Introduction
When it comes to cloud security, managing who has access to what is absolutely crucial. Organizations are constantly looking for secure ways to manage elevated permissions without compromising security. Google Cloud Platform's (GCP) new PAM product, Privileged Access Manager, solves the issue of handling temporary access to critical resources. 🎉
Traditionally, many organizations have relied on "break the glass" accounts for urgent security-related tasks, but these come with their own set of challenges and risks. While IAM conditions offer some control, GCP’s PAM provides a more streamlined and secure approach, ensuring that temporary access is managed efficiently and effectively. 🔒
Today, I’ll walk you through a practical guide on using PAM to create an entitlement, request access via a grant, and approve it to gain access to GCP compute engine service. By the end of this tutorial, you’ll see how PAM can be implemented for managing privileged access in your cloud environment.
Step 1: Creating an Entitlement
The first step in leveraging PAM is to create an entitlement. Entitlements define the access rights and permissions that can be temporarily granted to users.
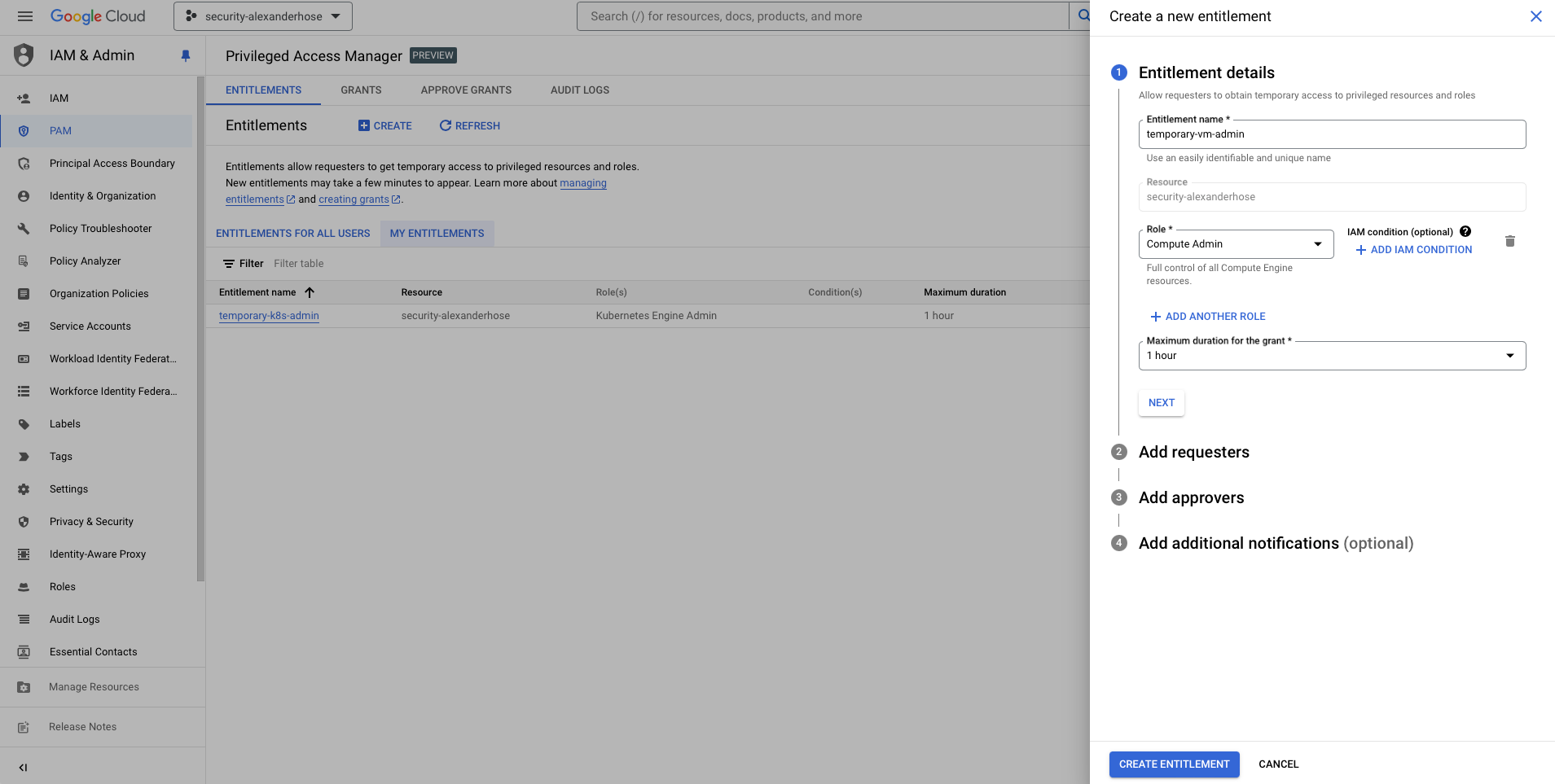
Create a New Entitlement
- Provide a name and description for the entitlement (e.g.,
temporary-vm-admin). - Define the roles and permissions associated with the entitlement. For this example, let's include roles that grant access to compute instances. You can also modify it even further with IAM conditions.
