AWS Network Firewall is a fully-managed service offered by Amazon Web Services (AWS). It provides network-level protection for Amazon Virtual Private Clouds (VPCs), granting an extra layer of security to your AWS environment and protecting against network-level threats.
This article provides a comprehensive overview of AWS Network Firewall and its features, benefits, and uses. Afterward, we deploy and configure a firewall.
Table of content
What is an AWS Network Firewall?
AWS Network Firewall vs Network ACL
AWS Network Firewall vs Security Group
Setup AWS Network Firewall
🔨 Prerequisites
🔥 Create Firewall
📑 Configure Route Tables
🚨 Create Firewall Policies
What is an AWS Network Firewall?
AWS Network Firewall is a fully-managed firewall service that provides network-level protection for VPCs. Features and capabilities of AWS Network Firewall:
- AWS Network Firewall is a fully managed service.
- AWS Network Firewall blocks malicious traffic before it reaches your applications.
- AWS Network Firewall works with Suricata rule syntax.
- Low-reputation domains or threat signatures can be identified by adding AWS-managed rules.
- You can create and manage firewall rules using AWS Firewall Manager for your organization.
AWS Network Firewall vs Network ACL
Network Access Control List (NACL) is a feature of VPCs that acts as a firewall for controlling traffic in and out of one or more subnets. Network ACLs are stateless. That means traffic must be explicitly allowed in both the inbound and outbound directions.
Differences between AWS Network Firewall and Network ACL:
- Level of protection: Network ACLs provide subnet-level protection.
- Scalability: Network ACLs are associated with a single subnet.
- Statelessness: Inbound and outbound traffic needs to be allowed separately.
AWS Network Firewall vs Security Group
Security groups act as virtual firewalls for controlling traffic. Security groups provide a stateful firewall that controls incoming and outgoing traffic.
