The Most Underrated Service in GCP? It's Not What You Think.
In the world of cloud security, we are obsessed with the new, the complex, and the cutting-edge. We talk about advanced threat intelligence feeds, sophisticated eBPF-based runtime security, and AI-powered anomaly detection. But what if the most impactful security service in GCP is one that’s been there all along, waiting to be used to its full potential?
In my opinion, the most underrated service in the GCP is the Security Command Center.
I know what you might be thinking. "A dashboard? That's your pick?" Yes. Because in a world where security professionals are drowning in alerts and fighting dashboard fatigue, a tool that provides genuine clarity is the most valuable asset you can have. We often think of security as adding more tools, which inevitably means more noise. SCC does the opposite. It provides a single, unified view of your security posture from day one. 📊
The Power of a True Single Pane of Glass
The term "single pane of glass" is one of the most overused phrases in cybersecurity marketing. It usually means yet another dashboard that pulls in some, but not all, of your data.
Security Command Center, however, comes closer to delivering on this promise than almost any other native tool I’ve seen. Its first and most immediate benefit is centralization. Just by activating it, you get immediate visibility into critical misconfigurations across your entire GCP organization. It’s not just about finding one or two things; it’s about a comprehensive, prioritized overview of your risk. Out of the box, it will start flagging common but dangerous issues like:
- Publicly exposed storage buckets.
- Compute instances with public IP addresses that shouldn't have them.
- Overly permissive IAM.
- Disabled audit logging for critical services.
Having this information in one place is powerful, but the real value comes from prioritization. SCC assigns a severity level to each finding, allowing your team to focus on what truly matters instead of chasing down low-impact alerts. Once you have this centralized data, you can build powerful workflows around it, such as exporting findings to Pub/Sub to integrate with your SIEM, create automated tickets in Jira, or trigger remediation functions.
It Grows With You, Effortlessly
Here's the most powerful part, and the reason it’s so underrated: SCC is designed as a platform, not just a product. It scales with you, effortlessly. As your organization matures and you enable more of GCP's native security services, their findings are automatically integrated into your SCC dashboard. 🧩
Services like Security Health Analytics, Web Security Scanner, Event Threat Detection, and Container Threat Detection all feed their findings directly into SCC. This means your single pane of glass becomes more intelligent and comprehensive over time without you having to configure dozens of new integrations. It’s a prime example of a tool that embraces the CNAPP philosophy of integration. For example, as you implement tools to discover sensitive data using Cloud Data Loss Prevention, those findings can appear directly in SCC, giving you a direct line of sight from a data-at-risk finding to the infrastructure that hosts it.

