I recently had a discussion about how to protect APIs and workloads efficiently against various threats. Website security has become a primary concern for businesses and individuals alike. It is essential to take measures to ensure the protection of your workload and APIs. Besides having preventive measures in our Software Development Lifecycle (SDLC), we can also use reactive measures. One of the most effective reactive ways is by implementing a Web Application Firewall (WAF).
AWS WAF is a powerful solution that can provide security to your website, safeguarding it against various types of attacks. In this article, we will discuss how AWS WAF can help maximize your website's security. We also cover the necessary steps to implement it.
Table of content
🔥 What is AWS Web Application Firewall?
🔑 Why is AWS WAF important for your website's security?
🛠️ Implementing AWS WAF
📝 Conclusion
🔥 What is AWS Web Application Firewall?
AWS WAF is providing real-time web application protection. It can detect and block various types of attacks, including SQL injection, cross-site scripting (XSS), and other web application vulnerabilities. You can define custom rules and actions that control the traffic to your web application.
AWS WAF operates on the Application Layer (Layer 7) of the OSI model. The application layer is covering protocols like HTTP or HTTPS. This way the WAF can inspect traffic and identify malicious payloads in the requests. It enables it to provide a more in-depth and sophisticated analysis of web traffic.
The WAF can protect CloudFront, Application Load Balancer (ALB), Amazon API Gateway, Amazon Cognito user pool, and AWS AppSync.
🔑 Why is AWS WAF important for your website's security?
I always recommend covering security from the start of the SDLC. AWS WAF is a reactive measure only. It would be best if you think about it as an additional layer of security only.
Websites are vulnerable to a wide range of attacks that can lead to a compromise. Attackers use automated vulnerability scanners to scan huge numbers of web applications. Or do manual testing of URLs and try to break in. AWS WAF provides a reliable and robust solution to secure your web applications from those attacks. It lets you set up rules to prevent attackers from exploiting known vulnerabilities.
AWS WAF is highly scalable and can handle large volumes of traffic, making it an ideal solution for websites of all sizes.
🛠️ Implementing AWS WAF
Implementing AWS WAF is a straightforward process. The following are the steps to follow to implement AWS WAF successfully.

Step 1: Identify the web application that requires protection.
The first step is to identify the web application that requires protection. This could be a web application integrated with Amazon CloudFront, the ALB, Amazon API Gateway, Amazon Cognito user pool, or AWS AppSync. In our example, we will take use an API Gateway.
Step 2: Create an AWS WAF web ACL.
The next step is to create an AWS WAF web Access Control List (ACL). A web ACL is a set of rules that define the conditions under which requests are allowed or blocked. Make sure to select the correct resource type from step 1 here.

Step 3: Define rules for the web ACL.
After creating the web ACL, you need to define rules that specify how incoming requests are evaluated. AWS WAF provides several built-in rules that you can use as a starting point.