Differences between AWS Network Firewall and Security Group:
- Level of protection: Security groups provide instance-level protection.
- Scalability: Security groups are associated with individual workloads.
- Statefulness: Return traffic is automatically allowed for established connections.
Setup AWS Network Firewall
Now we have covered the basics of the AWS Network Firewall. Let's dive into a sample setup.
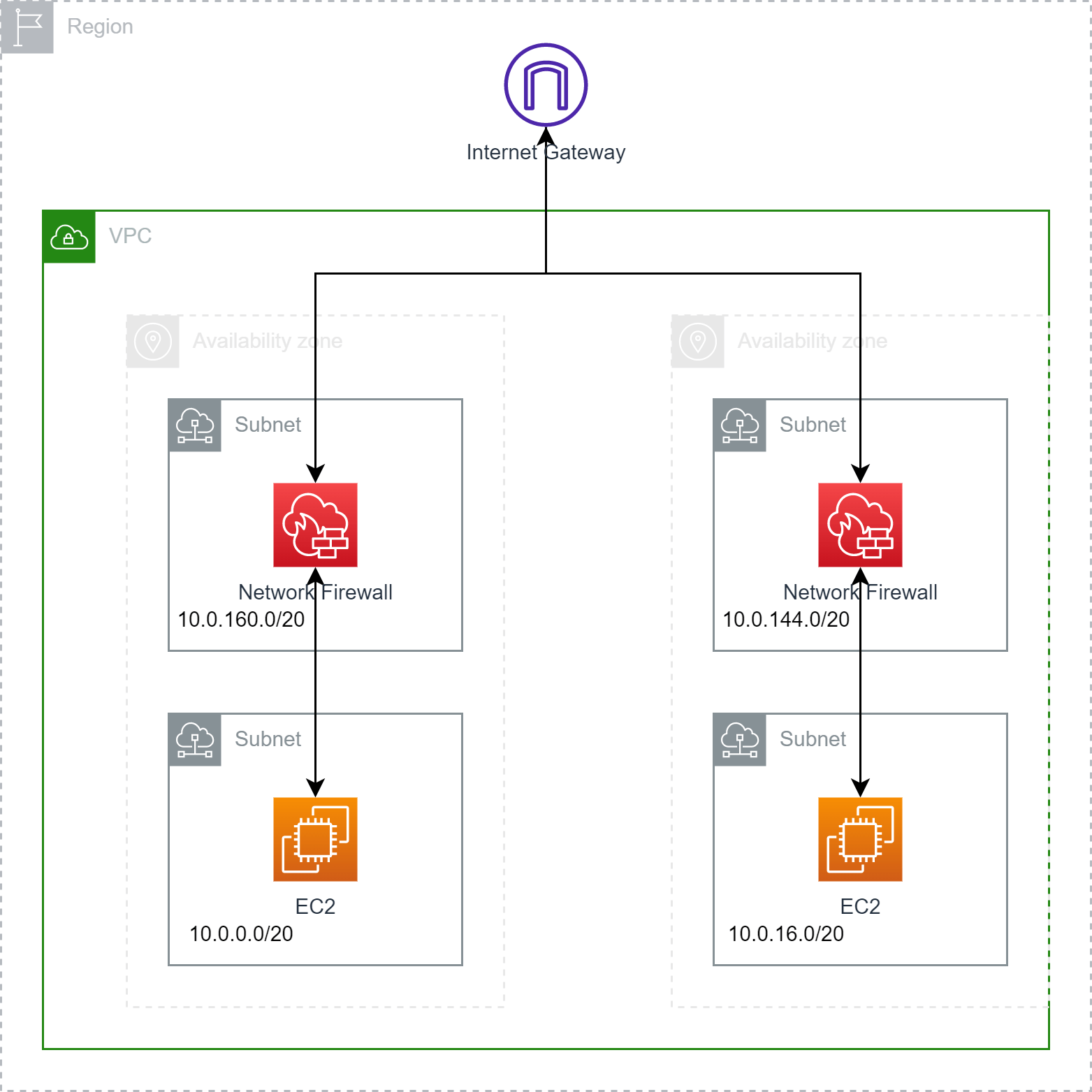
🔨 Prerequisites
- Internet Gateway
- One subnet for the Firewall
- One subnet for the workload
- Three route tables
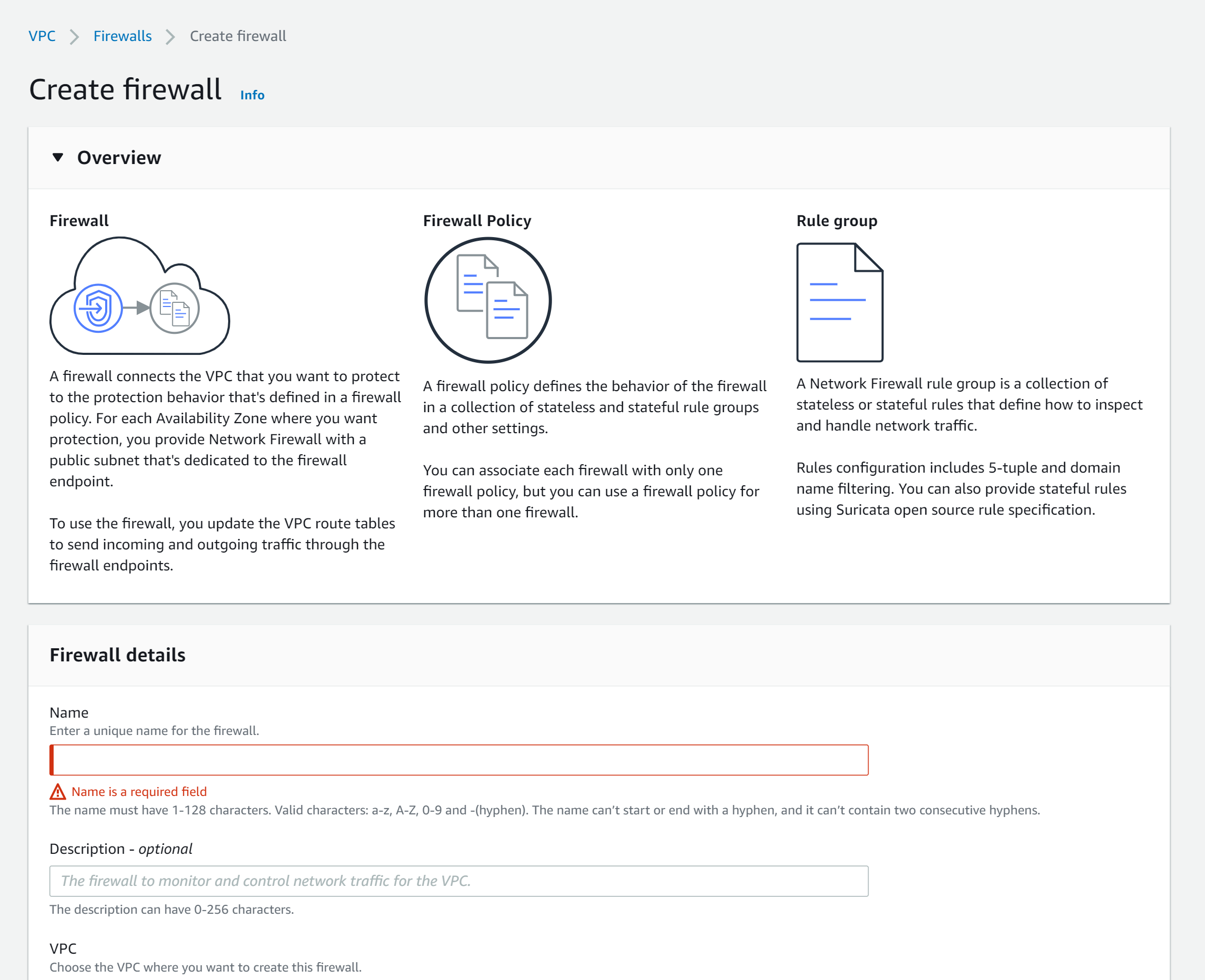
🔥 Create Firewall
First, we need to create a new Network Firewall within our VPC. Make sure to deploy it in a separate subnet.
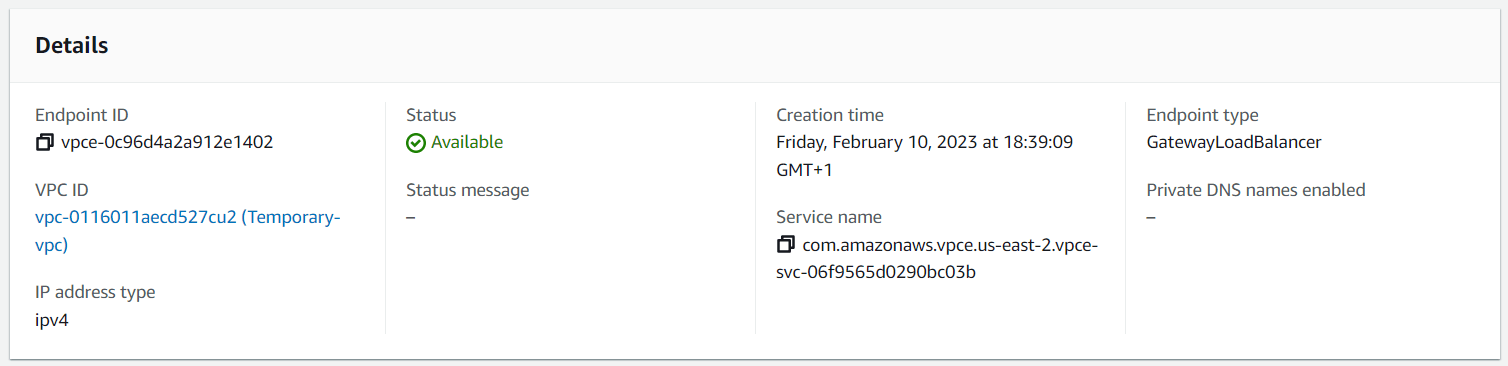
Next, we need to note down the VPC Endpoint created for the firewall. Navigate to Endpoints in the VPC Management Console to get the ID.
