Introduction
When you build applications and solutions, you want to restrict access to other AWS services. Typically, you would use IAM policies and roles to accomplish this task. However, managing these policies can get quite complicated. Luckily, AWS recently introduced several new features for the IAM Access Analyzer, providing users greater insight into how policies interact with resources on their accounts. IAM Access Analyzer now analyzes CloudTrail events across 140 AWS services and generates fine-grained policies based on the activities performed.
To access the new feature, we need to navigate to the Permissions tab of an existing IAM role. You need to scroll down and choose to generate a new policy based on CloudTrail events.

Join our community of cloud security professionals. 🔐
Subscribe to our newsletterAfterward, you can choose the period and regions to analyze. It will automatically check all activities performed by the role in the set period and then generate the policy.

Policy for the IAM access analyzer role
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "cloudtrail:GetTrail",
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"iam:GenerateServiceLastAccessedDetails",
"iam:GetServiceLastAccessedDetails"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:ListBucket"
],
"Resource": [
"arn:aws:s3:::<CloudTrailS3Bucket>",
"arn:aws:s3:::<CloudTrailS3Bucket>/*"
]
}
]
}Trust relationship for the IAM access analyzer role
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "access-analyzer.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}It will take a few minutes and you will be promoted that the new policy was successfully generated. We can then review the generated policy and add any actions that were not identified.
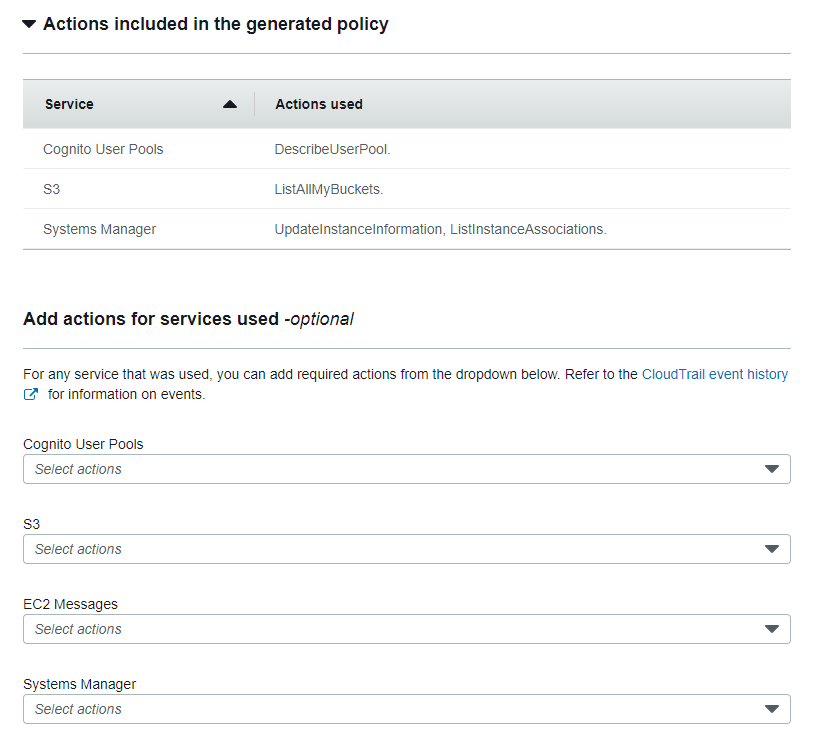
In my case, the generated policy has two statements. But there are still some placeholders that we need to replace. After that, it automatically creates and attaches the policy.
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:ListAllMyBuckets",
"ssm:ListInstanceAssociations",
"ssm:UpdateInstanceInformation"
],
"Resource": "*"
},
{
"Effect": "Allow",
"Action": "cognito-idp:DescribeUserPool",
"Resource": "arn:aws:cognito-idp:${Region}:${Account}:userpool/${UserPoolId}"
}
]
}Keep in mind that the existing policies will not be removed automatically.








Member discussion