Introduction
Jira Cloud is one of the most popular project management software solutions available, and it continues to grow in popularity. Jira has over 3.000 integrations, apps, add-ons, and plugins. Those can be mainly found in the official marketplace. In November AWS updated the AWS Service Management Connector for JSM to version 3.8.0. The newest version supports bidirectional integration with the AWS Security Hub. In this article, we walk through the integration and minimal setup of IAM.

Create KMS key
The first step is to create a new symmetric customer-managed key and attach the following key policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Enable IAM User Permissions",
"Effect": "Allow",
"Principal": {
"AWS": "arn:aws:iam::<accountID>:root"
},
"Action": "kms:*",
"Resource": "*"
},
{
"Sid": "Allow EventBridge",
"Effect": "Allow",
"Principal": {
"Service": "events.amazonaws.com"
},
"Action": [
"kms:Decrypt",
"kms:GenerateDataKey"
],
"Resource": "*"
}
]
}Create SQS queue
Second, we create a new SQS queue. The name should be AwsSmcJsmCloudForgeSecurityHubQueue as this is the common name that is set in the connector configuration. For the access policy, we are using the following permissions:
{
"Version": "2008-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "events.amazonaws.com"
},
"Action": "SQS:SendMessage",
"Resource": "arn:aws:sqs:<region>:<accountID>:AwsSmcJsmCloudForgeSecurityHubQueue",
"Condition": {
"ArnEquals": {
"aws:SourceArn": "arn:aws:events:<region>:<accountID>:rule/JIRADeliveryRule"
}
}
}
]
}Use the newly created KMS key for encrypting all messages that are sent to this queue.
Configure Amazon EventBridge rule
Afterward, we configure a new rule in Amazon EventBridge as JIRADeliveryRule. For the event source, we are choosing Security Hub and the event patterns should look like this:
{
"detail-type": ["Security Hub Findings - Imported"],
"source": ["aws.securityhub"]
}For the target, we are choosing the newly created SQS queue AwsSmcJsmCloudForgeSecurityHubQueue.
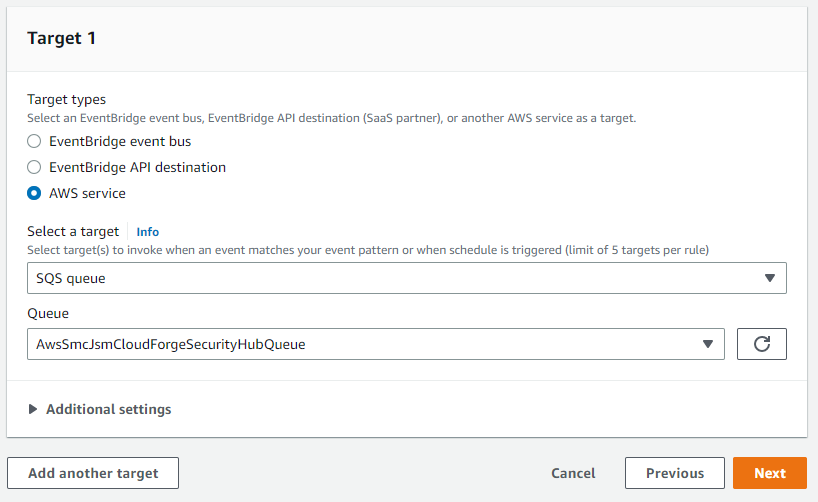
Create users for programmatic access
We need to create two users JIRASyncUser and JIRAEndUser. Later we configure the access key ID and secret access key of those users in the AWS Service Management Connector in JIRA. The two users will be used by the JIRA connector to interact with AWS.
JIRASyncUser
The first user JIRASyncUser is used for synchronizing AWS Security Hub alerts to JIRA. The user requires programmatic access and needs the following permissions attached:
{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"sqs:ReceiveMessage",
"sqs:DeleteMessage"
],
"Resource": "arn:aws:sqs:<region>:<accountID>:AwsSmcJsmCloudForgeSecurityHubQueue",
"Effect": "Allow"
},
{
"Action": [
"securityhub:BatchUpdateFindings"
],
"Resource": "*",
"Effect": "Allow"
}
]
}{
"Version": "2012-10-17",
"Statement": [
{
"Action": [
"kms:DescribeKey",
"kms:GenerateDataKey",
"kms:Decrypt"
],
"Resource": [
"arn:aws:kms:<region>:<accountID>:key/<keyID>"
],
"Effect": "Allow"
}
]
}Afterward, we note down the access key ID and secret access key.
