Introduced by Gartner in 2021, Cloud-Native Application Protection Platform promises a single pane of glass for all your cloud security needs. 🛡️ Imagine having all your security tools working together seamlessly, like the Avengers assembling to fight a threat! 💥
But what exactly is CNAPP, and how does it work? Let's dissect its six core components, understanding their individual strengths and how they combine to form an unbeatable security shield. ⚔️
Cloud Workload Protection (CWP) 🔒
Imagine an invisible forcefield around your cloud workloads (containers, VMs etc.). CWP acts as this shield, continuously monitoring for suspicious activity, malware, and unauthorized access. It also enforces security policies and isolates threats, preventing them from spreading like wildfire.
Example: A ransomware attack attempts to encrypt your critical cloud database. CWP detects the anomaly, isolates the infected workload, and prevents the attack from compromising your entire system.
Cloud Security Posture Management (CSPM) 🏰
Think of CSPM as your cloud security posture inspector. It continuously scans your cloud environment for misconfigurations, insecure settings, and compliance violations. By identifying these weaknesses, CSPM helps you proactively address security gaps before they become exploited.
Example: An IaaS misconfiguration accidentally exposes a sensitive data bucket to the public internet. CSPM detects this vulnerability and alerts your team, allowing you to fix the misconfiguration and prevent a potential data breach.
Cloud Infrastructure Entitlement Management (CIEM) 🛡️
This component focuses on identities and access within your cloud environment. CIEM grants visibility into user permissions, access controls, and activity logs. This helps identify and prevent insider threats or privileged account misuse.
Example: A service account with excessive access privileges attempts to download sensitive customer data. CIEM detects this suspicious activity and alerts security teams, allowing them to investigate and potentially prevent a data leak.
Vulnerability Management 🕵️♂️
This core function scans your cloud workloads for known vulnerabilities in software, libraries, and configurations. It prioritizes these vulnerabilities based on severity and exploits, allowing you to focus on patching the most critical risks first.
Example: A critical vulnerability is discovered in a popular open-source library used by your application. Vulnerability management identifies this risk and prioritizes it for patching, preventing attackers from exploiting the vulnerability to gain unauthorized access.
Code Security 🔒
Security shouldn't be an afterthought. Code security integrates security checks directly into the software development lifecycle, scanning code for vulnerabilities and insecure coding practices before applications are deployed.
Example: A developer unknowingly introduces a SQL injection vulnerability into their code. Code security scans identify this vulnerability during the development phase, allowing the developer to fix the code before it reaches production.
Network Security 🌐
While the focus is on cloud-native applications, securing the network traffic flowing to and from them remains crucial. Network security components within CNAPP provide firewalling, intrusion detection, and data loss prevention functionalities.
Example: An attacker attempts to inject malicious code into your web application through a web form. Network security features within CNAPP detect and block this attempt, protecting your application from being compromised.
Cloud-Native Security Solutions 🔐
While CNAPP offers a comprehensive security framework, several cloud providers offer native security solutions that can be stepping stones towards a more holistic CNAPP approach. Here's a breakdown of two prominent solutions: AWS Security Hub and GCP Security Command Center Enterprise (SCC Enterprise).
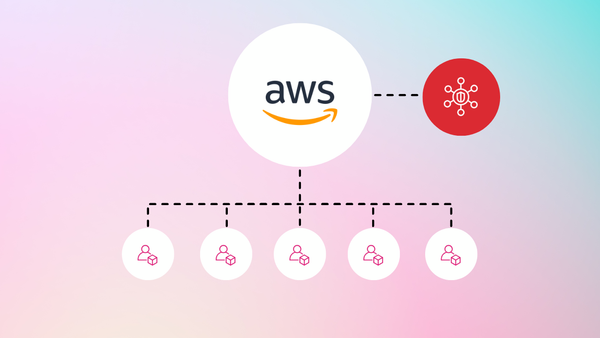
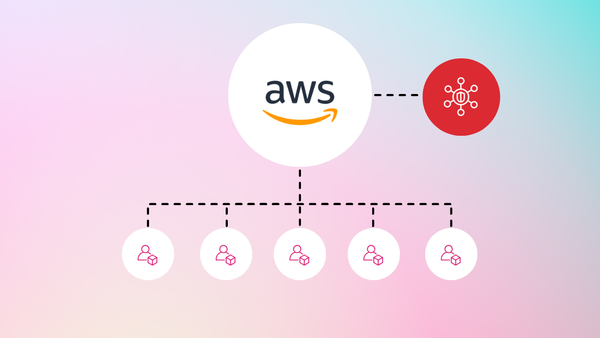
AWS Security Hub: Centralizing Security Findings in the AWS Cloud
AWS Security Hub acts as a central repository for security findings from various AWS security services, including GuardDuty, Inspector, and Macie. It provides a unified view of your security posture across your AWS accounts, allowing you to prioritize vulnerabilities and streamline remediation efforts.
