Do you want to take control of your cloud security posture? 🔐
If so, you must know about GCP Security Command Center (SCC) custom policies. Custom policies allow you to define rules for what constitutes a security violation. This gives you the flexibility to tailor SCC to your specific needs and requirements.
For example, you could create a policy that requires all VMs to be encrypted. Or, you could create a policy that checks for exposed ports for the firewall.
The possibilities are endless. The best part is, that creating custom policies is easy. In just a few clicks, you can create a policy that will help you to protect your data and your organization. The configuration is just hidden in the UI of SCC.
So what are you waiting for? Start creating custom policies today!
Create Custom Module In GCP SCC Health Analytics 📝
Let's start with the settings of our SCC. You click on the settings button in the top right corner. Ensure you are using the SCC Premium Tier otherwise, you won't have the option.
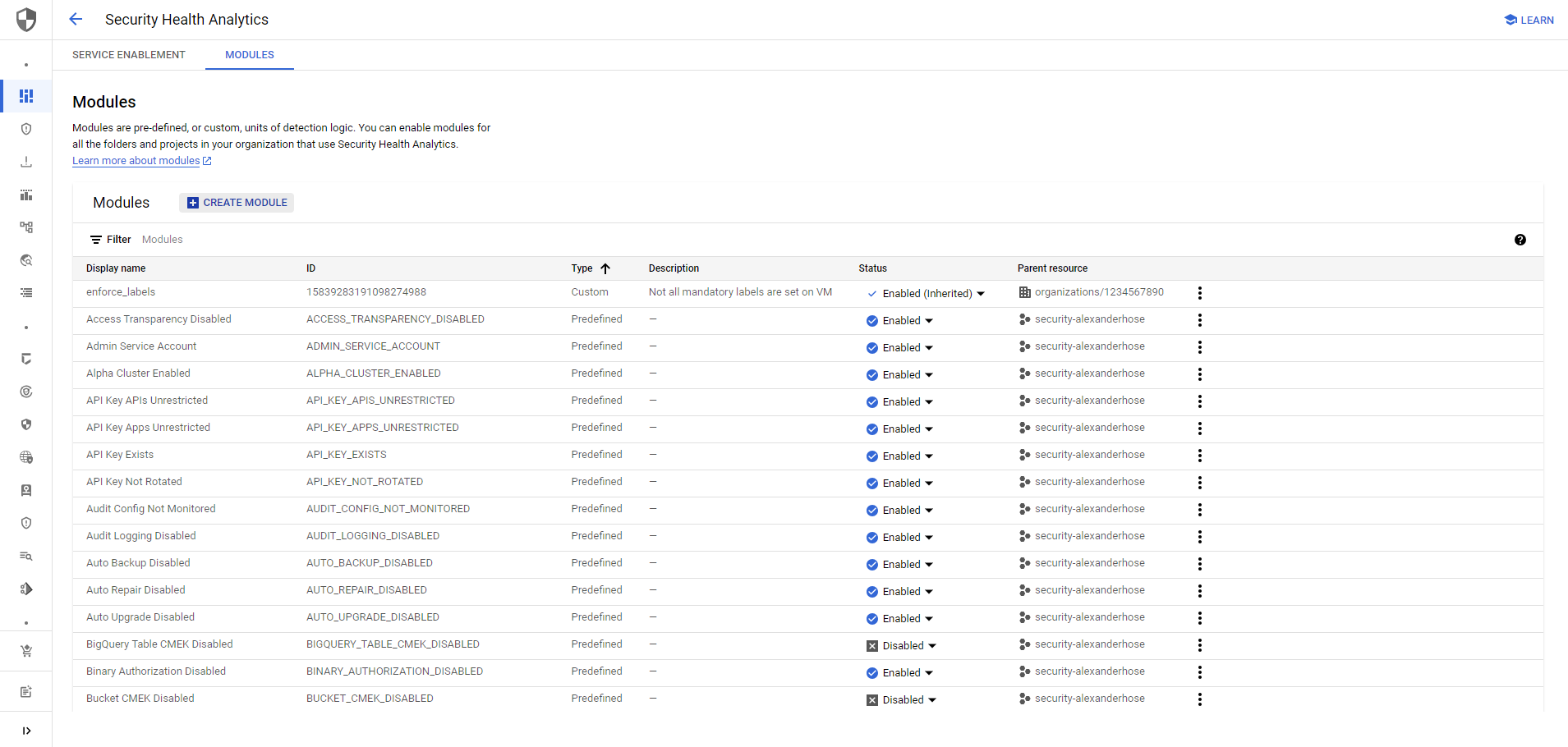
Next, you navigate to the Security Health Analytics settings. Here you can click on Create Module.
