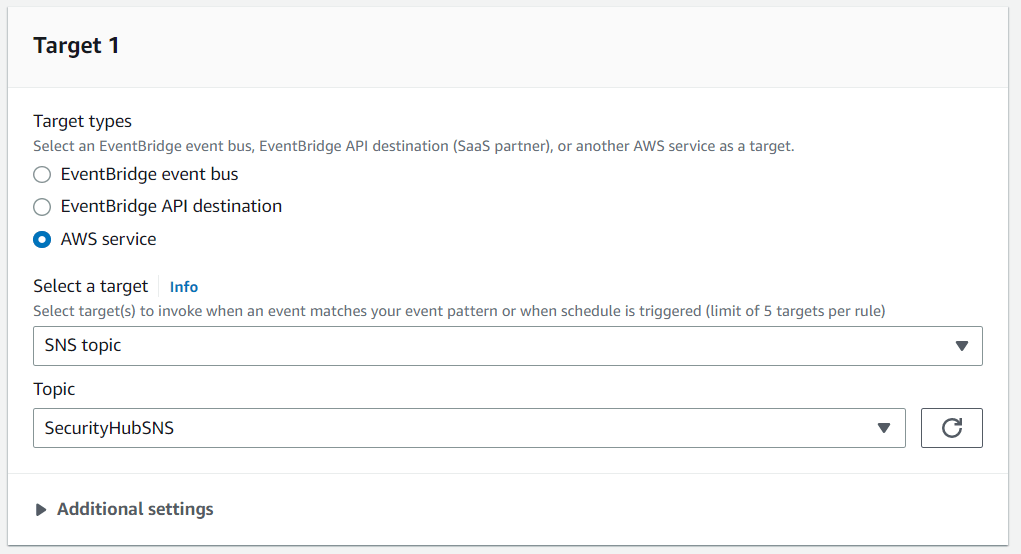
}In the next step, we need to choose the target of this rule. As AWS Chatbot will read an SNS topic, we need to choose the SecurityHubSNS topic that we created earlier.
💻 Create a new Slack AWS Chatbot
First, we need to create a new Slack workspace by navigating to AWS Chatbot and confirming the permission AWS needs on your channel.
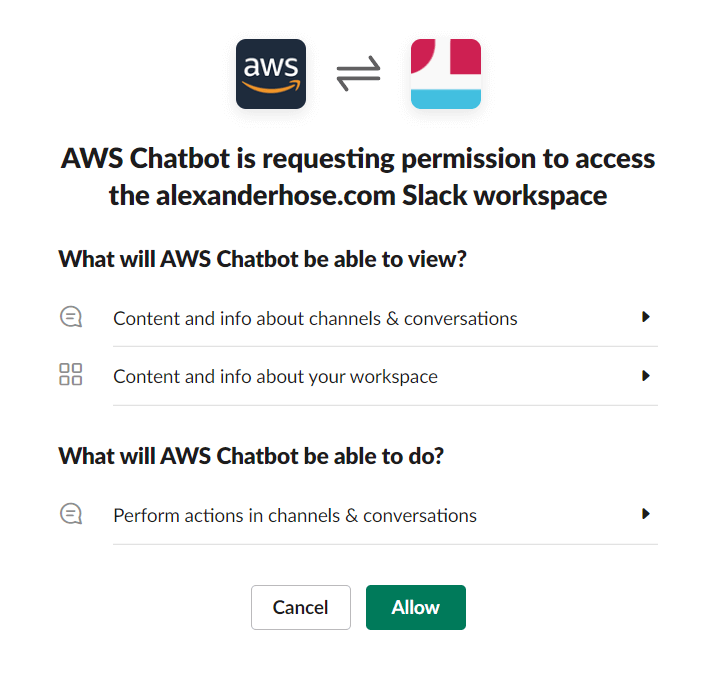
Once you've authorized AWS to access your Slack workspace, you can configure the new slack channel on AWS Chatbot and select the specific channel where you want your chatbot to be active.
