Introduction
Firewalls play a critical role in safeguarding your Google Cloud Platform (GCP) infrastructure from unauthorized access, malicious activities, and potential security breaches. 🔒 By implementing well-defined firewall rules, you can establish robust defenses and ensure the integrity and confidentiality of your data. In this article, we will explore the fundamental aspects of firewall rules and provide you with the knowledge to protect your GCP infrastructure effectively.
After following this article, you will also be able to fix any issues when receiving the following error message when connecting to a new compute instance via SSH: Your connection will most likely fail. VM is missing firewall rule allowing TCP ingress traffic from 0.0.0.0/0 on port 22. Or We are unable to connect to the VM on port 22. Please ensure that VM has a firewall rule that allows TCP ingress traffic from the IP range 0.0.0.0/0, port: 22.
Understanding Firewall Rules 🔥
Firewall rules act as a protective barrier, allowing or denying incoming and outgoing network traffic. In the context of GCP, firewall rules are essential for securing compute instances, load balancers, and other network resources. By explicitly defining the allowed connections and blocking unwanted traffic.
Firewall Rules 📏
Firewall rules are the individual configurations that define the traffic allowed or denied at the instance level. They are associated with specific tags, service accounts, or all instances. Firewall rules operate based on the priority assigned to them, rules with lower numbers get prioritized first.
Each firewall rule consists of criteria that define the characteristics of the traffic it applies to, such as the source IP range, destination IP range, protocol, destination, and port.
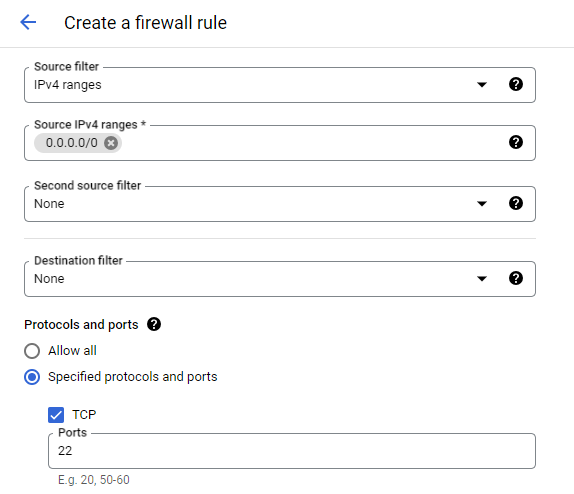
Create new firewall rule 📑
To create a new firewall rule, navigate to VPC network and click Create Firewall Rule. This will initiate the creation process.
Now we can configure the firewall rule.
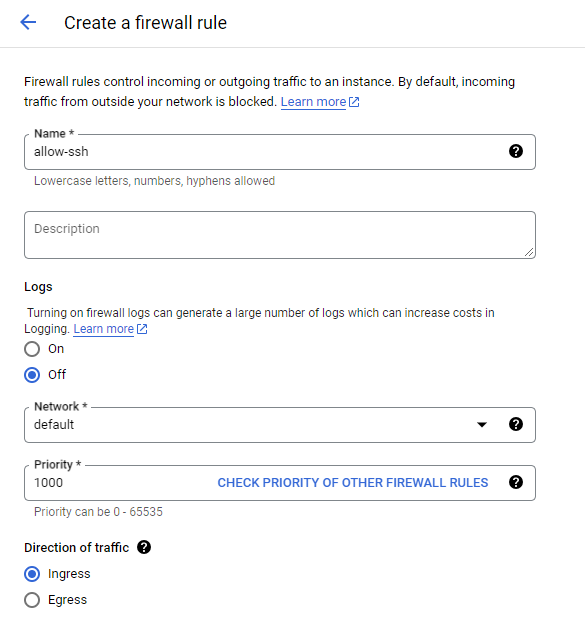
- Name and Description: Provide a meaningful name and description for the firewall rule to easily identify its purpose and functionality.
- Logs: Keep in mind that activating logging will incur additional costs.
- Priority: Assign a priority value to the rule to determine its precedence in relation to other firewall rules.
- Direction of traffic: Select whether the rule applies to ingress (incoming) or egress (outgoing) traffic.
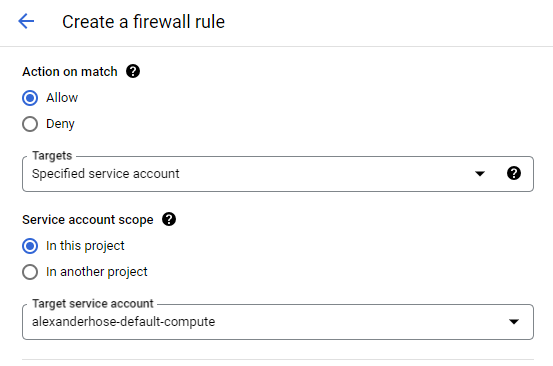
- Action: Specify the action to be taken for the matching traffic. Choose between allowing or denying the traffic.
- Targets: Define the targets for the rule. This can be a specific tag, a service account, or all instances within the network. If you want to select an individual service, it's advisable to use service accounts. Otherwise use network tags, if you want to select a group of services/instances (You need to assign the instances with the tag to apply the firewall rule).
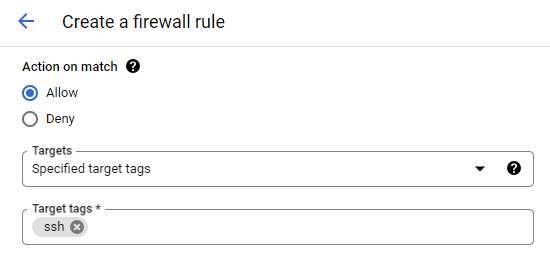
- Source and Destination: Set the source and destination filter to define the traffic's origin and destination.
- Protocols and Ports: Specify the protocols (TCP, UDP, or other) and ports (specific ports or port ranges) that the rule should match.
alexanderhose@gcp:~$ gcloud compute --project=<projectID> firewall-rules create allow-ssh --direction=INGRESS --priority=1000 --network=default --action=ALLOW --rules=tcp:22 --source-ranges=0.0.0.0/0 --target-service-accounts=<service-account-name>Check the assigned instances 🔬
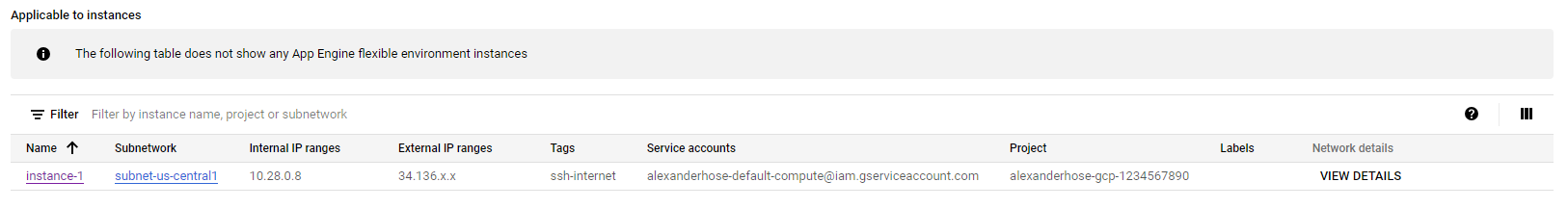
If you go to the firewall rule details after the creation. You can see to which instances it is assigned to.









Member discussion