Amazon Inspector recently announced the public preview of code scanning for Lambda functions. With this new functionality, AWS now offers static application security testing (SAST). Inspector already had security capabilities for Lambda but that was limited to Software Composition Analysis (SCA), which scans your dependencies for security vulnerabilities.
💡 How it works
Inspector conducts vulnerability scans when an existing Lambda function is discovered, a new Lambda function is deployed, or when the application code is updated in the last 90 days. It utilizes internal detectors developed in collaboration with Amazon CodeGuru to detect vulnerabilities. The complete list of all security detectors:

Lambda code scanning is currently available in preview in five AWS Regions: North Virginia (us-east-1), Ohio (us-east-2), Oregon (us-west-2), Frankfurt (eu-central-1), and Ireland (eu-west-1). During the preview period, Lambda code scanning is available at no additional cost to customers. Currently, the following programming languages are supported:
Java
- java8
- java8.al2
- java11
NodeJS
- nodejs12.x
- nodejs14.x
- nodejs16.x
- nodejs18.x
Python
- python3.7
- python3.8
- python3.9
Go
- go1.x
🛠️ Setup Lambda code scanning
You can activate/deactivate AWS Lambda scanning in the account management section of Inspector.
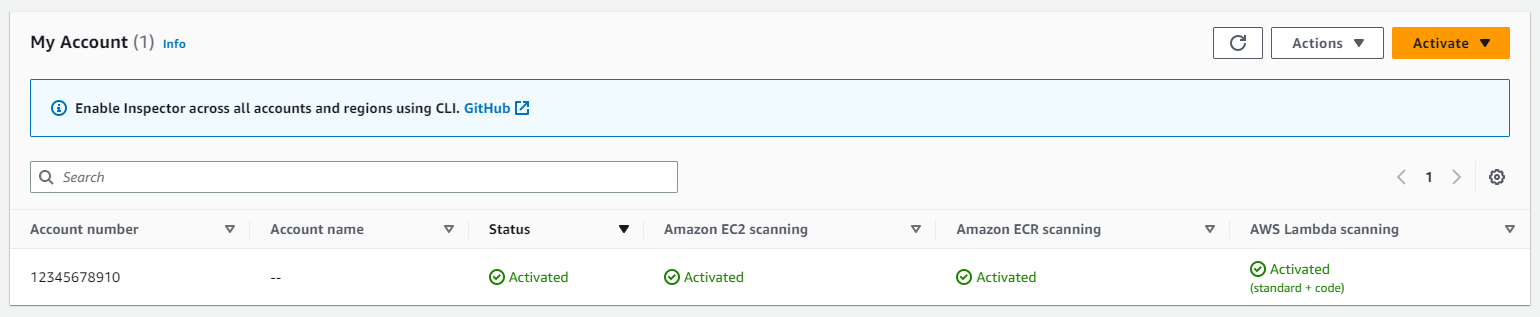
After activation, it will automatically start scanning your Lambda functions.
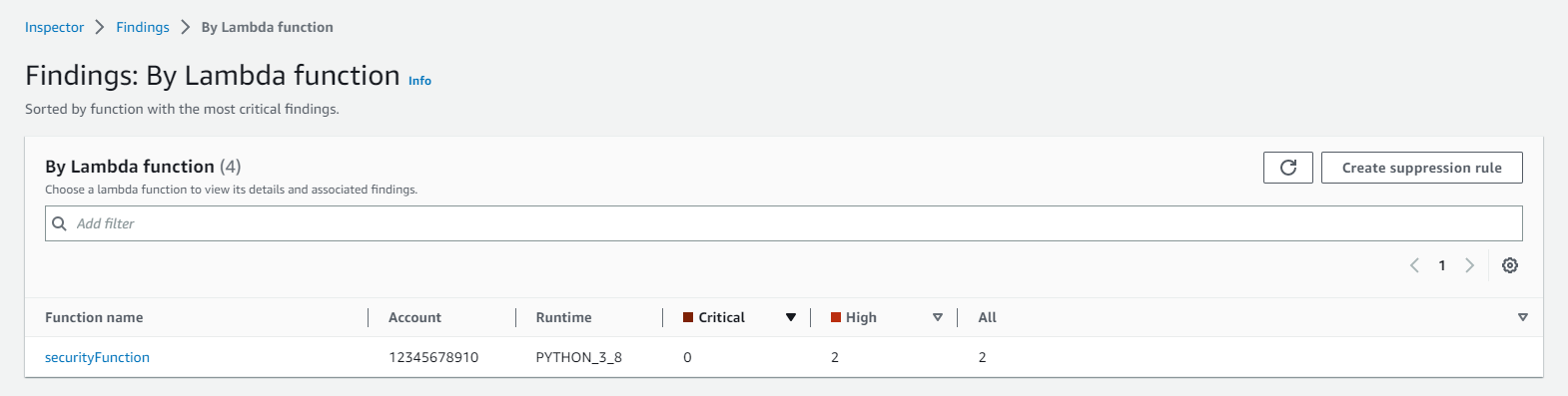
We can then see the vulnerabilities identified for the different Lambda functions. On the right-hand side, it will show us the vulnerability location and suggested remediation.
