Managing secrets in AWS ECS (Elastic Container Service) can be challenging, as you want to ensure that sensitive information like passwords, API keys, and database credentials are secure and only accessible to the applications that need them. AWS Secret Manager is a service that helps you manage secrets securely. In this guide, I'll show you how to use it with AWS ECS.
Table of contents
🔐 Create a Secret in AWS Secret Manager
🧰 Define the ECS Task
📄 Attach IAM policy
🔐 Create a Secret in AWS Secret Manager
The first step is to create a secret in AWS Secret Manager. Navigate to the AWS Secret Manager service, and click on "Store a new secret". Here, you can choose between different types of secrets. Make sure to choose an encryption key and note down the key's ARN.
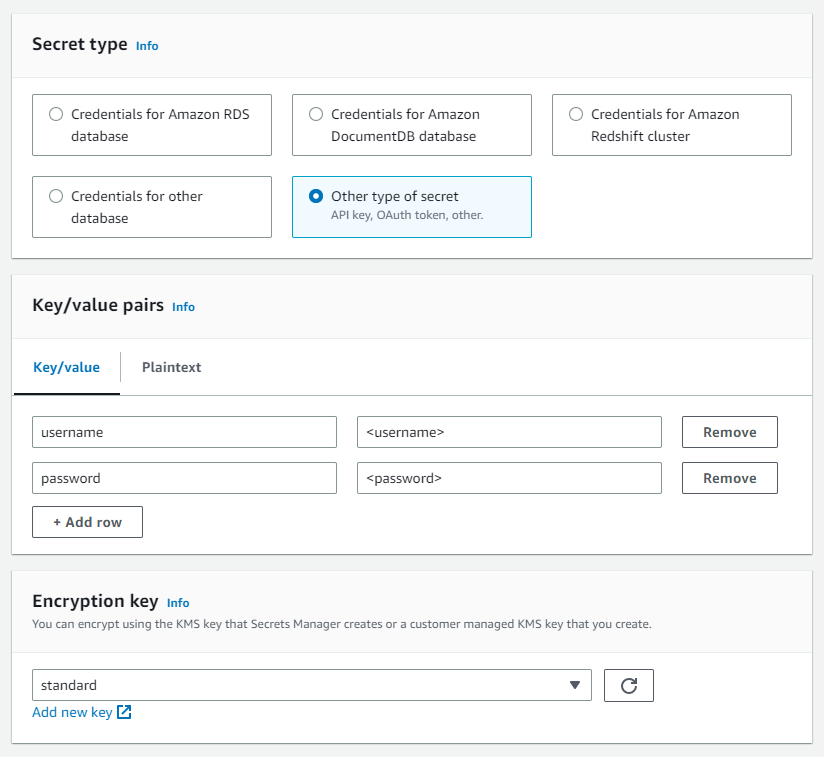
🧰 Define the ECS Task
Next, we need to define the ECS task that will use the secret. You can do this using the AWS ECS Task Definition. In the task definition, you can specify the container image, environment variables, and other settings.
In our case, we need to adjust the Environment variables section of the task definition. The "Key" is the name of the environment variable, which we can later access in the container. The "Value Type" needs to be ValueFrom as we need to utilize AWS Secrets Manager to get the variable. For the "Value", we need to take the ARN of the secret.
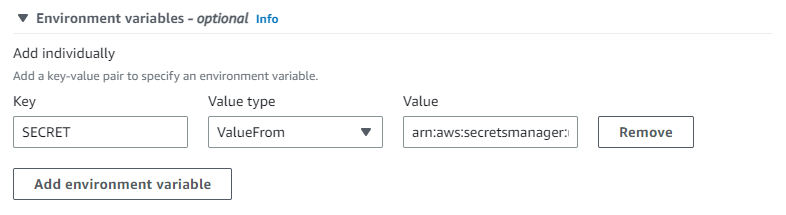
The ARN of the secret is structured in this way: arn:aws:secretsmanager:<region>:<accountID>:secret:<secretName>. If we would now print the environment variable SECRET in our container, we would get the following information:
{
"ARN": "arn:aws:secretsmanager:<region>:<accountID>:secret:<secretName>",
"Name": "<secretName>",
"VersionId": "<versionID>",
"SecretString": "{\"username\":\"<username>\",\"password\":\"<password>"}",
"VersionStages": [
"AWSCURRENT",
"AWSPENDING"
],
"CreatedDate": "2023-03-15T13:53:25.023000+00:00"
}Usually, we don't require this information but want to have the password directly saved in the environment variable. To get this information we need to add the variable name (key of the secret defined in the first section) and two colons at the end of the ARN:
Now the environment variable only holds the information of the secret and no other information.
The JSON file of the task definition will look like this:
"secrets": [
{
"name": "SECRET",
"valueFrom": "arn:aws:secretsmanager:<region>:<accountID>:secret:<secretName>:<variableName>::"
}
]📄 Attach IAM policy
AWS Secret Manager uses AWS Identity and Access Management (IAM) policies to control access to secrets. You need to ensure that the ECS task has permission to access the secret. In the policy, we need to reference the AWS Secrets Manager secret and the KMS key we used to encrypt the secret.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"kms:Decrypt",
"secretsmanager:GetSecretValue"
],
"Resource": [
"arn:aws:kms:<region>:<accountID>:key/<keyID>",
"arn:aws:secretsmanager:<region>:<accountID>:secret:<secretName>"
]
}
]
}Make sure the policy is added to the "Task execution role" of the task.
Conclusion
🎉 That's it to read secrets from AWS Secrets Manager in ECS. The only tricky part of reading secrets is knowing that you need to add additional information to the ARN to directly reference the secret.