You can also create custom rules that meet your specific requirements. We can choose from the types:
- IP set - Specific set of IP addresses.
- Rule Builder - Custom rule to inspect the requests based on different patterns.
- Rule Group - Combine several rules into one.
We could use the IP set to block specific IP ranges. As this setup would be straightforward, I will focus on the rule builder. Here we can choose between rate-based and regular rules.
Enjoy this article? Subscribe to receive the latest news about cloud security here 📫
Rate-based rule
All rules are based on an if-then concept. For the rate-based rule, we can choose how many requests can be made from one IP address before an action is taken. The action can be either Block, Count, CAPTCHA, or Challenge. In our example, let's choose CAPTCHA and set the rate limit to 100 for testing.
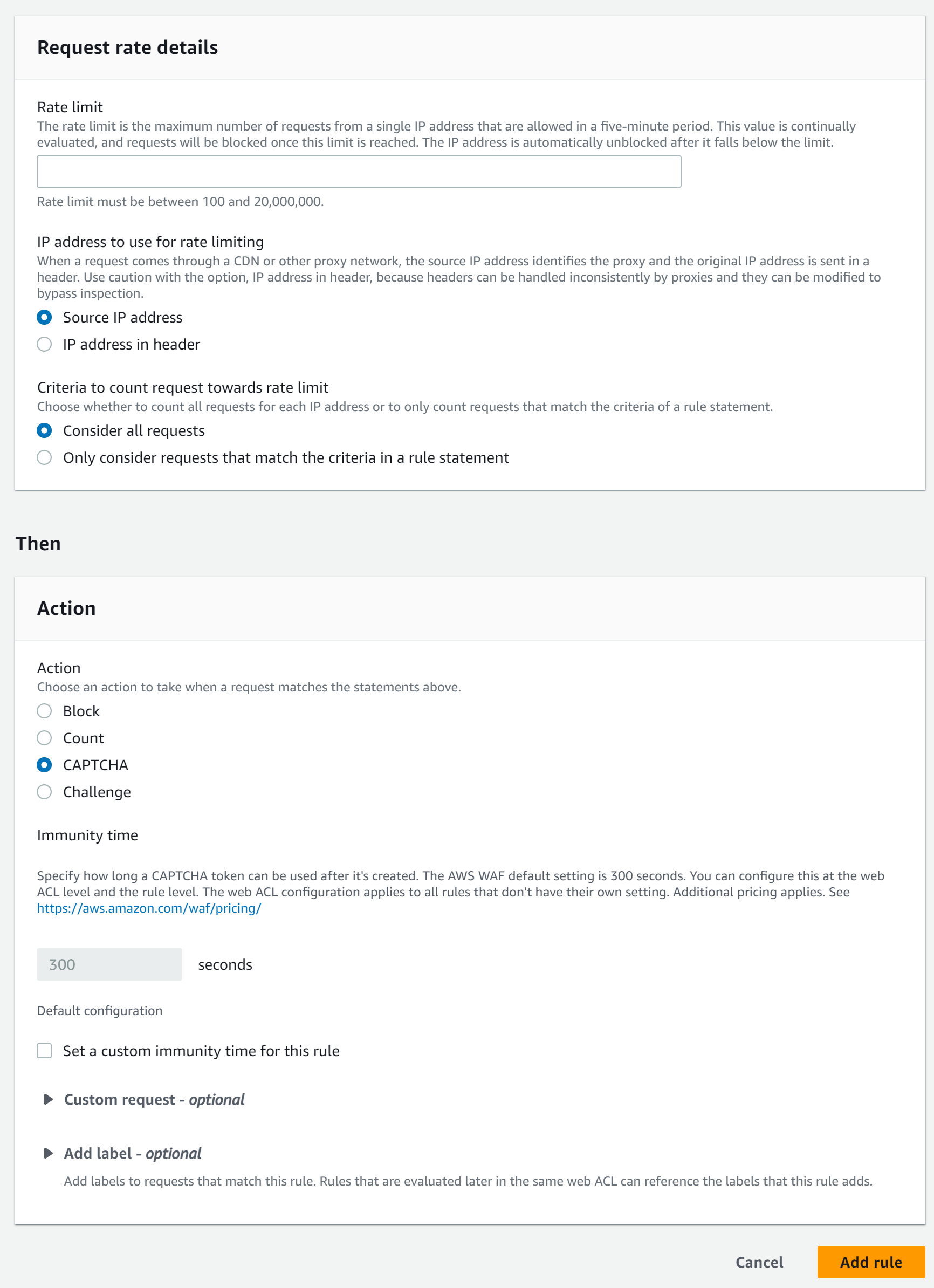
After 100 requests to the API Gateway, we will be prompted to solve a CAPTCHA. After solving this an AWS WAF token will be added to our cookies. All further requests require this token. Otherwise, we will need to solve another CAPTCHA.
$ curl -b "aws-waf-token=<token>" https://<API Gateway>/Test/user/1
{
"id": 1,
"type": "admin",
"username": "alexanderhose"
}📢 Important information
🕒 AWS WAF monitors the rate of requests every 30 seconds and counts requests for the prior five minutes each time.
🚫 An IP address can send requests at too high a rate for 30 seconds before AWS WAF detects and blocks it.
🚷 AWS WAF can block up to 10,000 IP addresses.
Regular rule
Regular rules are also based on the if-then concept. We can inspect different parts of the request made to our application. In our example, we want to forbid any special characters in the query string of the request. We can choose the matches regular expression type and add our regex [$&+,:;?@#|'<>.^*()%!-]. As we want to block any usage of special characters, we need to choose the action block.

If we now try to invoke the API with a special character in the query string, we will be blocked.
$ curl https://<API Gateway>/Test/user/1?get=user%
{
"message":"Forbidden"
}If you are interested in geo-based blocking, check out my previous blog article:

Associate AWS resources
Afterward, we need to choose the resources, we want to associate with the web ACL.

Step 4: Monitor and fine-tune the web ACL.
After implementing the web ACL, you need to monitor and fine-tune it regularly. AWS WAF provides detailed logs that allow you to analyze traffic patterns and detect potential attacks. You can use this information to modify your rules and improve the effectiveness of your web ACL.
📝 Conclusion
AWS WAF is an effective solution for protecting your web applications from common web exploits. It is a reactive security measure, so won't replace secure development principles.
By setting up AWS WAF, you can enhance the security of your website and protect your users' sensitive information. AWS WAF provides a powerful set of features that enable you to create custom rules or choose from a wide range of AWS-managed rules.
Remember to keep your AWS WAF rules up to date and monitor your website's traffic regularly to ensure that your security measures are effective.








Member discussion