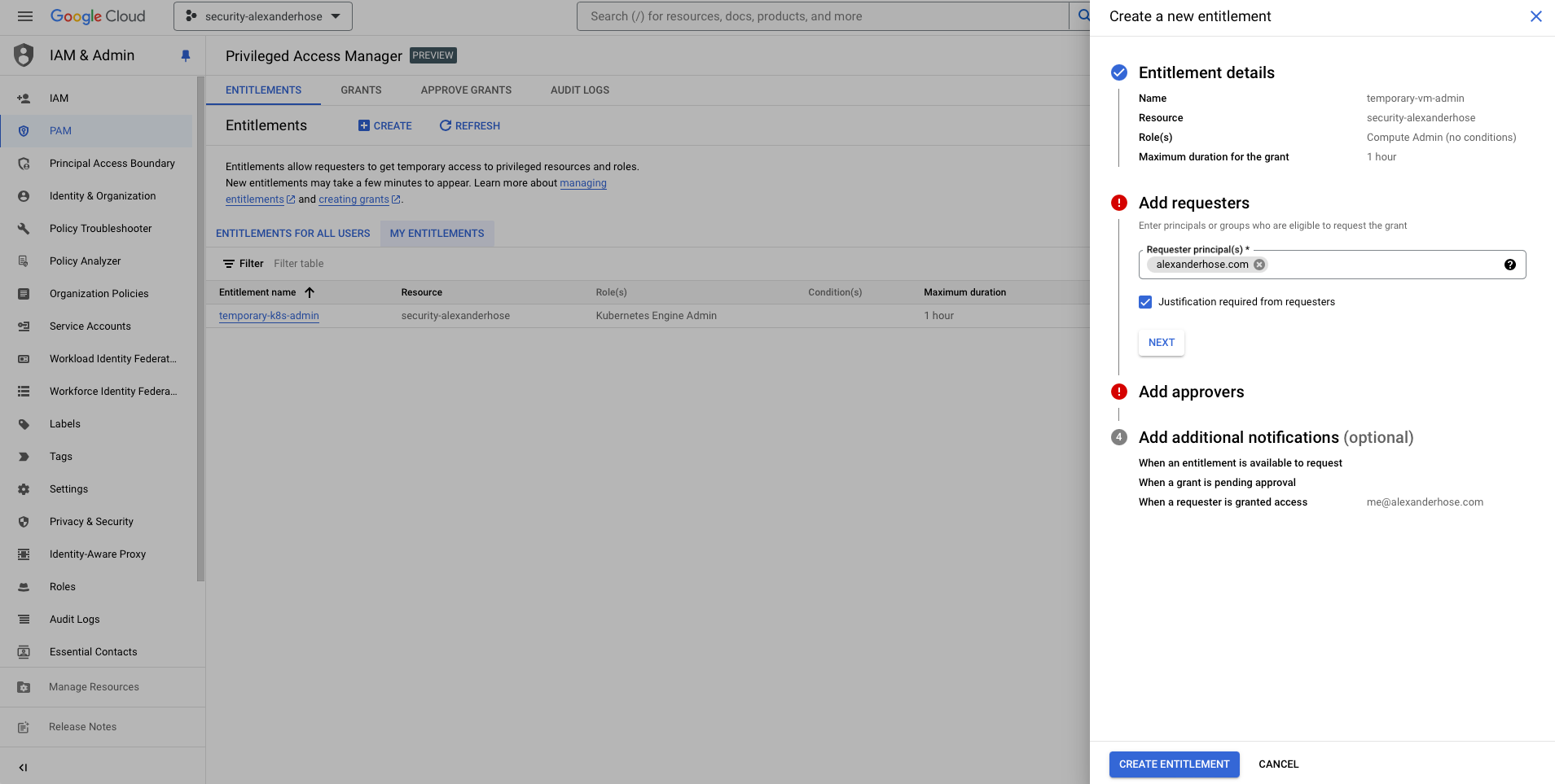
Set the Requestor Information
Add the requestor information by including one or more of the following (Those are able to request the grant):
- Google Account email:
[email protected] - Google Group:
[email protected] - Service account:
[email protected] - Google Workspace domain:
alexanderhose.com
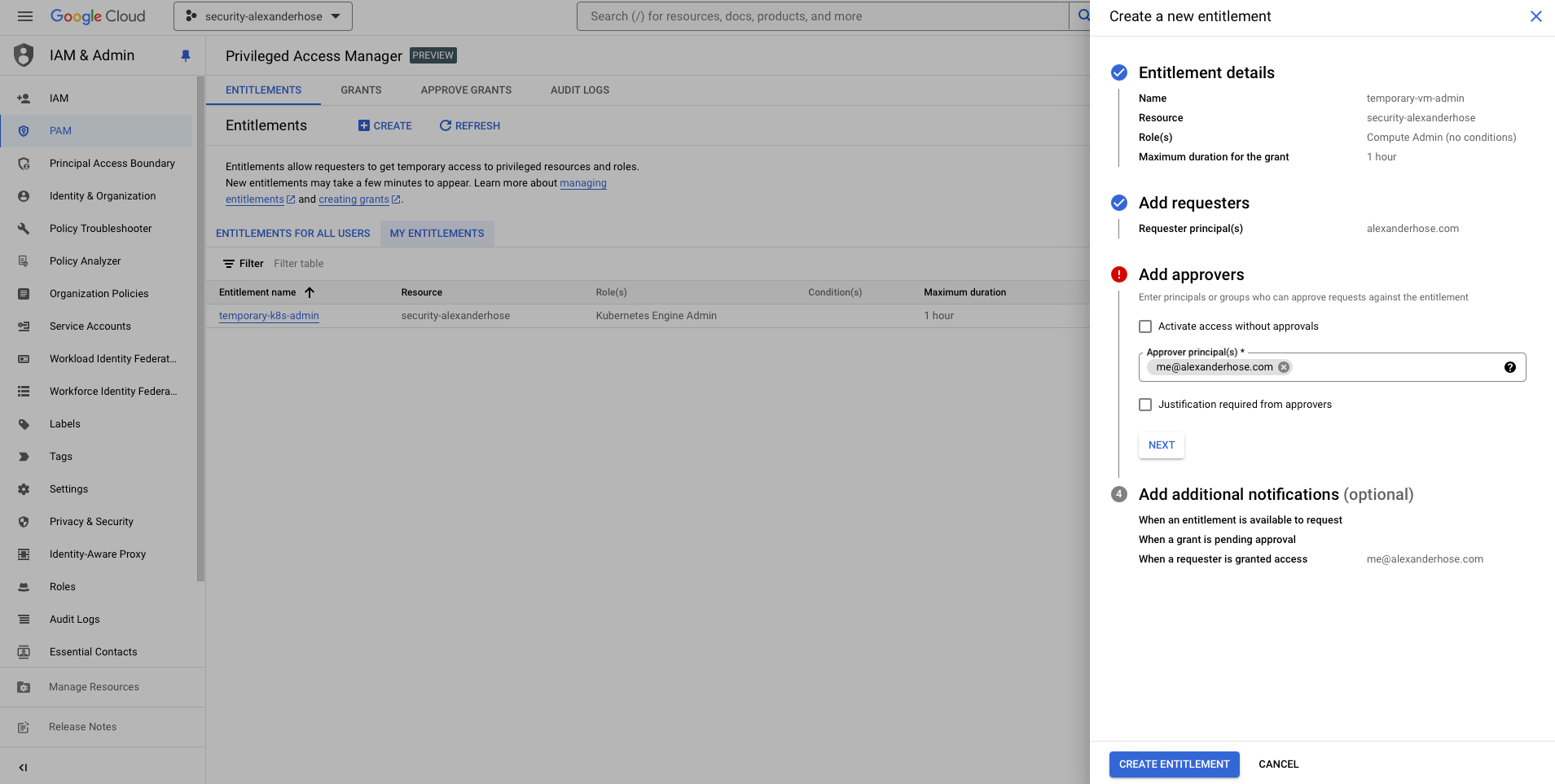
Choose the Approvers
Add the email addresses of the approvers who can approve or deny access requests. In this case, it will be my own email address: [email protected].