JIRAEndUser
The second user we need is JIRAEndUser. The user requires programmatic access. Besides that, we do not need to attach any policies as this user is not required for the AWS Security Hub integration. We still need to note down the access key ID and secret access key as we need to configure it on JIRA.
Enjoy this article? Subscribe to receive the latest news about cloud security here 📫
Configure AWS Service Management Connector for JSM
Download the AWS Service Management Connector for JSM from the Atlassian Marketplace: https://marketplace.atlassian.com/apps/1221283/
Next, we are configuring the two users that we have created before. I would create an aggregation region for AWS Security Hub, so we only need to configure one region:
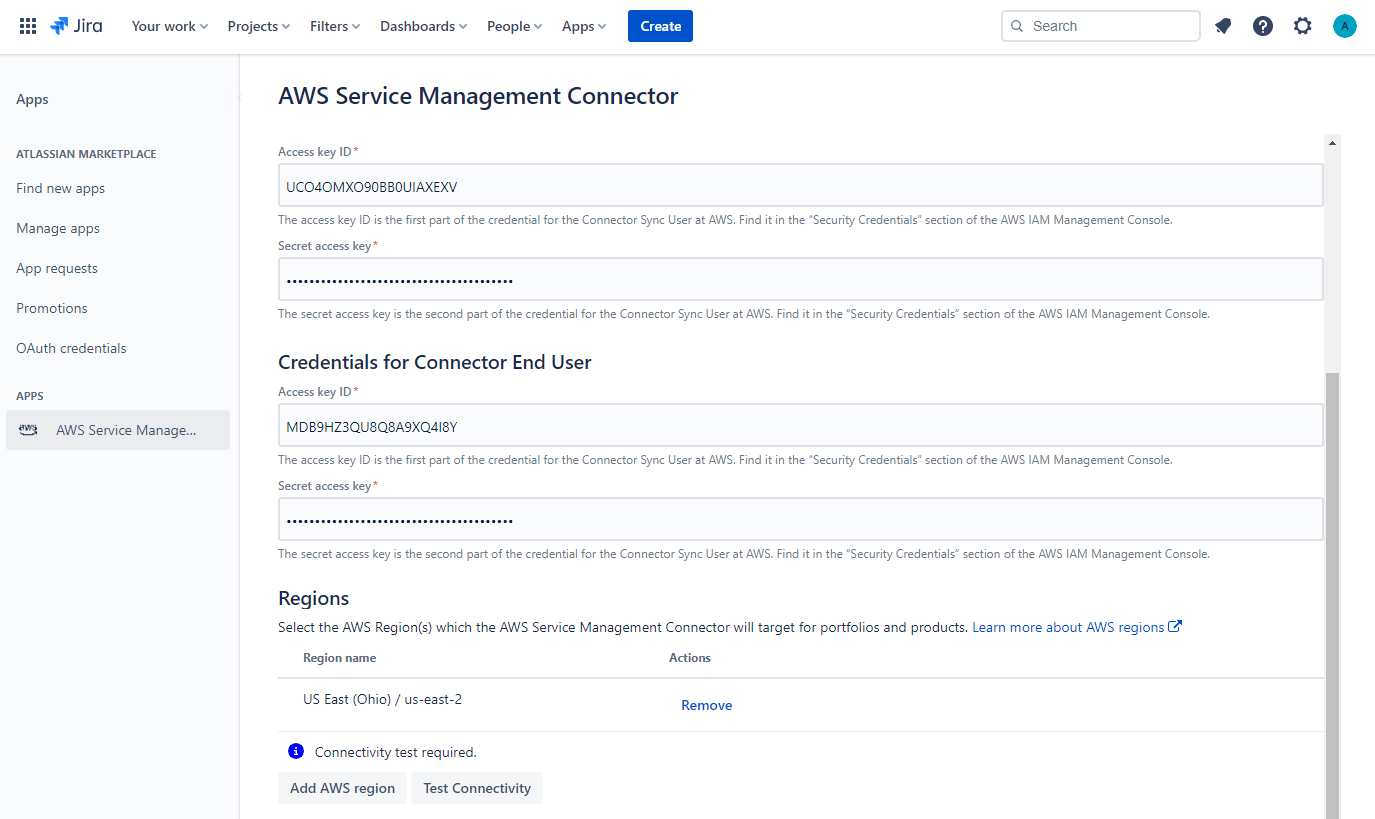
Once we have saved the configuration, we can go to the connector settings. We will activate AWS Security Hub only and choose the required severity values we want to import into JIRA Cloud. We can keep the SQS queue name and choose the JIRA project we want to synchronize. In my case, I have a dedicated JIRA project for all AWS alerts.
