Introduction
GCP offers a powerful security solution known as the GCP Security Command Center (SCC). This guide will explore the key features and best practices to secure your cloud using GCP SCC.
What is GCP SCC?
GCP SCC is a comprehensive security management and risk assessment platform. It offers centralized visibility into the security posture of your cloud infrastructure, applications, and data. By leveraging advanced security analytics, it helps organizations detect, prevent, and respond to security threats effectively. Currently, 6 different modules are available:
- Security Health Analytics
- Web Security Scanner
- Event Threat Detection
- Container Threat Detection
- Rapid Vulnerability Detection
- Virtual Machine Threat Detection
Understanding the Importance of SCC and Cloud Security 🔐
Cloud security is crucial for any organization that relies on cloud services. Breaches and unauthorized access can result in significant financial losses, reputational damage, and legal consequences. GCP SCC provides a proactive approach to identify vulnerabilities, monitor threats, and help mitigate risks. Ensuring the integrity and confidentiality of your cloud environment.
Setup SCC 🧪
You can choose between the Premium and Standard tier. The Standard tier only includes Security Health Analytics and shows basic misconfiguration. This is helpful for small organizations, that run noncritical workloads.
If you own an organization, the Premium tier is definitely advisable as it offers better threat detection capabilities.
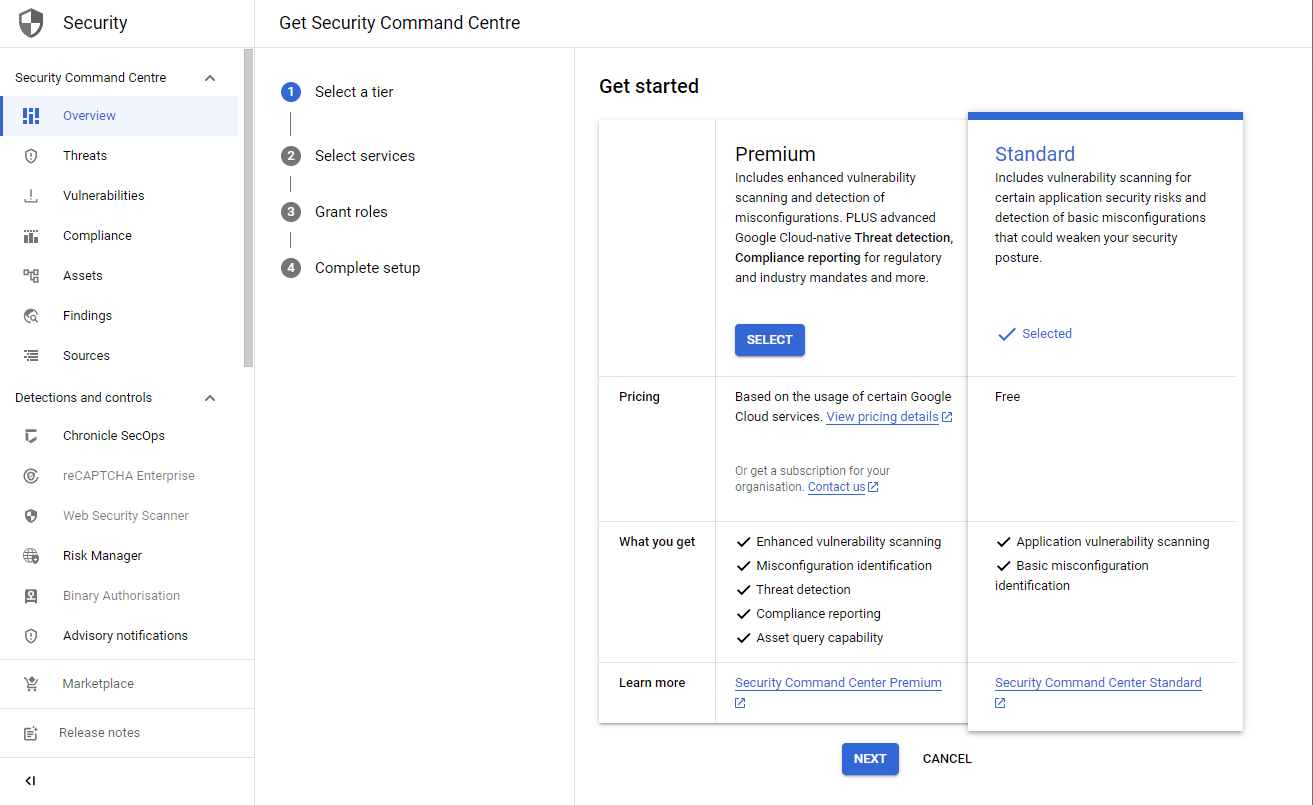
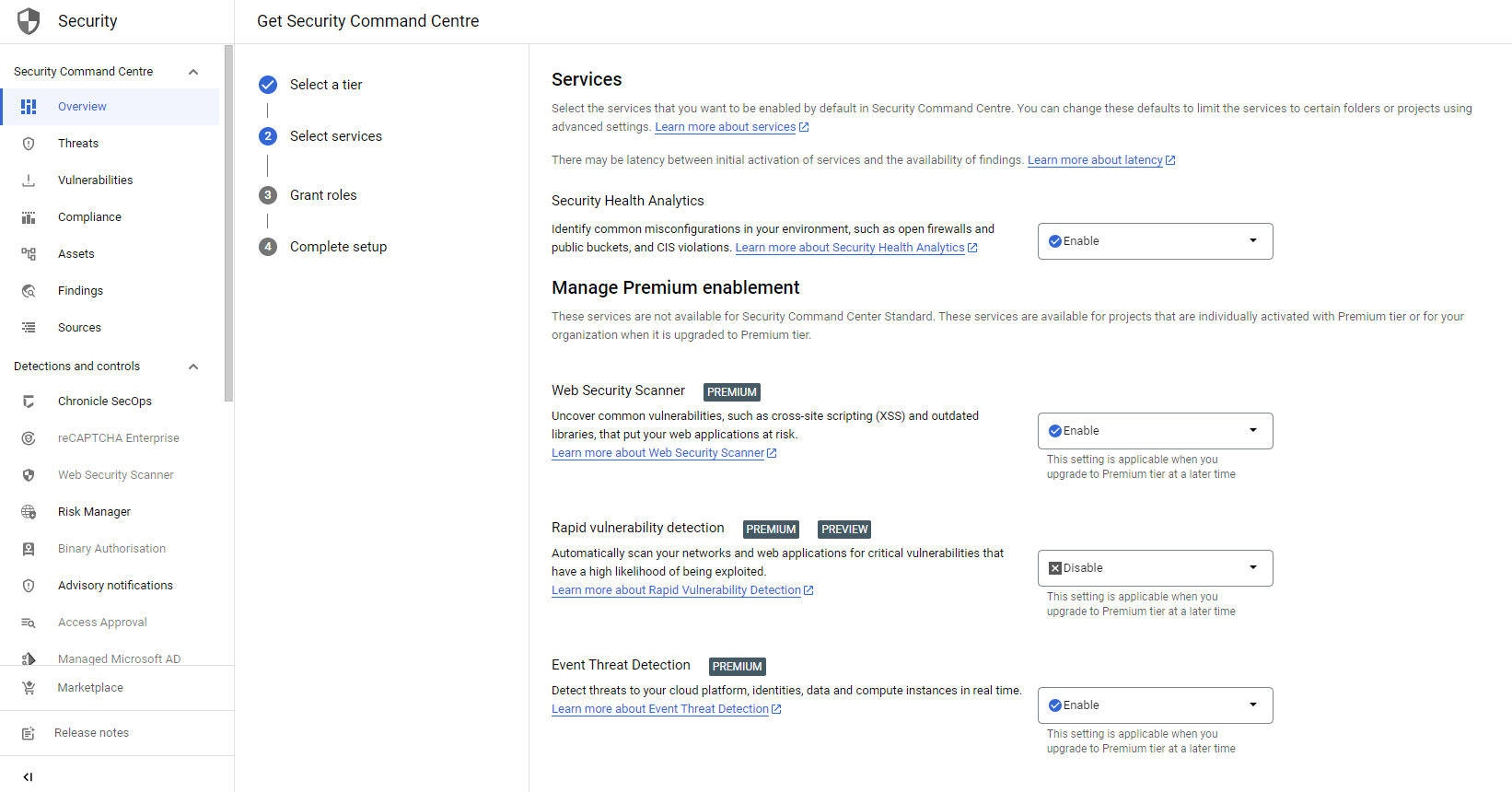
When activating SCC, you can choose to only activate a subset of services. One service which directly has an impact on your workloads is Rapid Vulnerability Detection. It automatically starts scanning all your assets. This could impact your production resources as it accesses administrator interfaces and tries to log into your VMs.