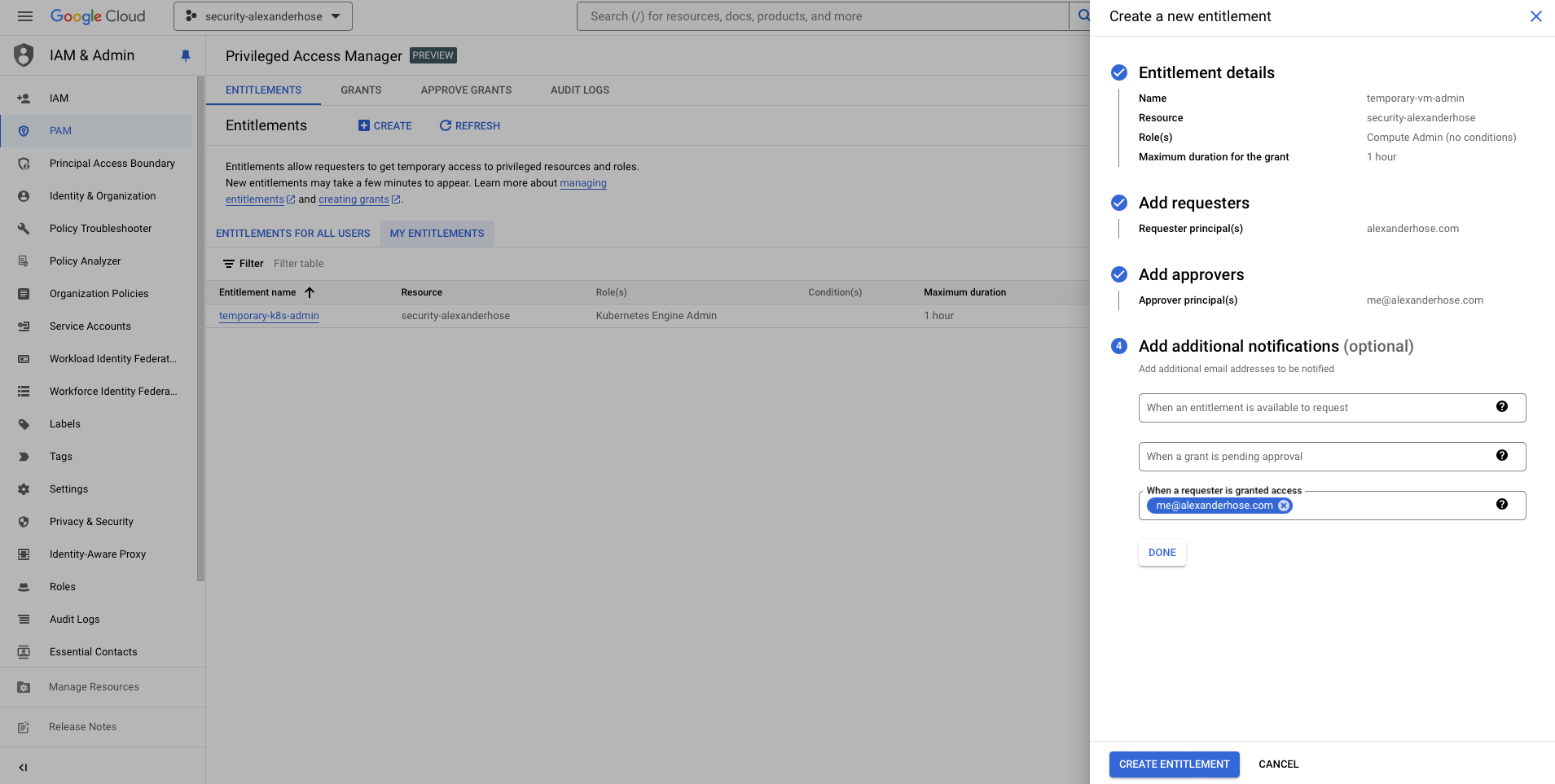
Optional: Add Additional Notifications:
- Notification for Entitlement Availability:
- These email addresses will be notified when an entitlement is available for use. They can request a grant if they are also listed as requesters for the entitlement.