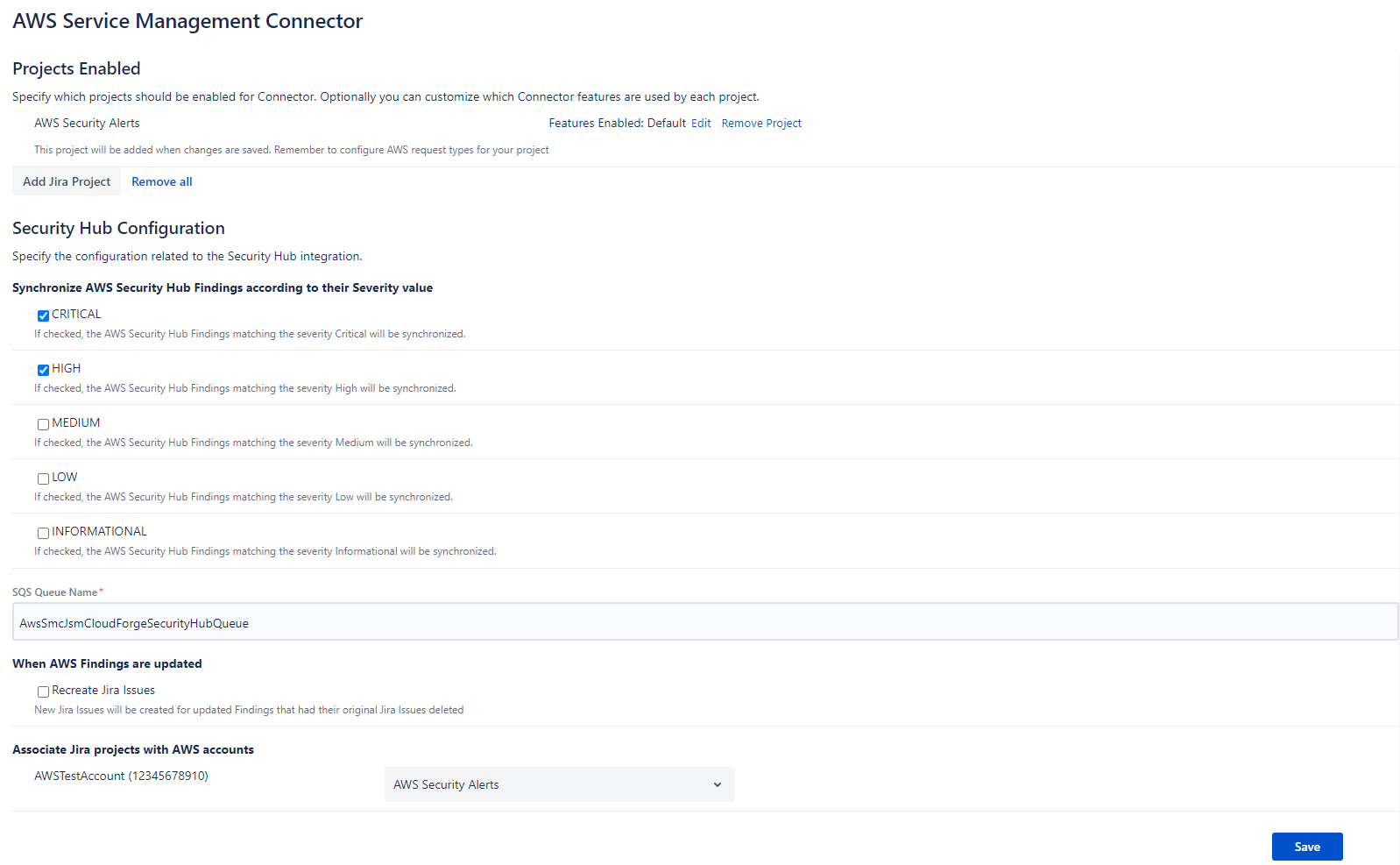
It takes a few seconds and the first alerts will appear in the issue section of JIRA.
