AWS Network Firewall is a fully-managed firewall service offered by Amazon Web Services (AWS) that provides network-level protection for Amazon Virtual Private Clouds (VPCs). It is designed to protect against network-level threats and provide an additional layer of security for your AWS environment.
AWS recently announced a new feature to reject TCP traffic for stateful rules. Previously, it was only possible to use pass, drop, or alert actions. In comparison to the drop action, the firewall can now send a TCP reset (RST) for the rejection. The drop action sends no response to the source sender. This made it harder to debug any dropped connections because sessions remained open until the time-to-live threshold was exceeded.
To set up the firewall, we need to create a new stateful rule group.
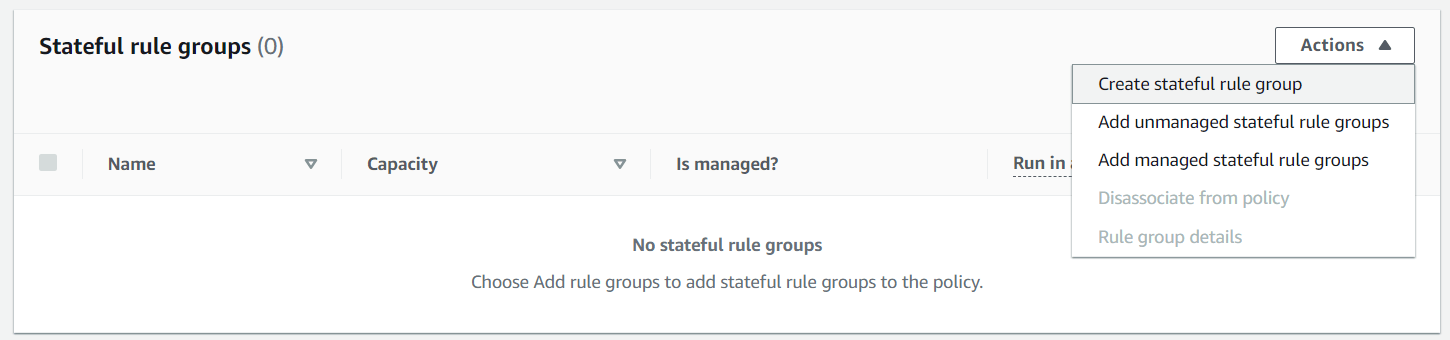
We must choose TCP as the protocol, as the reject action is only available for TCP. Once the rule is set up, if a connection is attempted to a server in a subnet protected by the Network Firewall, the connection will be refused and the packet will be sent to the originator with a TCP reset (RST). This provides assurance that the traffic is being blocked and that no connections to the protected subnet can be made.
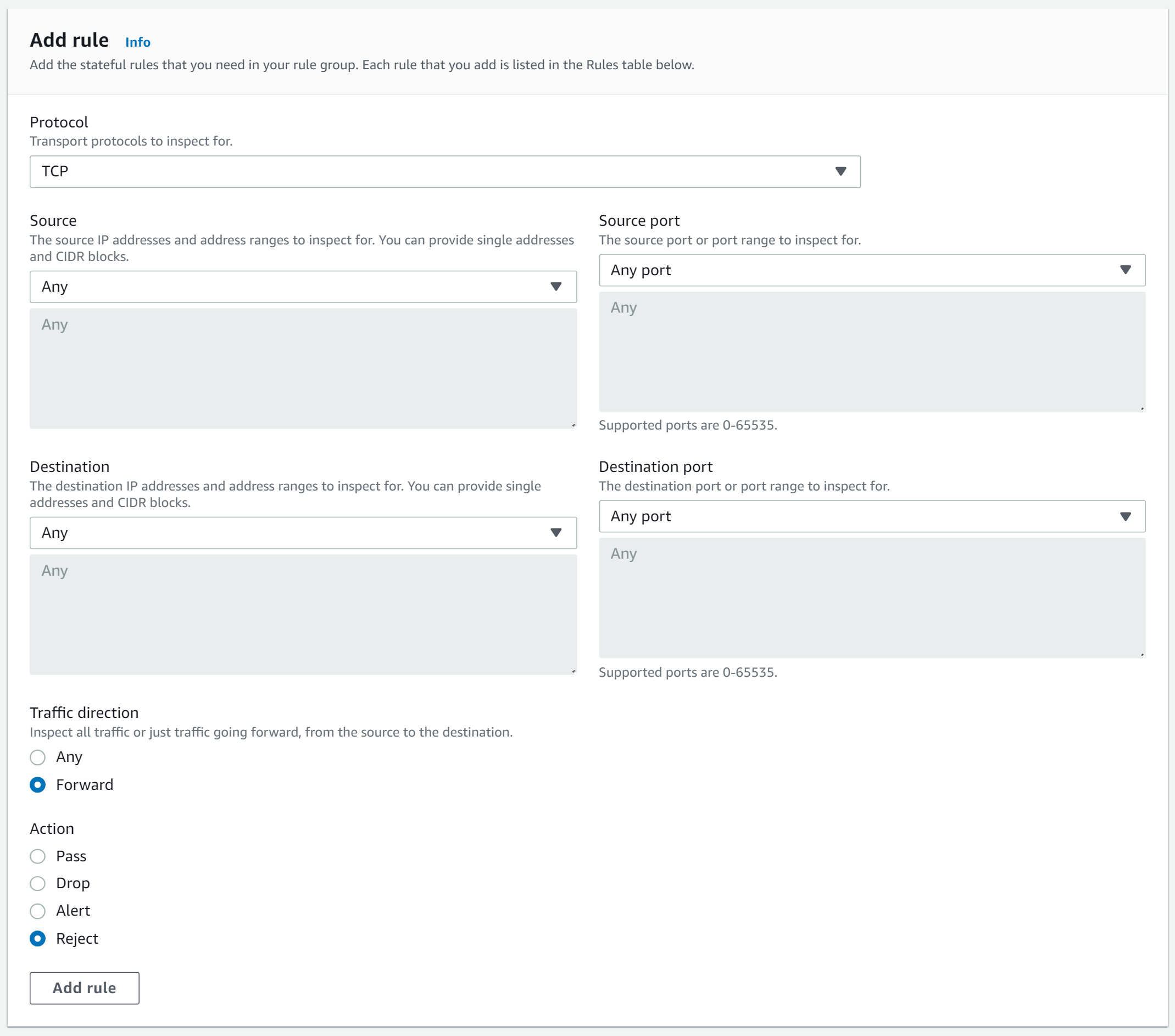
The network firewall provides a unique level of protection for AWS users, as it offers an additional layer of security for the AWS environment. It allows for the rejection of traffic based on stateful rules and provides the assurance that any attempted connection to the protected subnet will be refused.
alexanderhose:~/ $ curl -k -s -v <server>
* Trying <ip>:80...
* connect to <ip> port 80 failed: Connection refused
* Failed to connect to <server> port 80 after 4 ms: Connection refused
* Closing connection 0







Member discussion