During mid of October, AWS released the AWS Parameters and Secrets Lambda Extension. It makes it easier to retrieve parameters or secrets from the Systems Manager Parameter Store or AWS Secrets Manager. As the lambda function makes requests to different AWS services, we need to adjust the execution role. You can do that from the configuration tab. Make sure to add a policy, that enables you to use secretsmanager:GetSecretValue or ssm:GetParameter and kms:Decrypt on the required resources.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"kms:Decrypt",
"secretsmanager:GetSecretValue",
"ssm:GetParameter"
],
"Resource": "*"
}
]
}Enjoy this article? Subscribe to receive the latest news about cloud security here 📫
Furthermore, we need to add the new layer to the existing function. You can choose it directly from the AWS layers source.
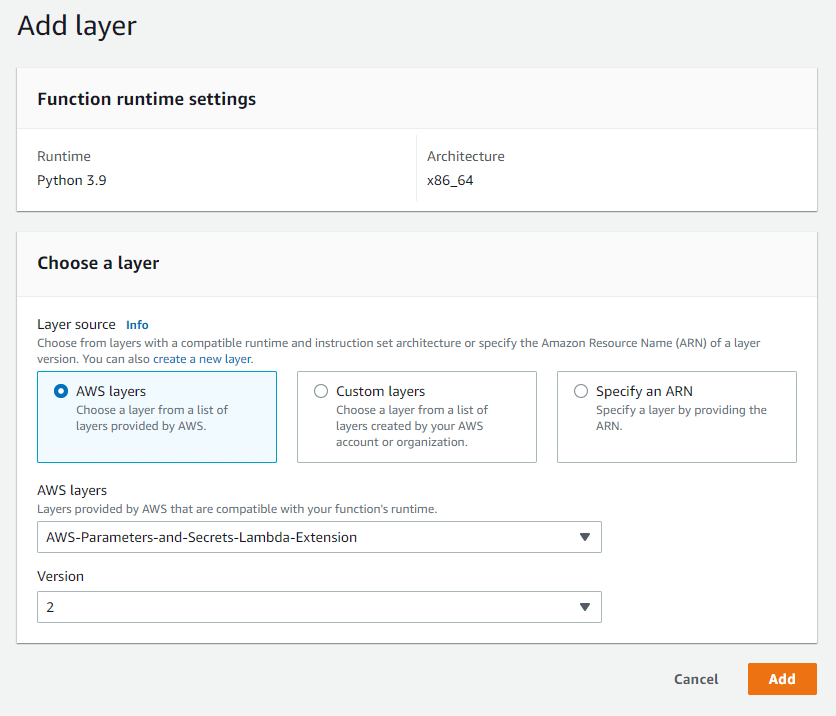
We need to retrieve the parameter or secret information from the extension cache. To make requests, we need to add the request header X-AWS-Parameters-Secrets-Token and the value AWS_SESSION_TOKEN both information is available from the running functions environment variables. Depending on the AWS service the extension offers different endpoints.
AWS Secrets Manager
GET: /secretsmanager/get?secretId=<SecretID>&versionId=<VersionID>&versionStage=<VersionStage>SecretID
The ARN or name of the secret to retrieve. Only this parameter is required to retrieve a secret.
VersionID
The unique identifier of the version. Usually, it is in the UUID format with 32 hexadecimal digits.
VersionStage
Specify the version by staging label or use AWSPREVIOUS for the previous version.
AWS Systems Manager Parameter Store
GET: /systemsmanager/parameters/get?name=<ParameterPath>?version=<Version>&label=<Label>&withDecryption={true|false}ParameterPath
The full parameter name or the parameter path.
Decryption
Required if you are using the SecureString option.
Example
To retrieve information from the AWS-Parameters-and-Secrets-Lambda-Extension you need to make requests to localhost on port 2773. You can then use the above-described endpoints.
Below is an example implementation in python:
import os
import urllib3
import json
def lambda_handler(event, context):
parameter_name = "LambdaExtensionsSecureParameter"
auth_headers = {"X-Aws-Parameters-Secrets-Token": os.environ.get('AWS_SESSION_TOKEN')}
http = urllib3.PoolManager()
r = http.request("GET", "http://localhost:2773/systemsmanager/parameters/get?name=" + parameter_name + "&withDecryption=true", headers=auth_headers)
parameter = json.loads(r.data)
return parameter["Parameter"]["Value"]







Member discussion