Introduction
Before diving into the implementation process, it is essential to grasp the concept of GCP IAM conditions. IAM conditions allow you to define fine-grained access controls based on various attributes such as time ⏰ or resource being accessed 🗄️. By setting specific conditions, you can enforce additional security measures 🔒. Ensuring that only authorized entities can access your resources.
In the previous article, we covered the creation of service accounts, set roles, and attach them to GCP services. This knowledge forms the foundation for this article. 📚

This article focuses on assigning permissions to principles based on time. This can be particularly useful for granting short-term elevated permissions or for batch jobs that consistently run at specific times of the day. The benefit is that if the administrator forgets to revoke access from the service account, the IAM condition can automatically expire the access after a certain time.
Step 1: Select IAM principle 🔐
Let's delve into IAM conditions. Initially, we need to choose an IAM principal, such as a service account or user. In my case, I will create a new service account.
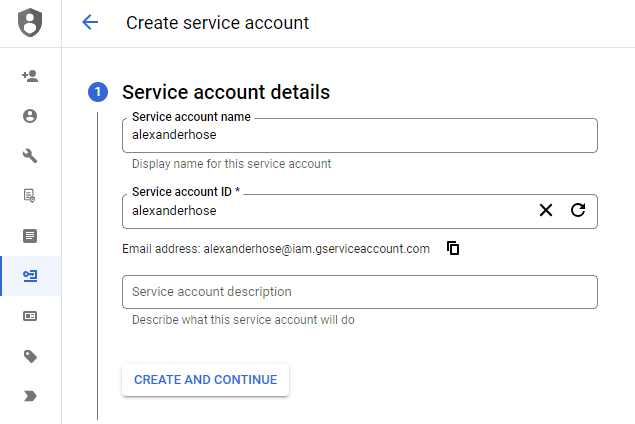
Alternatively, you can access the IAM service, select a principal, and click on the edit button on the right-hand side 📝.
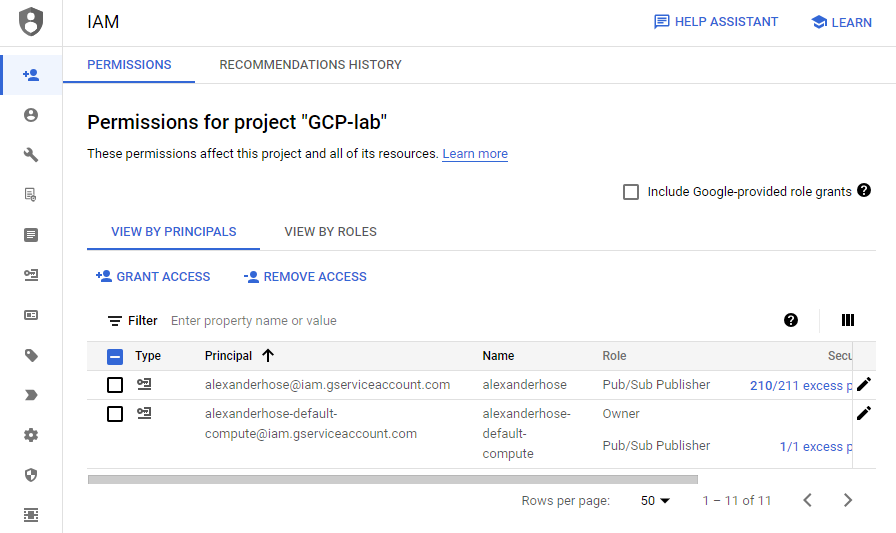
Step 2: Configure conditional access 🛑
In this step, where we grant the principal access to other services, we have the option to edit the IAM condition. I have assigned the Pub/Sub Publisher role to the service account. Now, I want to restrict access to this role based on different time periods.
