At the beginning of October AWS added the IAM Access Analyzer functionality to validate role trust policies directly in the AWS console. It guides you through adding each policy element, like actions or conditions, and provides context-specific documentation. To make your policies even more secure, it automatically checks for issues and gives specific suggestions and warnings.
Enjoy this article? Subscribe to our newsletter to receive the latest news about cloud security here 📫
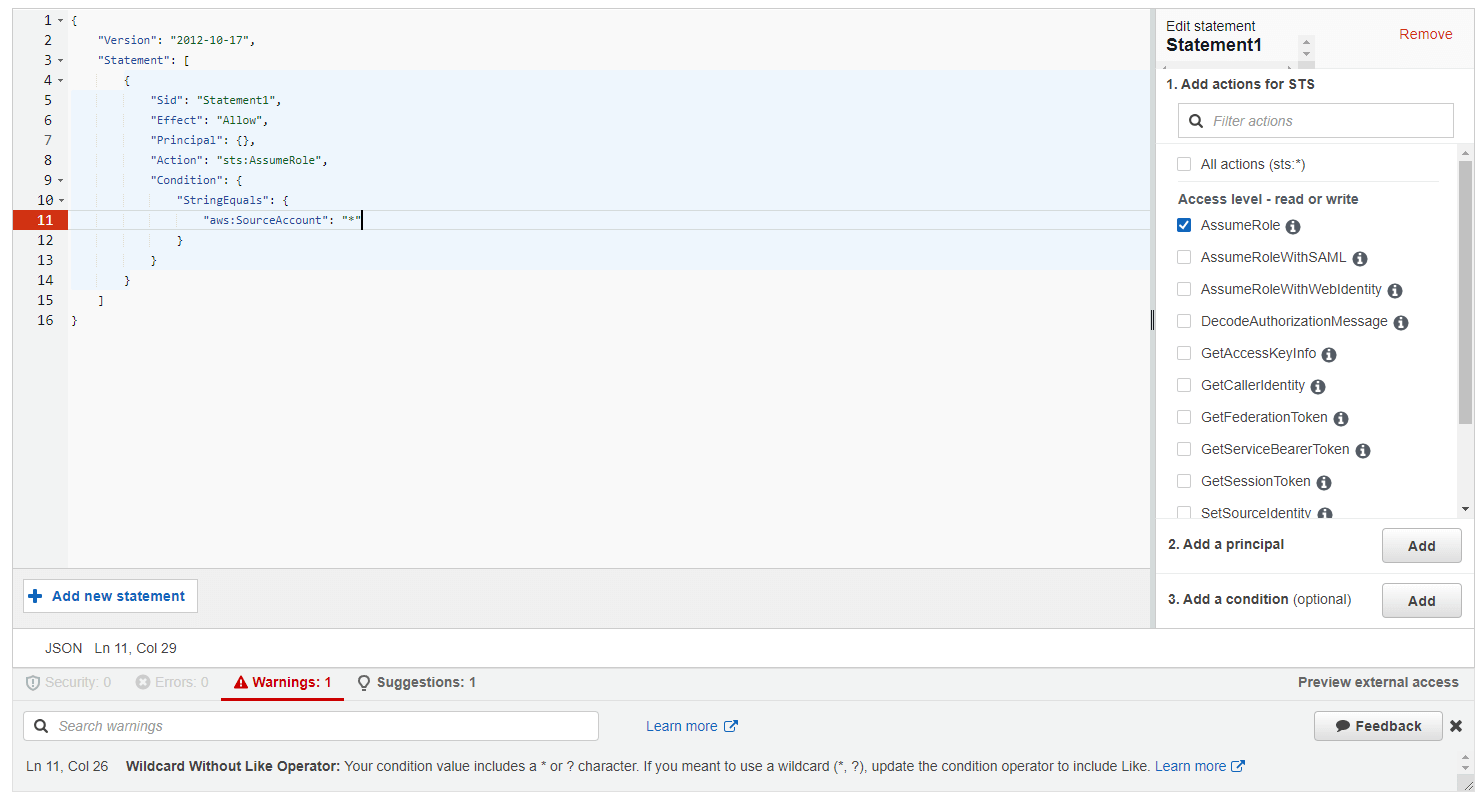
Additionally, you can preview external access to make sure only the intended access is allowed. Just click the preview external access button and choose your analyzer.