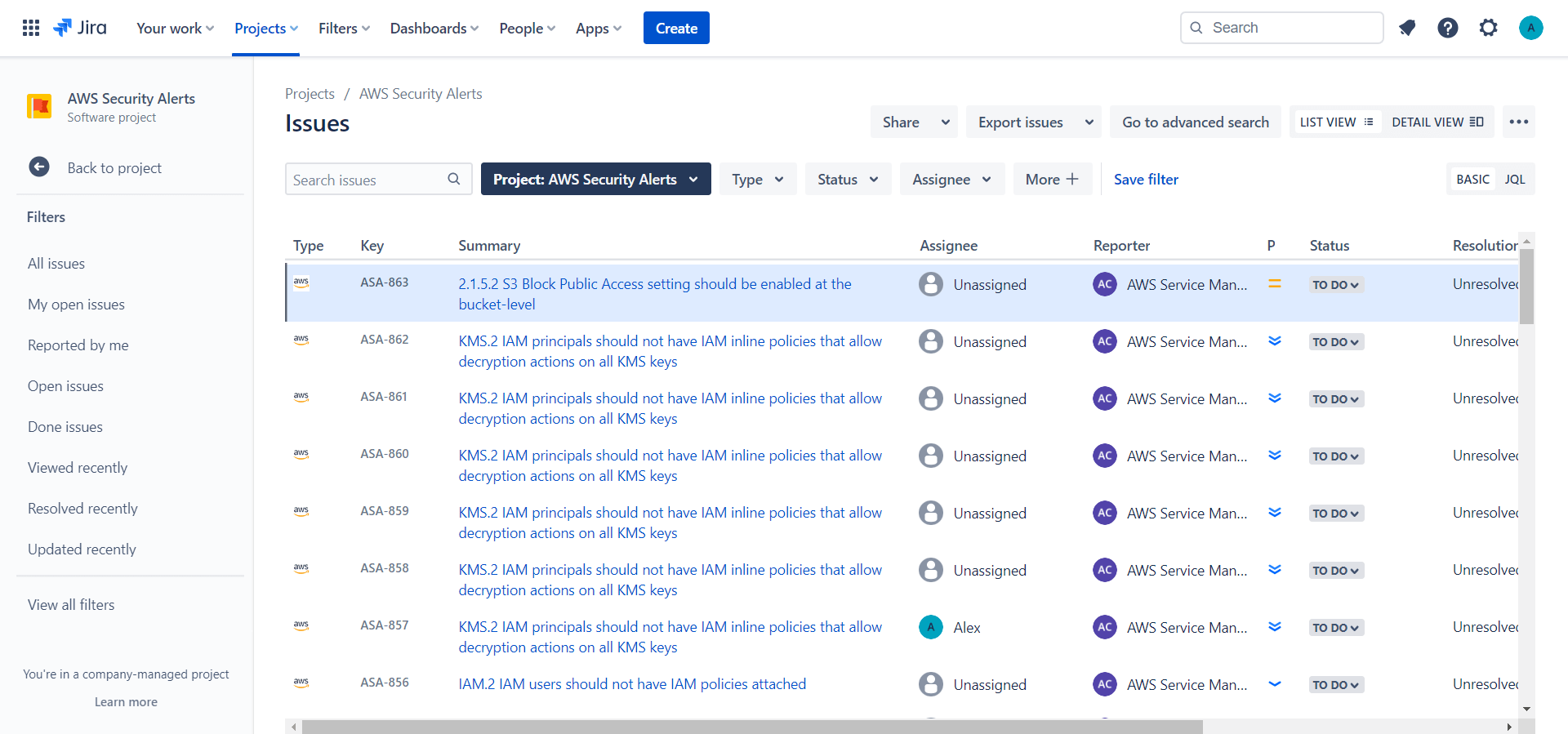
If you encounter any issues, you can go to admin.atlassian.com, choose Products, then your Site and Connected apps. From there you can download the logs of the connector.