📑 Configure Route Tables
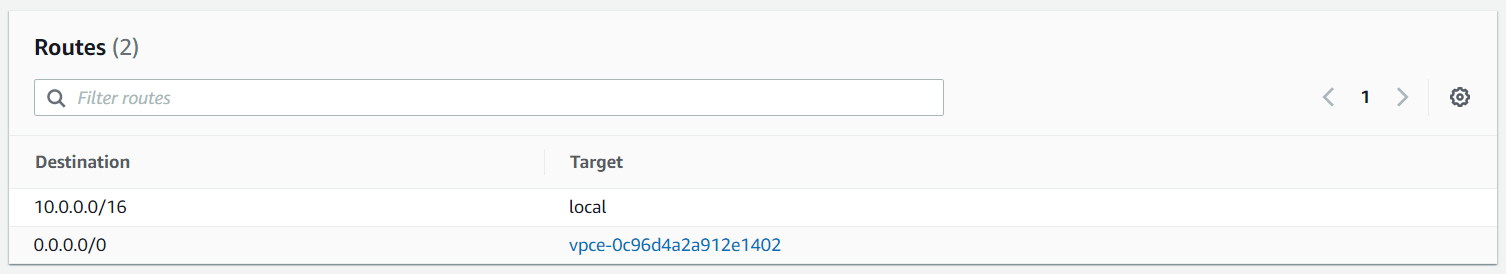
First, we adjust the routing table for the workload. Here we can keep the local routing. As we want to inspect all traffic that goes to the internet, we need to add a new route. This new route will route all traffic to the Firewall VPC Endpoint, which we noted earlier.
Next, we adjust the routing table for the subnet, where the Network Firewall is deployed. Here we add a new route to route all internet traffic to the internet gateway.
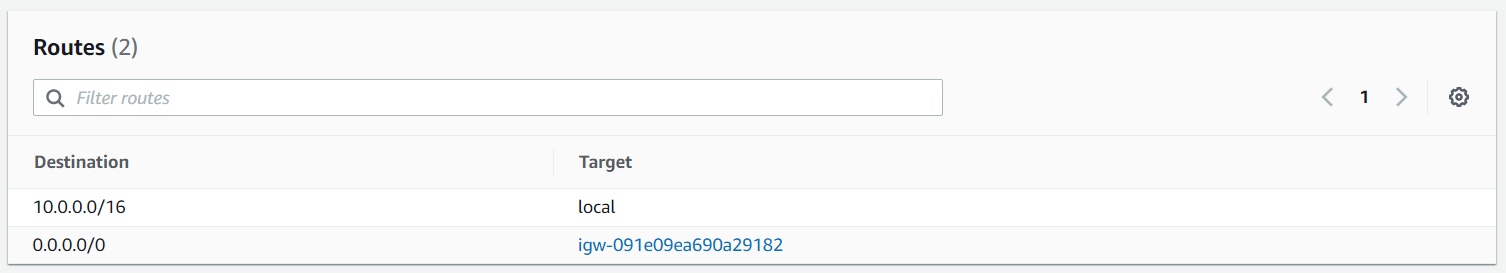
Lastly, we configure the routing table for the Internet Gateway.