- Notification for Grants Awaiting Approval:
- These email addresses are notified about grants that are awaiting approval. They can approve or deny access if they are also listed as approvers for the entitlement.
- Notification for Granted Access:
- These email addresses will be notified when a requester is granted access.
Step 2: Requesting Access via a Grant
Now that we have an entitlement created, the next step is for a user to request access to it. Without the grant, the user is not able to access the compute instance service.
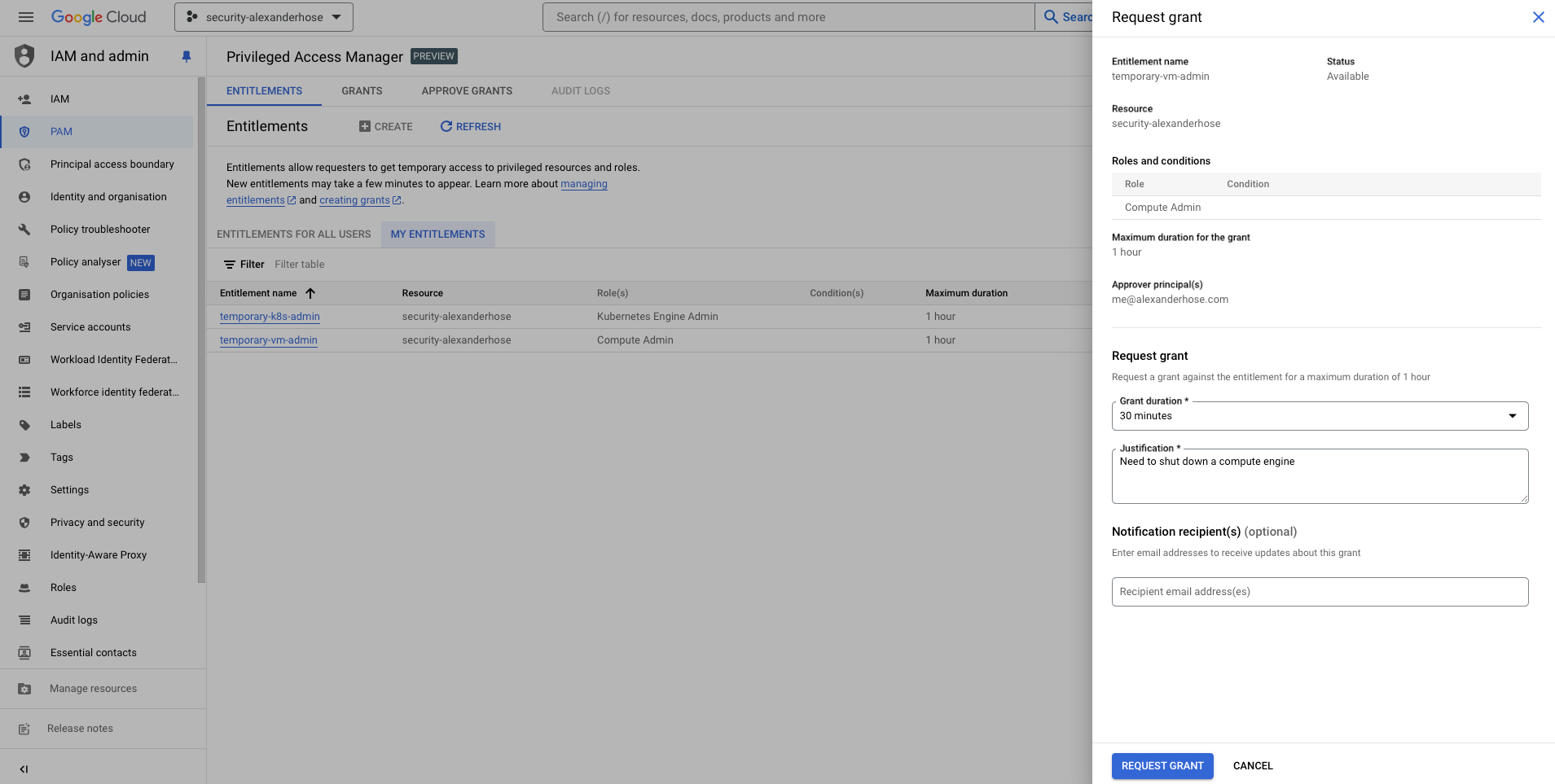
Request the Grant
Navigate to the PAM dashboard and find the previously created entitlement, temporary-vm-admin. Choose the duration for which the access is needed and provide a justification for the request and submit it. The approver will receive an email notification to approve the grant.