CloudFormation Template
{
"Description": "AWS Service Management Connector for JIRA and integration with AWS Security Hub",
"Outputs": {
"JIRASyncUserAccessKey": {
"Value": {
"Ref": "JIRASyncUserAccessKeys"
}
},
"JIRASyncUserSecretAccessKey": {
"Value": {
"Fn::GetAtt": [
"JIRASyncUserAccessKeys",
"SecretAccessKey"
]
}
},
"JIRAEndUserAccessKey": {
"Value": {
"Ref": "JIRAEndUserAccessKeys"
}
},
"JIRAEndUserSecretAccessKey": {
"Value": {
"Fn::GetAtt": [
"JIRAEndUserAccessKeys",
"SecretAccessKey"
]
}
}
},
"Parameters": {
"SecurityHubQueueName": {
"Default": "AwsSmcJsmCloudForgeSecurityHubQueue",
"Type": "String"
}
},
"Resources": {
"SQSPolicy": {
"Type": "AWS::SQS::QueuePolicy",
"Properties": {
"Queues": [
{
"Ref": "AwsSmcJsmCloudForgeSecurityHubQueue"
}
],
"PolicyDocument": {
"Statement": [
{
"Action": "SQS:SendMessage",
"Effect": "Allow",
"Resource": {
"Fn::GetAtt": [
"AwsSmcJsmCloudForgeSecurityHubQueue",
"Arn"
]
},
"Principal": {
"Service": "events.amazonaws.com"
},
"Condition": {
"ArnEquals": {
"aws:SourceArn": {
"Fn::GetAtt": [
"JIRADeliveryRule",
"Arn"
]
}
}
}
}
]
}
}
},
"AwsSmcJsmCloudForgeSecurityHubQueue": {
"Properties": {
"KmsMasterKeyId": {
"Ref": "SQSQueueKey"
},
"QueueName": {
"Ref": "SecurityHubQueueName"
},
"Tags": [
{
"Key": "Name",
"Value": {
"Ref": "SecurityHubQueueName"
}
}
]
},
"Type": "AWS::SQS::Queue"
},
"JIRADeliveryRule": {
"Properties": {
"EventPattern": {
"detail-type": [
"Security Hub Findings - Imported"
],
"source": [
"aws.securityhub"
]
},
"Targets": [
{
"Arn": {
"Fn::Sub": "arn:aws:sqs:${AWS::Region}:${AWS::AccountId}:AwsSmcJsmCloudForgeSecurityHubQueue"
},
"Id": "JIRADeliveryRuleID"
}
]
},
"Type": "AWS::Events::Rule"
},
"JIRAEndUser": {
"Properties": {
"UserName": "JIRAEndUser",
"Tags": [
{
"Key": "Type",
"Value": "Programmatic access without 2FA"
}
]
},
"Type": "AWS::IAM::User"
},
"JIRAEndUserAccessKeys": {
"DependsOn": "JIRAEndUser",
"Properties": {
"Status": "Active",
"UserName": "JIRAEndUser"
},
"Type": "AWS::IAM::AccessKey"
},
"JIRASyncUser": {
"Properties": {
"Policies": [
{
"PolicyDocument": {
"Statement": [
{
"Action": [
"sqs:ReceiveMessage",
"sqs:DeleteMessage"
],
"Effect": "Allow",
"Resource": [
{
"Fn::GetAtt": [
"AwsSmcJsmCloudForgeSecurityHubQueue",
"Arn"
]
}
]
},
{
"Action": [
"securityhub:BatchUpdateFindings"
],
"Effect": "Allow",
"Resource": "*"
}
],
"Version": "2012-10-17"
},
"PolicyName": "AWSSecurityHubToJiraPolicy"
},
{
"PolicyDocument": {
"Statement": [
{
"Action": [
"kms:DescribeKey",
"kms:GenerateDataKey",
"kms:Decrypt"
],
"Effect": "Allow",
"Resource": [
{
"Fn::GetAtt": [
"SQSQueueKey",
"Arn"
]
}
]
}
],
"Version": "2012-10-17"
},
"PolicyName": "JIRASyncUserKMSKeyAccess"
}
],
"UserName": "JIRASyncUser",
"Tags": [
{
"Key": "Type",
"Value": "Programmatic access without 2FA"
}
],
},
"Type": "AWS::IAM::User"
},
"JIRASyncUserAccessKeys": {
"DependsOn": "JIRASyncUser",
"Properties": {
"Status": "Active",
"UserName": "JIRASyncUser"
},
"Type": "AWS::IAM::AccessKey"
},
"SQSQueueKey": {
"Type": "AWS::KMS::Key",
"Properties": {
"Description": "KMS key for SQS queue",
"KeyPolicy": {
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Enable IAM User Permissions",
"Effect": "Allow",
"Principal": {
"AWS": {
"Fn::Sub": "arn:aws:iam::${AWS::AccountId}:root"
}
},
"Action": "kms:*",
"Resource": "*"
},
{
"Sid": "Allow EventBridge",
"Effect": "Allow",
"Principal": {
"Service": "events.amazonaws.com"
},
"Action": [
"kms:Decrypt",
"kms:GenerateDataKey"
],
"Resource": "*"
}
]
}
}
}
}
}






Member discussion