Introduction
One essential aspect of GCP administration is implementing organization policies to ensure security 🔒, compliance 📜, and governance 📊. In this guide, we will explore how to create custom GCP organization policies to enhance your cloud posture. 🔐
The Importance of GCP Organization Policies 📜
Before we dive into the nitty-gritty of creating custom organization policies, let's understand their significance. GCP organization policies act as a set of rules and restrictions that govern the behavior of cloud resources within a project or organization. They help enforce compliance with internal policies, industry regulations, and data protection standards. In the past, we could only utilize the predefined policies from GCP. With the new preview of custom policies, we can define our own rules. Currently, the following services are supported:
compute.googleapis.com/Diskcompute.googleapis.com/Firewallcompute.googleapis.com/Imagecompute.googleapis.com/Instancecompute.googleapis.com/Networkcompute.googleapis.com/Routecompute.googleapis.com/Subnetworkcontainer.googleapis.com/Clustercontainer.googleapis.com/NodePooldataproc.googleapis.com/Cluster
The Basics of GCP Organization Policies 🏢
Built-in vs. Custom Organization Policies
Google Cloud provides a variety of pre-configured, built-in organization policies. While these policies cover common security and compliance needs, they might not cater to the specific requirements of your organization. This is where custom organization policies come into play, allowing you to tailor the rules to your unique needs.
Policy Resources and Conditions
Organization policies are based on resource types and conditions. Resource types define which resources are covered by the policy. While conditions specify the actual restrictions to be enforced. The conditions can be crafted with the Common Expression Language (CEL). This combination offers a flexible and granular approach to managing your resources.
Impact on Projects and Resources
Implementing organization policies can have a profound impact on your projects and resources. It's crucial to assess the potential consequences and thoroughly test policies before enforcement to avoid any unintended disruptions. You can create a separate project or folder to test those policies before activating them for your whole organization.
How to Create Custom GCP Organization Policies 🧪
If you log in to your organization account and navigate to organization policies, you will see a button called custom constraint at the top.
In the wizard 🧙♂️, you need to give some basic information like the name, constraint ID, and description. Afterward, we are getting to the interesting part. In the enforcement section, we can choose the resource type the condition will evaluate. Next, we can define the actual condition.
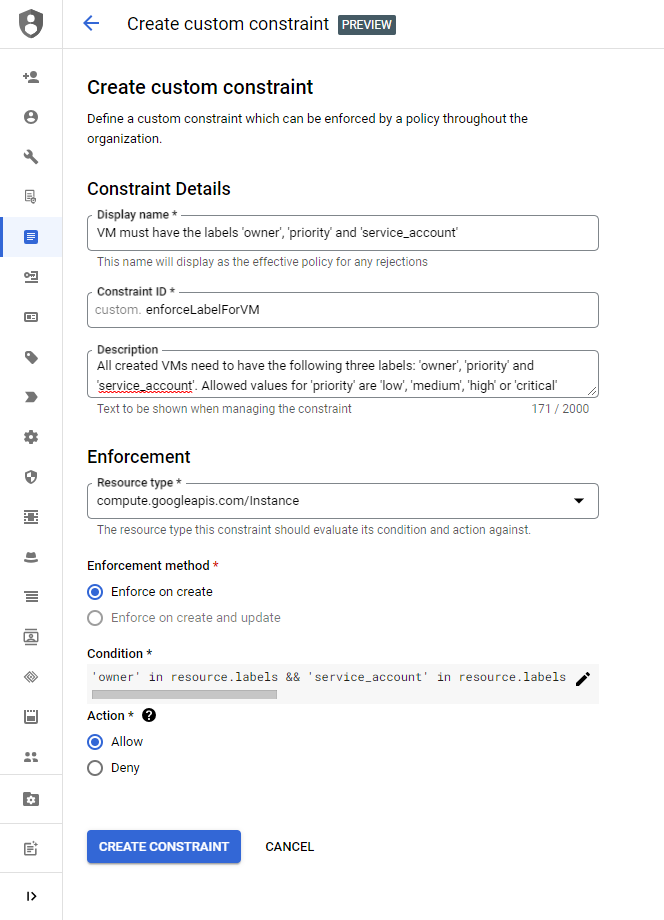
You can reference the CEL documentation on GitHub for all information. In my case, I want to create a policy that enforces to have three labels attached to each compute instance. You can select the fields of the VM with the JSON notation. We also want to ensure that the priority label only has specific values. The policy would look like this:
'owner' in resource.labels && 'service_account' in resource.labels && 'priority' in resource.labels && resource.labels['priority'] in ['low', 'medium', 'high', 'critical']Lastly, we set the action and can enforce the policy. Don't forget that you need to enable the enforcement and isn't activated by default for most organizations.
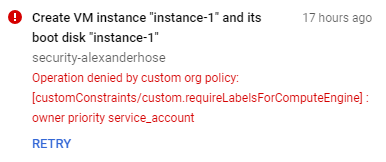
If we are trying to create a compute instance without all tags, we will receive an error and the creation process will be aborted:
Conclusion 🎓
Creating custom GCP organization policies is a crucial step in ensuring the security, compliance, and efficiency of your cloud infrastructure. 🔒 By understanding the basics of GCP organization policies, identifying your specific requirements, and following best practices, you can establish a robust governance framework. Remember that this functionality is in preview as of writing this article. The capabilities are very basic at the moment but are looking very promising. 🚀







Member discussion