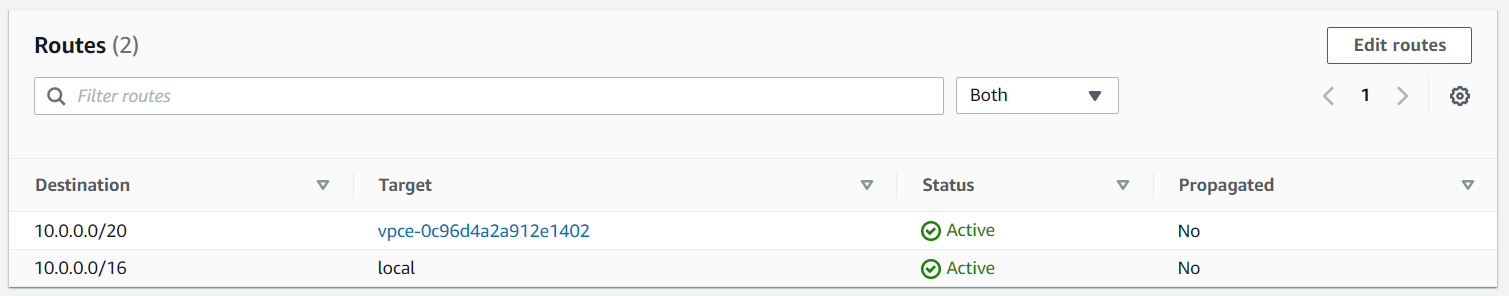
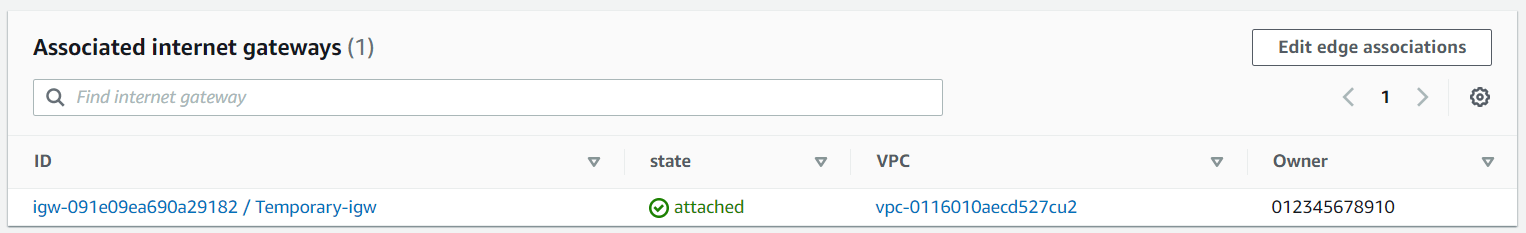
Here it is essential to use a newly created routing table and assign the internet gateway as an edge association. You have this option from the routing table itself.
Furthermore, we need to take the CIDR from the workload subnet and route it via the VPC Endpoint.
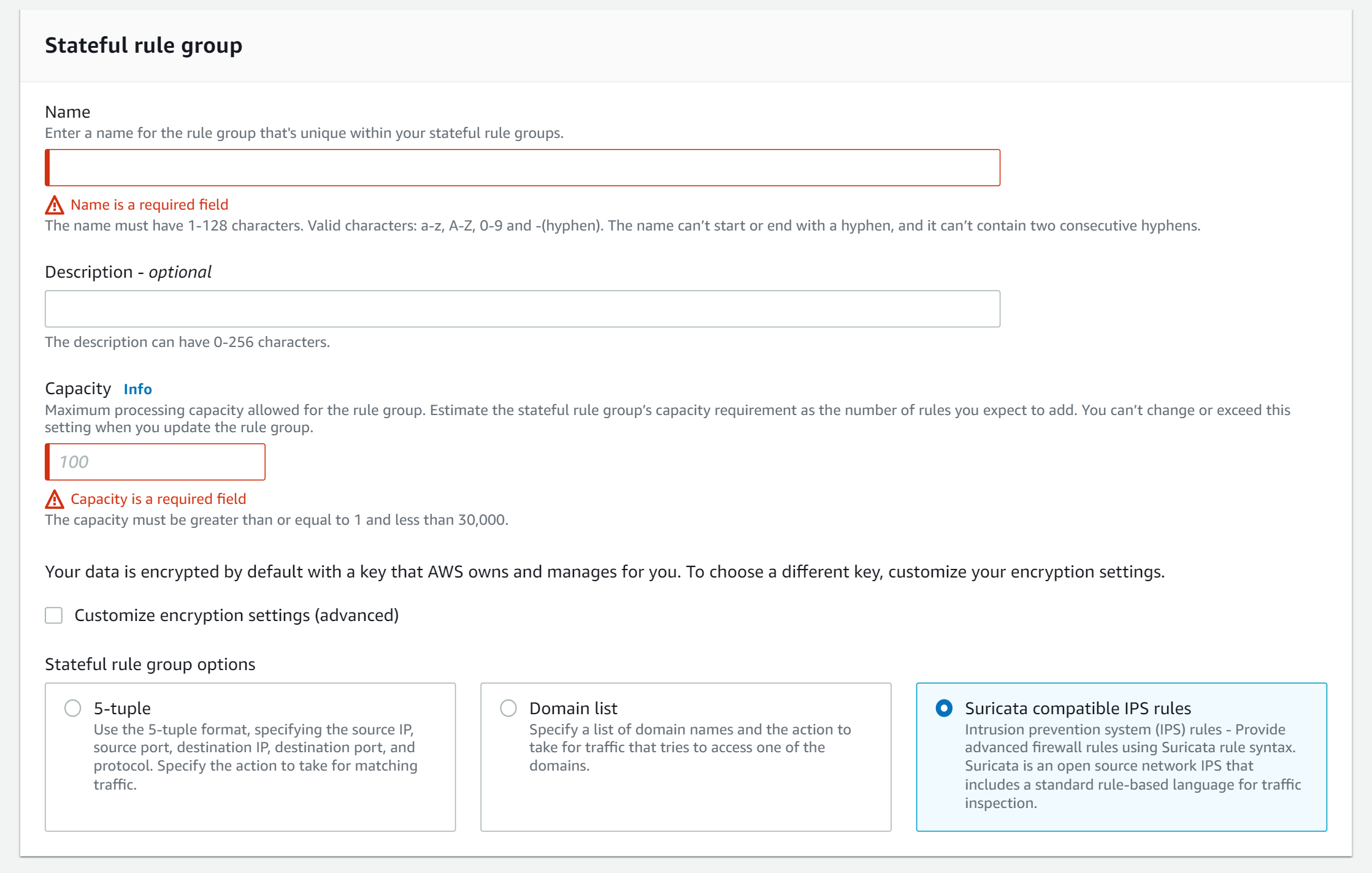
🚨 Create Firewall Policies
Now we have configured the firewall for one of our subnets. All workloads which are deployed in this subnet will route their traffic through the Network Firewall. Now we need to create new policies.