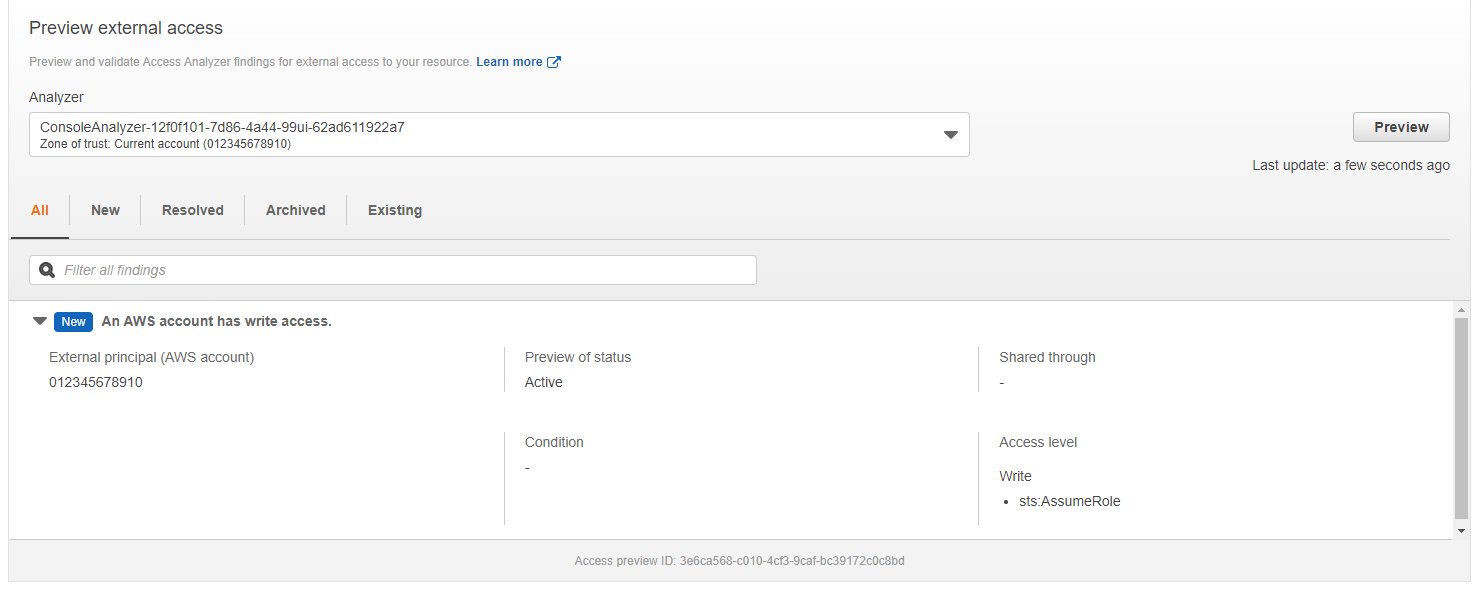
Besides the console changes, you can also use the existing API endpoints or AWS CLI, which got extended by the trust policy functionality. In the AWS console, you create a new policy document.
[[email protected] ~]$ vi policy
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "Statement1",
"Effect": "Allow",
"Principal": {},
"Action": "sts:AssumeRole",
"Condition": {
"StringEquals": {
"aws:SourceAccount": [
"*"
]
}
}
}
]
}Afterward, you validate the policy, reference the created policy document, and choose the policy type as RESOURCE_POLICY .
[[email protected] ~]$ aws accessanalyzer validate-policy --policy-type "RESOURCE_POLICY" --policy-document file://policy
{
"findings":[
{
"findingDetails":"Your condition value includes a * or ? character. If you meant to use a wildcard (*, ?), update the condition operator to include Like.",
"findingType":"WARNING",
"issueCode":"WILDCARD_WITHOUT_LIKE_OPERATOR",
"learnMoreLink":"https://docs.aws.amazon.com/IAM/latest/UserGuide/access-analyzer-reference-policy-checks.html#access-analyzer-reference-policy-checks-general-warning-wildcard-without-like-operator",
"locations":[
"..."
]
}
]
}







Member discussion