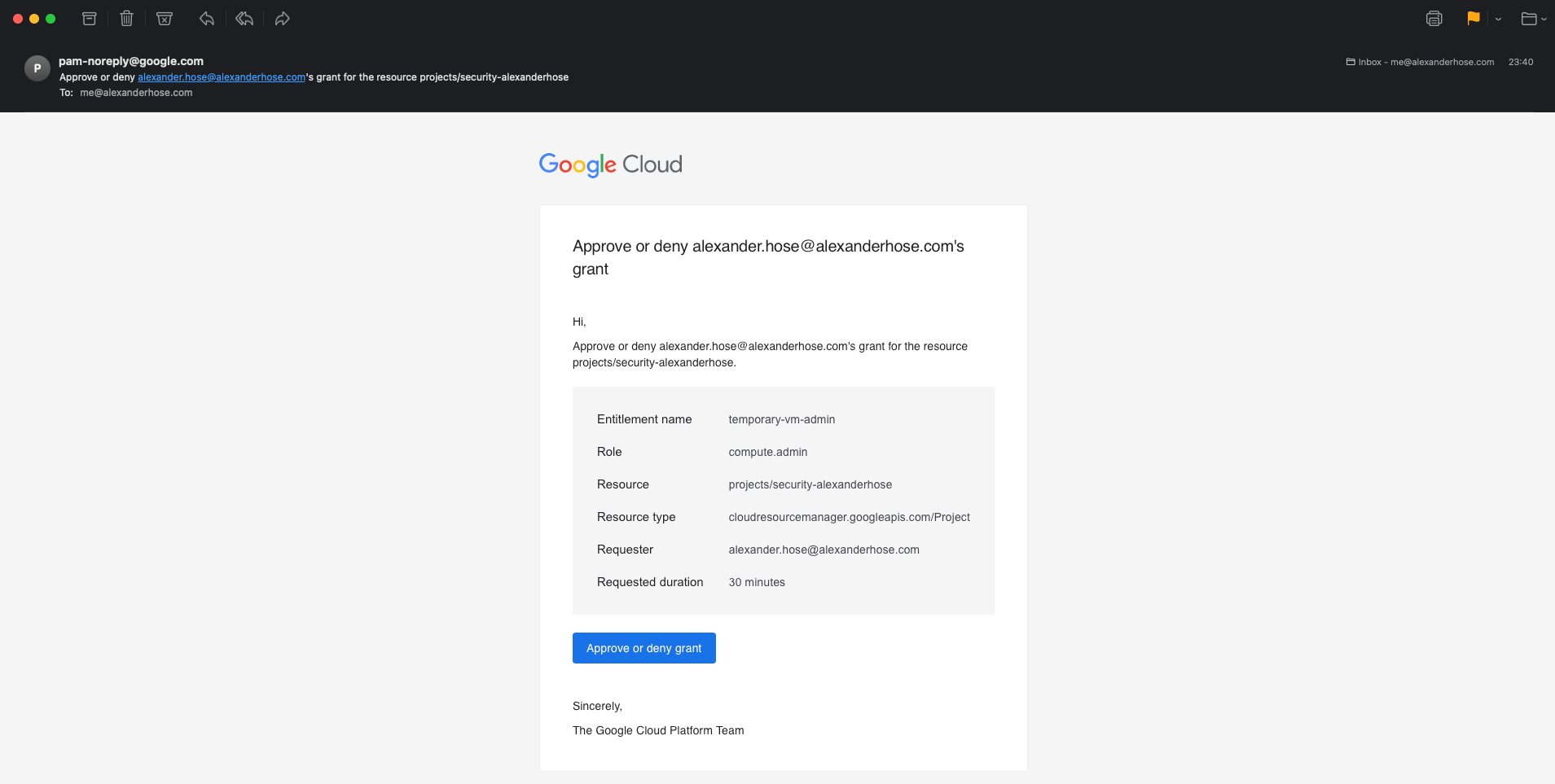
Step 3: Approving the Access Request
With the access request submitted, it’s time to approve it from the main account.
Approve the Request
The approver will receive an email notification about the grant request. By clicking on the link in the email, they will be brought directly to the PAM dashboard to approve the grant.