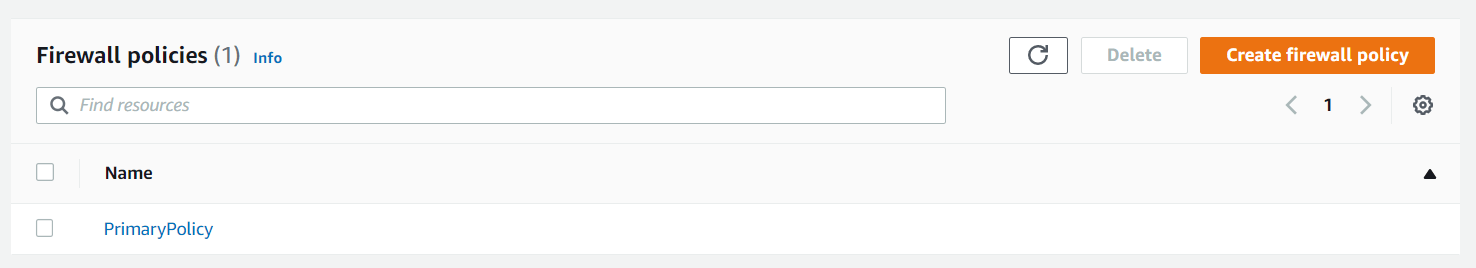
AWS offers a wide range of AWS-managed rules, but we can also create our own. We have three options, either 5-tuple, domain lists, or Suricata-compatible IPS rules.
Check out my previous article about blocking traffic for Network Firewalls:

Congratulations 🎉, you have deployed your own AWS Network Firewall. Now we can create rules and test the firewall. When deploying the Network Firewall, take into account that you need to pay for the Network Firewall Endpoint per hour and separately for each GB of traffic that flows via the firewall.







Member discussion