My Favorite Feature: Visualizing the Attacker's Journey
Where SCC truly shines for me is with its Attack Path Simulation feature. This is where it graduates from a simple dashboard to a genuine strategic tool. Security teams are often stuck playing a numbers game, chasing vulnerabilities based on a CVSS score. An "8.5" is critical, a "6.0" is medium. But this score lacks context. An 8.5 vulnerability on an isolated development server with no sensitive data is far less of a risk than a "medium" 6.0 vulnerability on a server that has a direct path to your customer database. Attack Path Simulation provides that missing context. It visualizes how an attacker could chain multiple, seemingly low-risk findings together to create a high-impact breach.
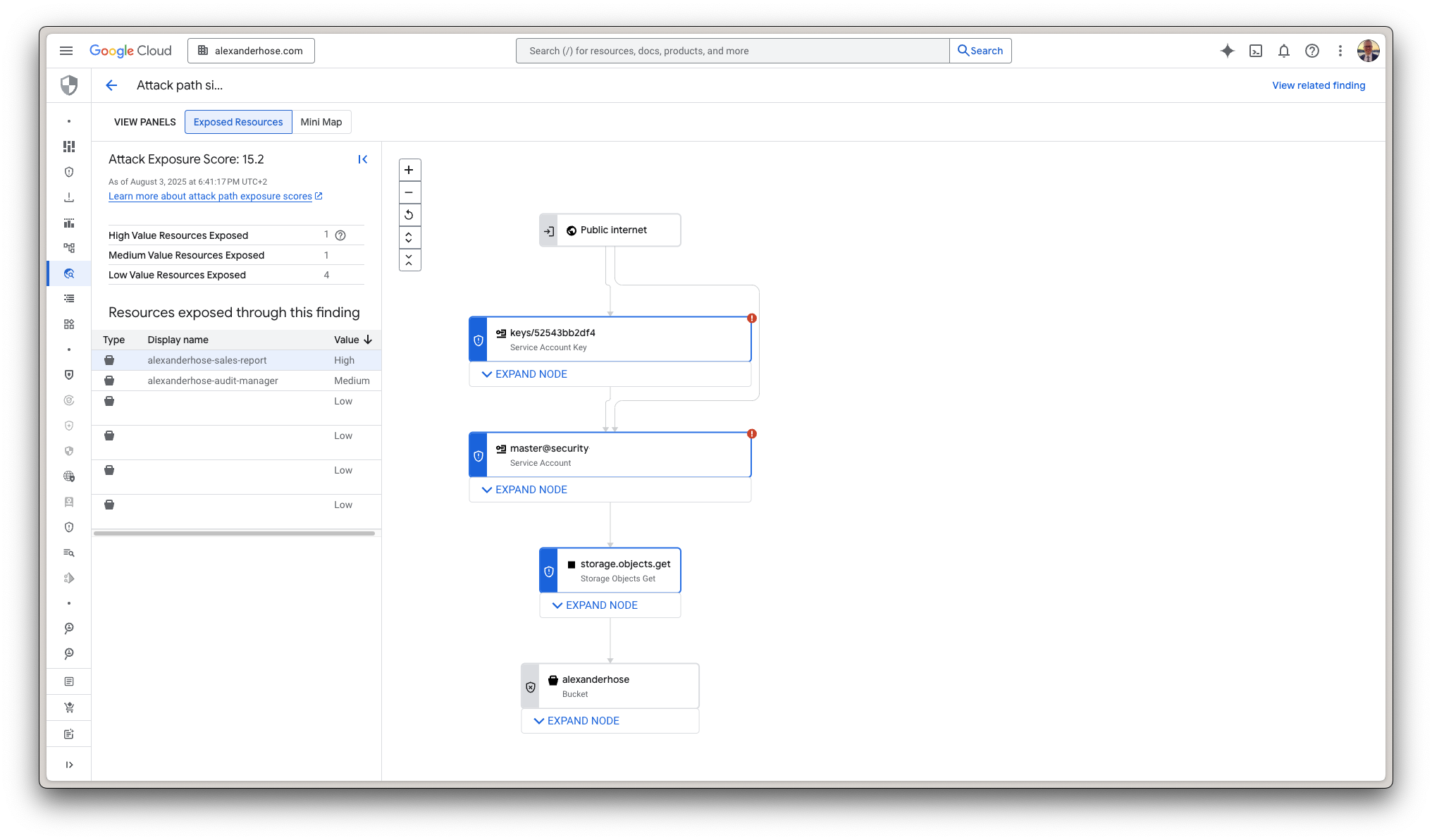
Imagine this scenario: SCC flags a publicly exposed storage bucket (a low-severity finding). On its own, it’s a minor issue. But the attack path simulation might show that this bucket contains a configuration file with a service account key (a medium-severity finding), and that service account has overly permissive roles that grant access to a production BigQuery dataset (a critical asset). Suddenly, three separate findings are connected into a single, critical attack path. This allows you to prioritize the fix that breaks the chain and provides the biggest risk reduction, not just the one with the highest score.
Taking SCC to the Next Level: Making It Your Own
Once you've mastered the built-in capabilities, SCC becomes a powerful platform for customization. This is where you can truly tailor it to your organization's unique risk profile.
- Custom Threat Detections: While the built-in detectors are excellent, you might have specific compliance requirements or internal policies that they don't cover. You can build your own custom threat detections to monitor for these unique scenarios, turning SCC into a bespoke monitoring

- Custom Policies for Prevention: Detection is good, but prevention is better. By creating custom policies, you can move from simply finding misconfigurations to actively preventing them from happening in the first place. This is a key step in maturing your security

- A Single Source of Truth: Do you use third-party security scanners? You can create custom findings and ingest their alerts into SCC. This allows you to consolidate alerts from your entire security toolchain, making SCC the one true source of truth for your security posture.

The Foundation for a Mature Security Program
Many tools solve a single problem. A good firewall blocks traffic; a good scanner finds vulnerabilities. But a mature security program isn't just a collection of tools - it's an integrated system that provides a holistic view of risk.
From here, you can create custom detections, automate responses, and, most importantly, gain the strategic visibility needed to make informed, risk-based decisions. It enables a proactive, intelligent, and scalable security posture. And that's why it deserves a place at the very center of your GCP security strategy.









Member discussion