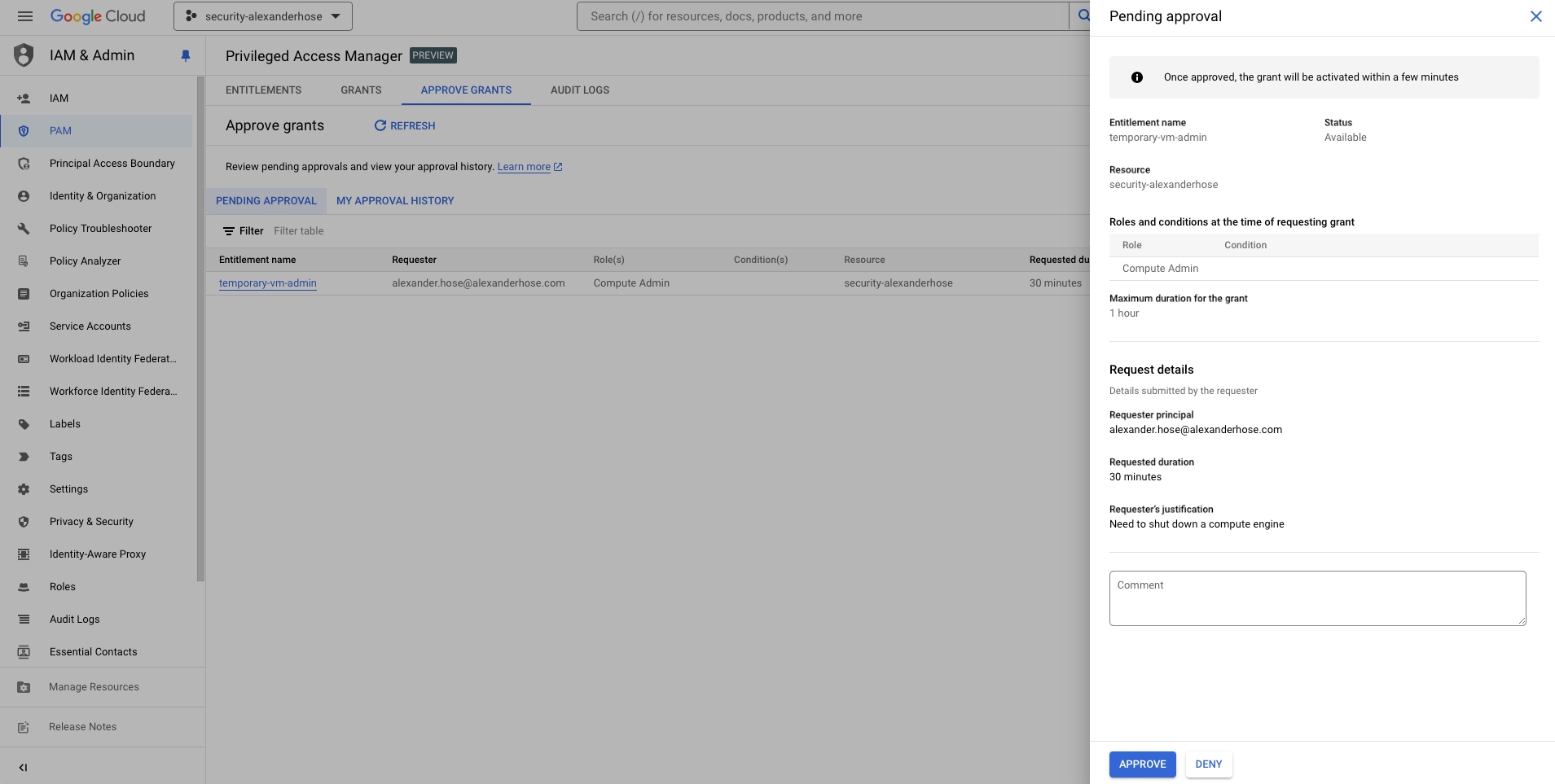
Grant Access
Add any necessary comments and approve the request. All requests are logged in the audit logs for compliance and tracking. Once approved, the entitlement is granted, and the requester account will have temporary access to the specified resources or services. Keep in mind that the duration of the grant will start once the approval is submitted.