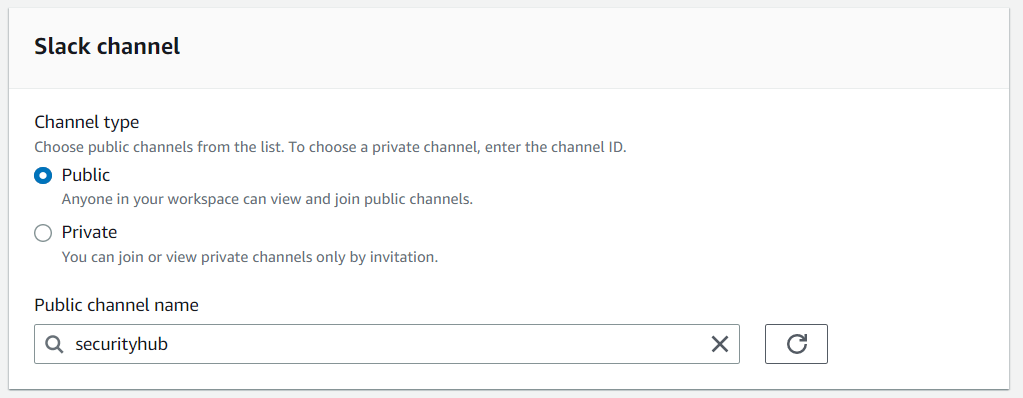
Assigning a role is mandatory and could fail sometimes. That's why I created a role via the IAM console and attached it, instead of generating it directly from the chatbot console. Choose the appropriate policies like AWSChatbotServiceLinkedRolePolicy. Make sure that the role has a trust relationship with AWS Chatbot.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "",
"Effect": "Allow",
"Principal": {
"Service": "chatbot.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}As I don't want the chatbot to perform any actions, the configuration for the policies and guardrails does not matter.
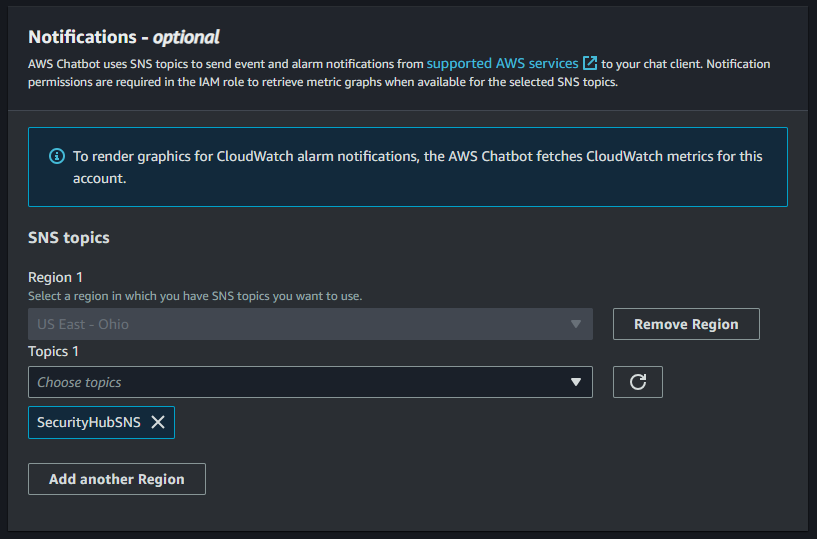
Lastly, I chose the newly created SNS topic in the Notifications section. AWS Chatbot uses this topic to deliver notifications to the configured chat room.