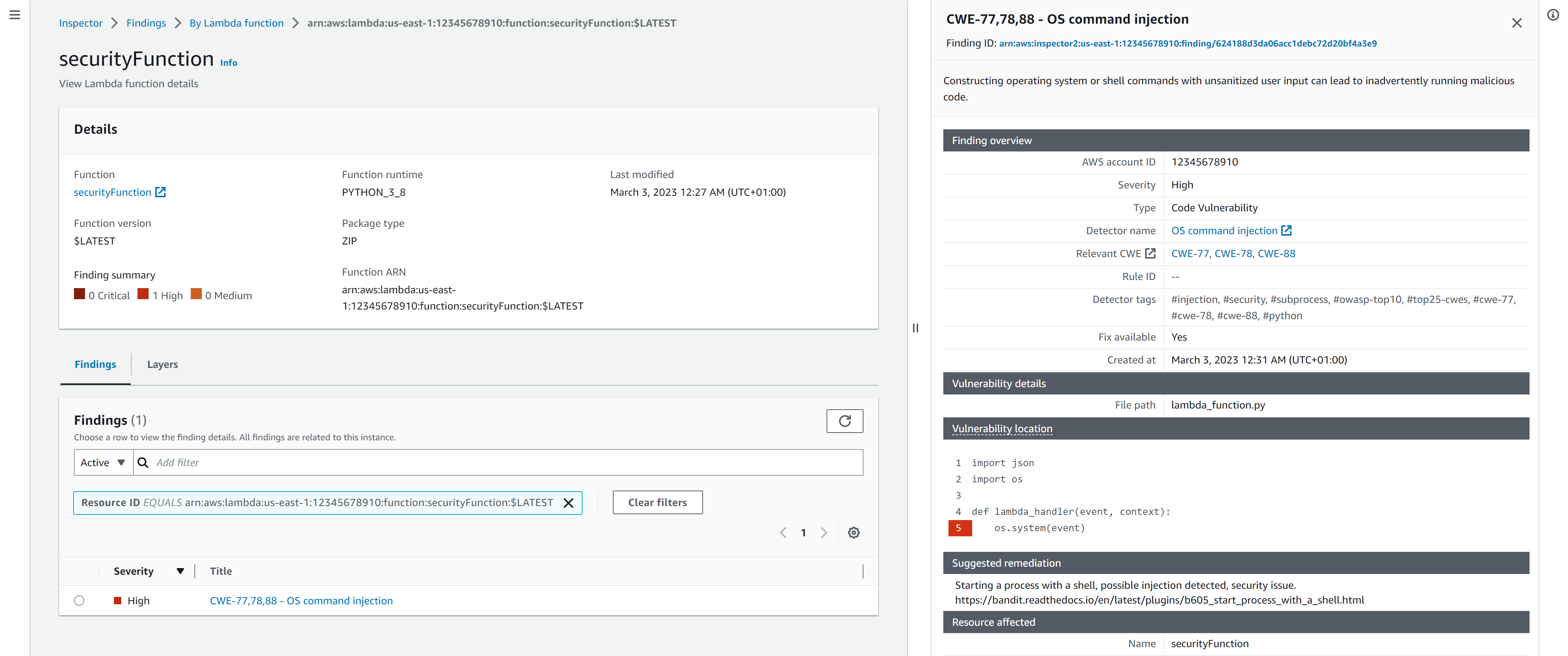
We can also query all results via the AWS CLI. This way you could potentially implement Inspector in your CI/CD pipelines. You can use the --filter argument to select your Lambda function.
alexanderhose:~/ $ aws inspector2 list-findings --filter='{"lambdaFunctionName": [{"comparison": "EQUALS","value": "securityFunction"}]}'
{
"findings": [
{
"awsAccountId": "12345678910",
"description": "Constructing operating system or shell commands with unsanitized user input can lead to inadvertently running malicious code.",
"findingArn": "arn:aws:inspector2:us-east-1:12345678910:finding/624188d3da06acc1debc72d20bf4a3e9",
"firstObservedAt": "2023-03-02T23:35:10.230000+00:00",
"lastObservedAt": "2023-03-02T23:35:10.230000+00:00",
"remediation": {
"recommendation": {
"text": "Starting a process with a shell, possible injection detected, security issue. https://bandit.readthedocs.io/en/latest/plugins/b605_start_process_with_a_shell.html"
}
},
"resources": [
{
...
}
],
"severity": "HIGH",
"status": "ACTIVE",
"title": "CWE-77,78,88 - OS command injection",
"type": "CODE_VULNERABILITY",
"updatedAt": "2023-03-02T23:35:10.230000+00:00"
},
]
}🎓 Conclusion
Lambda scanning expands the existing capability to scan application package dependencies for vulnerabilities. With the ability to scan code within a Lambda function for code security vulnerabilities, Inspector offers a more comprehensive vulnerability management solution. Inspector generates actionable security findings. And streamlines the vulnerability management processes. You can enable your developers more quickly and efficiently to remediate vulnerabilities.









Member discussion