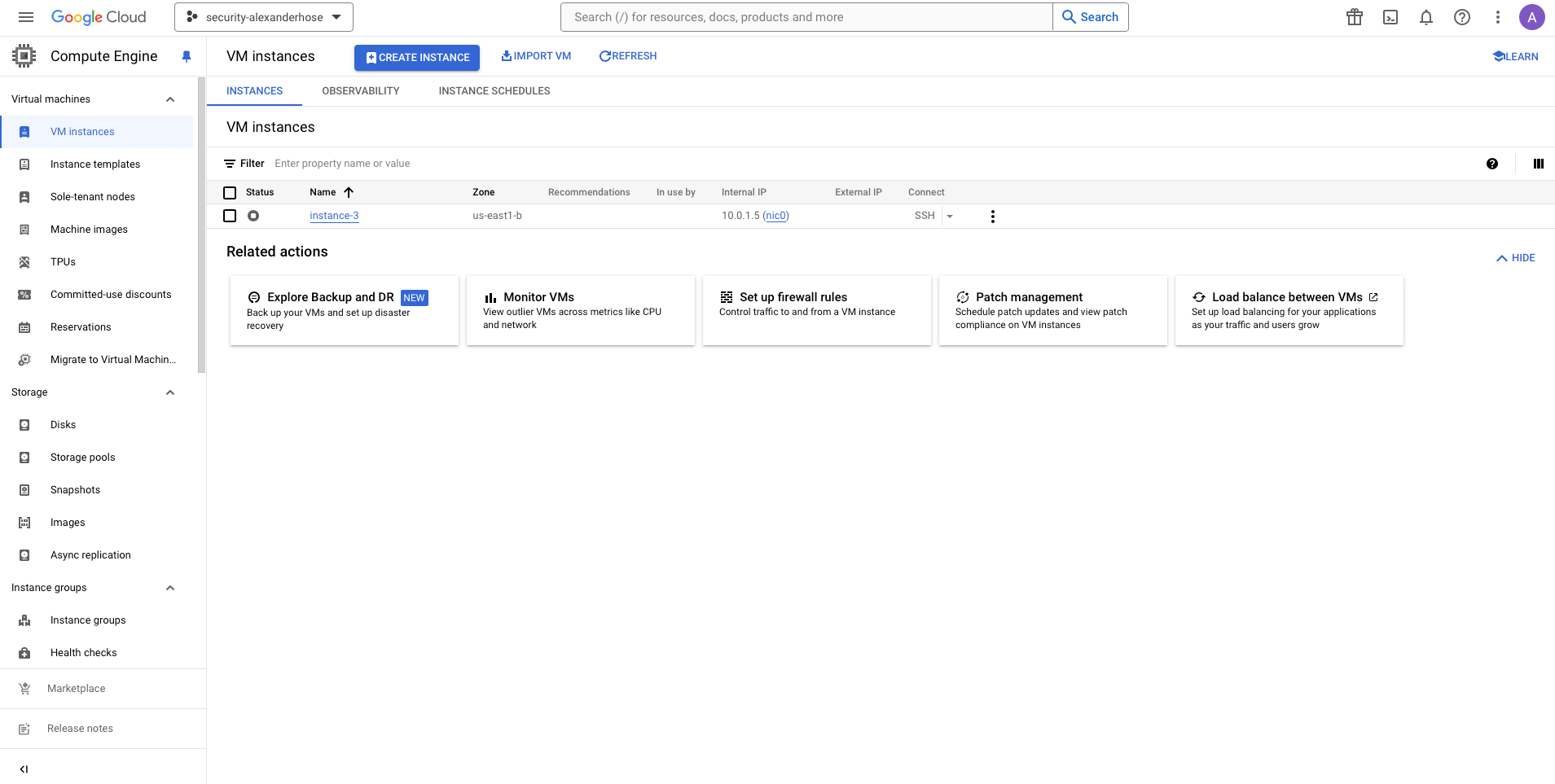
Step 4: Accessing GCP Compute Engine Service
With the entitlement granted, the requester can now access the GCP compute instances as per the defined roles and permissions.
- Navigate to the Compute Engine section and ensure you have the necessary permissions to access the instances.
- Perform the required tasks within the scope and duration of the granted entitlement. The user can now perform actions on the compute instance service.
Conclusion 🎓
GCP’s Privileged Access Manager is a powerful tool that significantly enhances the security posture of your cloud environment by managing temporary access to critical resources. Previously, I had to use workarounds with IAM conditions, which required adding them to CI/CD pipelines and lacked proper audit trails. With PAM, you have a much better solution that streamlines access management and ensures comprehensive logging and compliance.









Member discussion