Key Functionalities
- Security Posture Management (CSPM): Security Hub aggregates findings from various AWS services, highlighting misconfigurations that could create security gaps.
- Vulnerability Management: Security Hub integrates with vulnerability scanners, providing a consolidated view of identified vulnerabilities across your AWS environment.
Limitations to Consider
- Limited Scope: Security Hub primarily focuses on security findings within the AWS environment. For a more comprehensive CNAPP experience, integration with third-party tools for non-AWS environments is necessary.
- Actionable Insights: Security Hub excels at aggregating findings, but advanced threat detection and automated remediation functionalities might require additional tools or processes.
GCP Security Command Center Enterprise: A Multi-Cloud Security Powerhouse
SCC Enterprise builds upon the existing SCC, extending its functionalities beyond GCP to encompass multi-cloud environments like AWS and Azure. This makes it a compelling option for organizations managing workloads across diverse cloud platforms.
Key Functionalities
- Cloud Workload Protection (CWP): SCC Enterprise offers agentless and agent-based vulnerability scanning.
- Cloud Security Posture Management (CSPM): It helps identify security misconfigurations across GCP, AWS, and Azure.
- Threat Detection and Response: The platform leverages Google's threat intelligence and Mandiant expertise to detect threats, integrate response workflows, and visualize attack paths.
- Shift-Left Security: By offering Assured Open Source Software and IaC scanning, SCC Enterprise promotes secure coding practices and infrastructure configurations.
Limitations to Consider
- Integration with Third-Party Tools: While SCC Enterprise covers a vast array of security features, it might still require integration with additional third-party tools for a truly comprehensive CNAPP experience, especially for security needs outside the GCP, AWS, and Azure environments.
- Vendor Lock-In: Though it extends beyond GCP, SCC Enterprise is still a Google Cloud offering. Organizations seeking a completely vendor-neutral CNAPP platform might want to consider other options.
Now, here's the million-dollar question: How do you leverage the true power of CNAPP?
In my opinion, CNAPP's full potential can only be realized when all these components are tightly integrated into a single platform. Imagine a central command center where security teams can monitor threats, analyze data from all these functionalities, and orchestrate a unified response. Additionally, seamless integration with your internal DevOps and security processes is essential.

When CNAPP becomes an organic part of your development and security workflows, it empowers a proactive and holistic approach to cloud security. So, ditch the point solutions and fragmented tools. Embrace a truly integrated CNAPP platform!
Unlocking CNAPP's Full Potential: A Collaborative Effort 🤝
While a unified CNAPP platform is paramount, its true power lies not just in technology, but in its adoption across the organization. Here's where I believe a critical shift needs to happen – CNAPP procurement shouldn't be a solitary cloud security department endeavor.
Why Collaboration Matters
Imagine a situation where the cloud security department deploys a robust CNAPP platform, only to encounter resistance from developers due to a clunky user interface that hinders their workflow. Or picture security teams struggling to integrate CNAPP data with existing SIEM systems, creating data silos and hindering threat detection. These scenarios highlight the importance of a collaborative approach.
The Synergy of Departments
By involving key stakeholders from Security, Development, and Operations during the CNAPP selection process, organizations can ensure a solution that aligns with everyone's needs. Security teams can define essential functionalities, developers can provide feedback on usability, and operations can assess the platform's manageability. This collaborative approach fosters a sense of ownership and increases the likelihood of successful implementation.
The Benefits of a United Front
A cross-departmental approach to CNAPP procurement offers several advantages:
- Improved User Adoption: When developers and security teams are involved in the selection process, they're more likely to embrace the chosen platform, leading to better user adoption and a more effective security posture.
- Streamlined Integration: Collaboration across departments allows for smoother integration with existing workflows and systems, eliminating data silos and maximizing the platform's value.
- Holistic Security Strategy: By involving various stakeholders, organizations can develop a more comprehensive security strategy that addresses the specific needs of each department, leading to a more robust security posture.
Conclusion 🎓
CNAPP offers a powerful suite of tools for securing cloud-native applications. However, to unlock its full potential, organizations need to move beyond departmental silos and embrace a collaborative approach to procurement. By involving key stakeholders from across the organization, businesses can ensure a CNAPP platform that is not just powerful, but also seamlessly integrated into their existing workflows, empowering a truly holistic approach to cloud security.





Member discussion