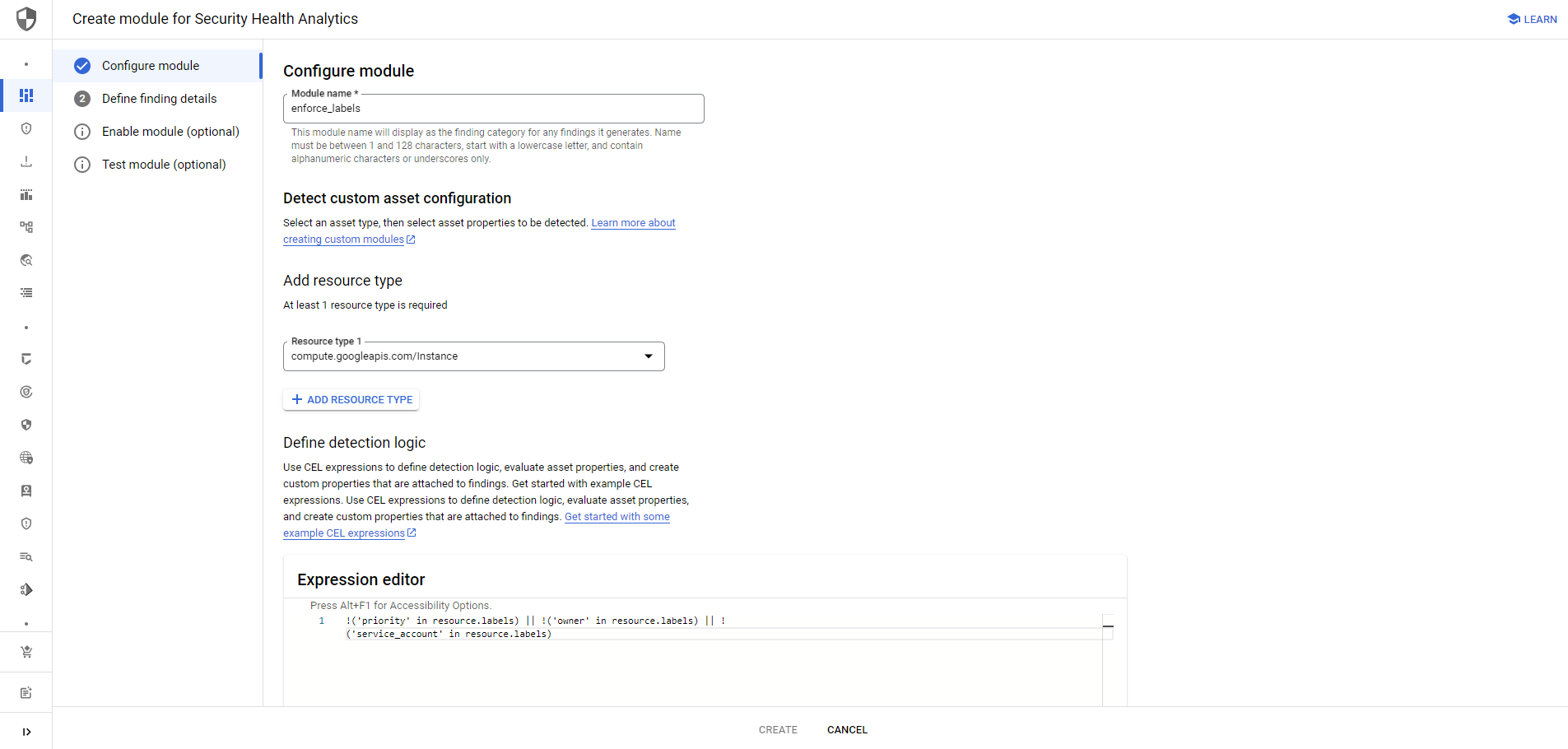
Let's give the new module or policy a catchy name. This will later be the name that is present in the overview of the findings. We also need to choose the resources that we want to analyze.

Join our community of cloud security professionals. 🔐
Subscribe to our newsletterUse CEL expressions to define the detection logic and evaluate asset properties.
- CEL expressions are a powerful way to define detection logic and evaluate asset properties. (https://github.com/google/cel-spec)
- You can use CEL expressions to evaluate asset properties, such as the size of a disk, the number of open ports or labels, etc.
Here are some specific examples of how CEL expressions can be used:
- Check if all mandatory labels are set for a compute instance
!('priority' in resource.labels) || !('owner' in resource.labels) || !('service_account' in resource.labels) - Check if labels contain certain values
!(resource.labels['priority'] in ['low', 'medium', 'high', 'critical'])If you are not sure how certain properties are structured of a GCP service, you can use gcloud for that gcloud compute instances describe <instanceName>.