Join our community of cloud security professionals. 🔐
Subscribe to our newsletter📨 Receiving Slack messages for Security Hub findings
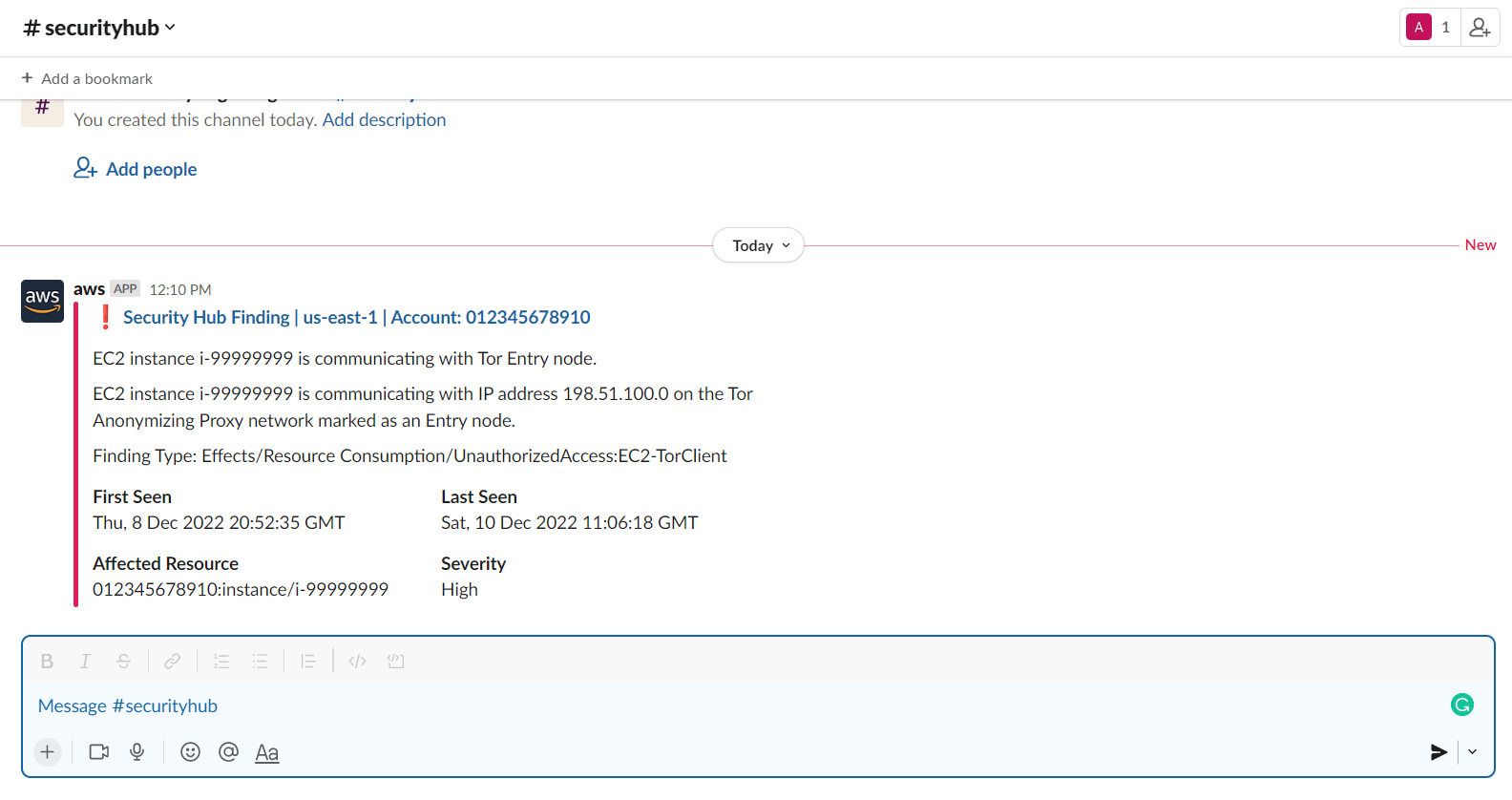
To test the setup you can generate a GuardDuty finding
$ aws guardduty create-sample-findings --detector-id <detectorID> --finding-types UnauthorizedAccess:EC2/TorClientAfter a period, you should see the first alerts on Slack.
💭 Conclusion
In conclusion, integrating AWS Security Hub with Slack allows for real-time security alerts and notifications to be delivered directly to your Slack workspace. This integration can help improve response time to security incidents and streamline communication between team members. Overall, integrating Security Hub with Slack can be a valuable addition to any organization's security strategy. Ensure to configure the EventBridge rule properly otherwise, you will be overwhelmed by all the alerts that the Security Hub aggregates.






Member discussion