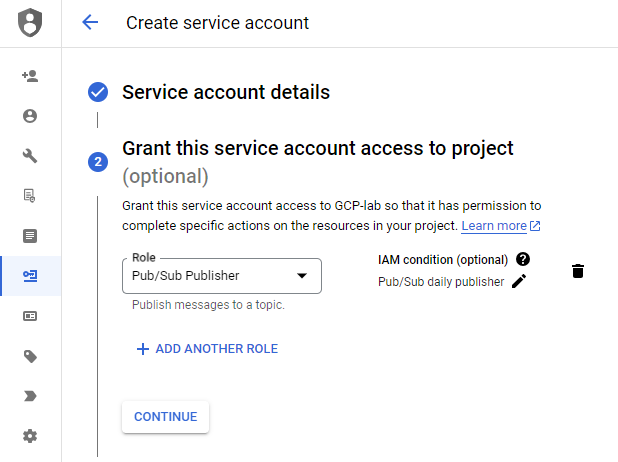
Within the condition builder, we have a user-friendly interface to construct our conditions. In this scenario, we select every Saturday between 10:00 and 13:59 until the end of the year. As a result, the service account can publish Pub/Sub messages only during this timeframe.
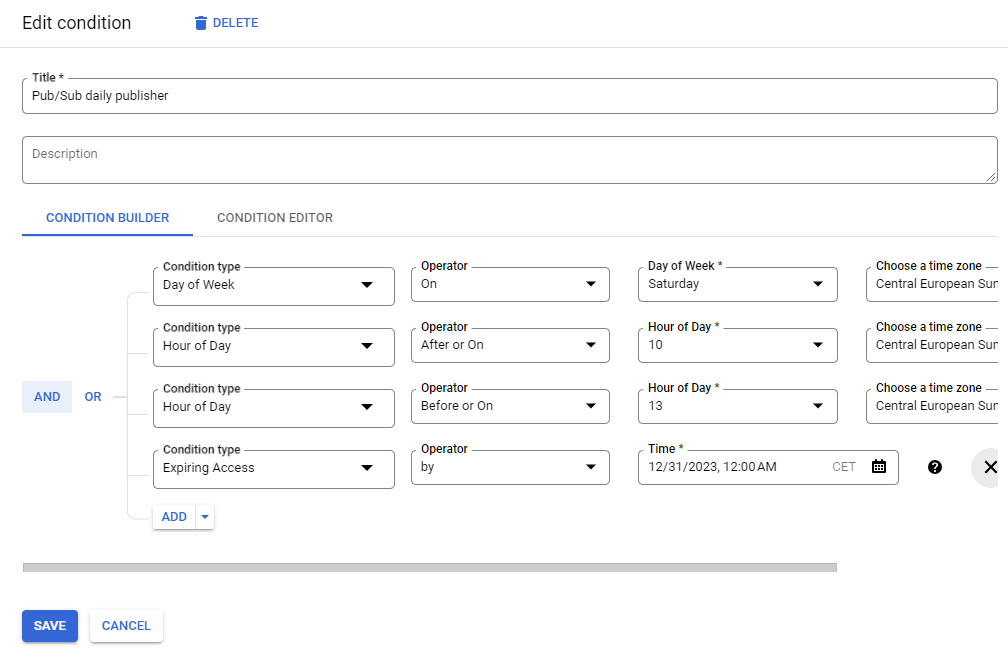
We can also select the condition editor. The editor supports the Common Expression Language (CEL). The above example can be translated into the following CEL:
request.time.getDayOfWeek("Europe/Berlin") == 6 &&
request.time.getHours("Europe/Berlin") >= 10 &&
request.time.getHours("Europe/Berlin") <= 13 &&
request.time < timestamp("2023-12-30T23:00:00.000Z")Step 3: Test access to GCP services 🧪
Now we are prepared to test the access of the service account. I have created a pub/sub topic and attempted to publish a test message at noon on a Saturday, and successfully obtained the message ID:
alexanderhose@instance:~$ gcloud pubsub topics publish alexanderhose-topic --message="Hello World!"
messageIds:
- '1234567890'If I attempt to perform this action outside the specified timeframe, I will receive an error message:
alexanderhose@instance:~$ gcloud pubsub topics publish alexanderhose-topic --message="Hello World!"
ERROR: (gcloud.pubsub.topics.publish) PERMISSION_DENIED: User not authorized to perform this action.Conclusion 🎉
GCP IAM conditions offer a robust solution for implementing fine-grained access controls. This can be done based on attributes like time and resources. This article focused on the importance of IAM conditions in assigning permissions on a time basis. Which is particularly useful for managing short-term elevated access or scheduling batch jobs. With IAM conditions, you can set specific criteria to automatically control access and mitigate the risk of unintended or prolonged access.










Member discussion