Afterward, we just need to assign the severity, a description and finding related next steps.
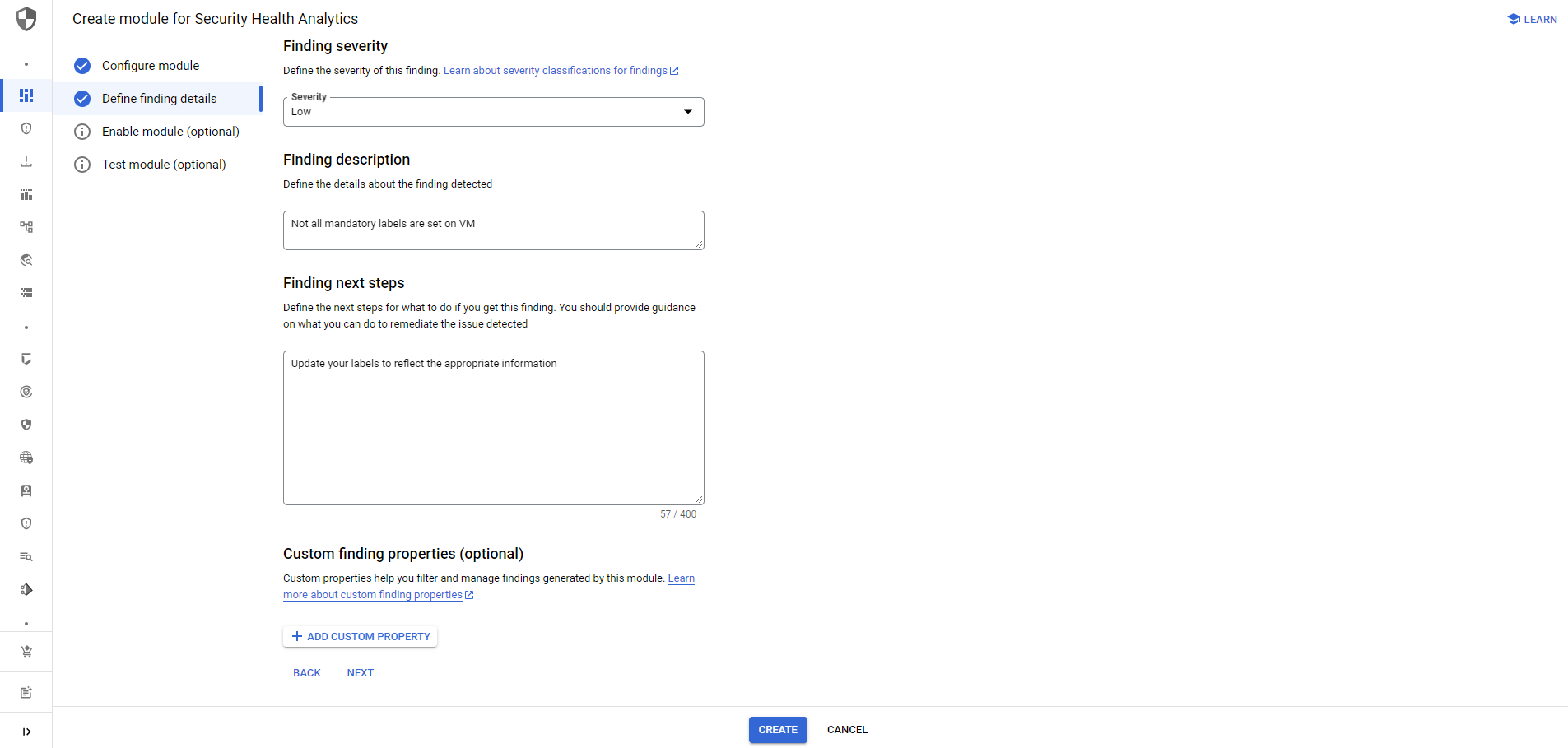
You can also test the policies during the creation process. Here is an example file to test the above policy:
testData:
- asset:
resource: //compute.googleapis.com/projects/alexanderhose/zones/us-central1-c/instances/keycloak
assetType: compute.googleapis.com/Instance
resourceData:
labels:
owner: alexander
service_account: naConclusion 🎓
In this blog post, we have discussed how to use CEL expressions to define detection logic and evaluate asset properties to create GCP SCC Health Analytics custom policies or modules. We have also provided some specific examples of how CEL expressions can be used.
I am super excited about this topic because it allows us to adjust the finding dashboards and create policies based on our company's requirements. This gives us the flexibility to tailor SCC to our specific needs and requirements, which is essential for protecting our data and our organization.
You can also check my previous article on how to create custom GCP organizational policies to ensure the above is not happening when creating resources.








Member discussion