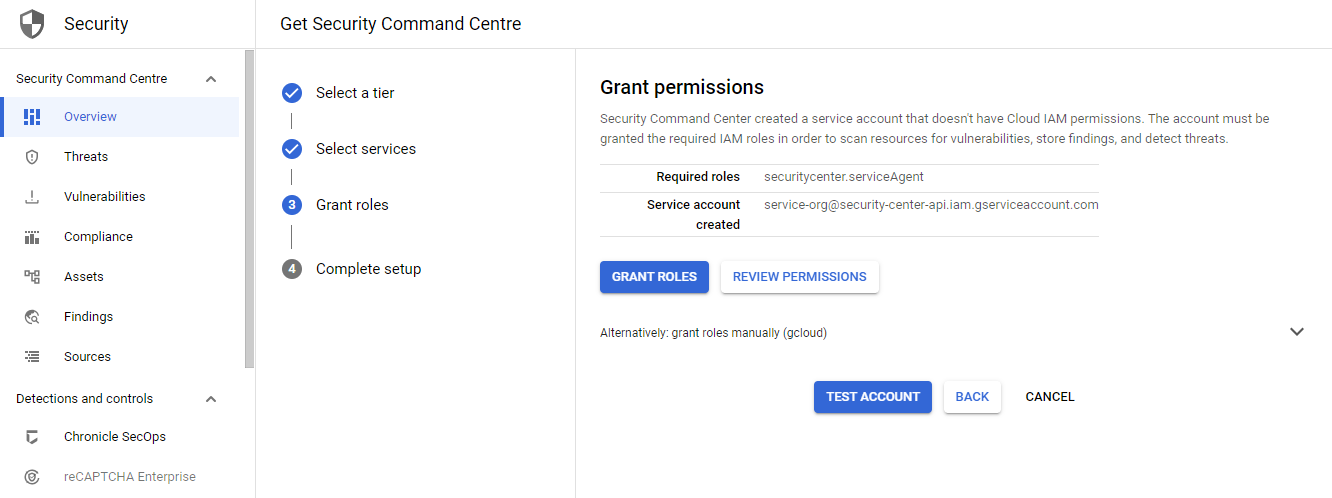
Lastly, SCC creates a separate service account, to which you need to attach roles. Don't worry - you don't need to create the service account as it's managed by Google. You only need to grant roles to the service account. This can be done directly from console or use the gcloud CLI.
$ gcloud organizations add-iam-policy-binding 1234567890 --member serviceAccount:service-org-1234567890@security-center-api.iam.gserviceaccount.com --role roles/securitycenter.serviceAgent
It will take a few seconds, and your first misconfigurations will appear in the overview.
My thoughts 💭
GCP SCC offers numerous positive aspects that can significantly enhance your cloud security. One of its key strengths lies in its compliance capabilities, allowing you to adhere to industry standards and regulations effortlessly. By leveraging SCC, you can gain insights into your compliance posture and assess whether your cloud infrastructure aligns with various frameworks. Whether you need to comply with the CIS benchmarks, NIST, ISO, or OWASP, the SCC empowers you to tailor your security measures accordingly, fostering a more secure and resilient cloud environment. Thereby ensuring that your organization meets essential security requirements.
Furthermore, the ability to create custom findings within the SCC is a notable benefit. This feature enables you to design specific rules and checks tailored to your organization's security needs. By doing so, you can address niche security concerns and pinpoint potential vulnerabilities that are specific to your cloud infrastructure. This results in a more comprehensive and personalized security approach. If you want to learn how to create custom findings, check out my previous article:

However, it is crucial to acknowledge that SCC also faces certain limitations. Some services within SCC may not be as mature as others. This might lead to discrepancies in the overall effectiveness of security assessments or the availability of advanced security functionalities. As a result, users should carefully evaluate their specific security requirements and consider supplementing the platform with additional security tools to fill in any gaps and ensure comprehensive coverage. One of those services is the Web Security Scanner, for example, it has some great potential, but can't replace a well-established Dynamic Application Security Testing (DAST) tool. If you want to learn more about the Web Security Scanner, you can check out my deep-dive:

In conclusion, SCC presents itself as a powerful tool for enhancing cloud security. However, it's important to be mindful of its potential limitations. By being aware of both the positives and negatives, organizations can make informed decisions and craft a robust security strategy that best suits their unique needs. If you need help deciding on the right setup, feel free to reach out to me or leave a comment below.










Member discussion