Introduction
Today, we'll be exploring a powerful feature that allows you to export GCP Security Command Center findings to Pub/Sub, and then effortlessly transform them via Cloud Functions for seamless integration with other systems.
Understanding GCP Security Command Center 🧠
Before we jump into the nitty-gritty details, let's quickly recap what GCP Security Command Center is all about. It's like your cloud security guardian angel, constantly monitoring and analyzing your GCP resources for potential vulnerabilities, misconfigurations, and suspicious activity.
Exporting to Pub/Sub - A Game-Changing Move 📤
Now, imagine having the ability to export these findings to Pub/Sub in just a few clicks. Pub/Sub (short for Publisher/Subscriber) is GCP's messaging service that lets different components of your application communicate with each other asynchronously. By exporting your security findings to Pub/Sub, you're creating a centralized hub for real-time information flow.
Setup 🏗️
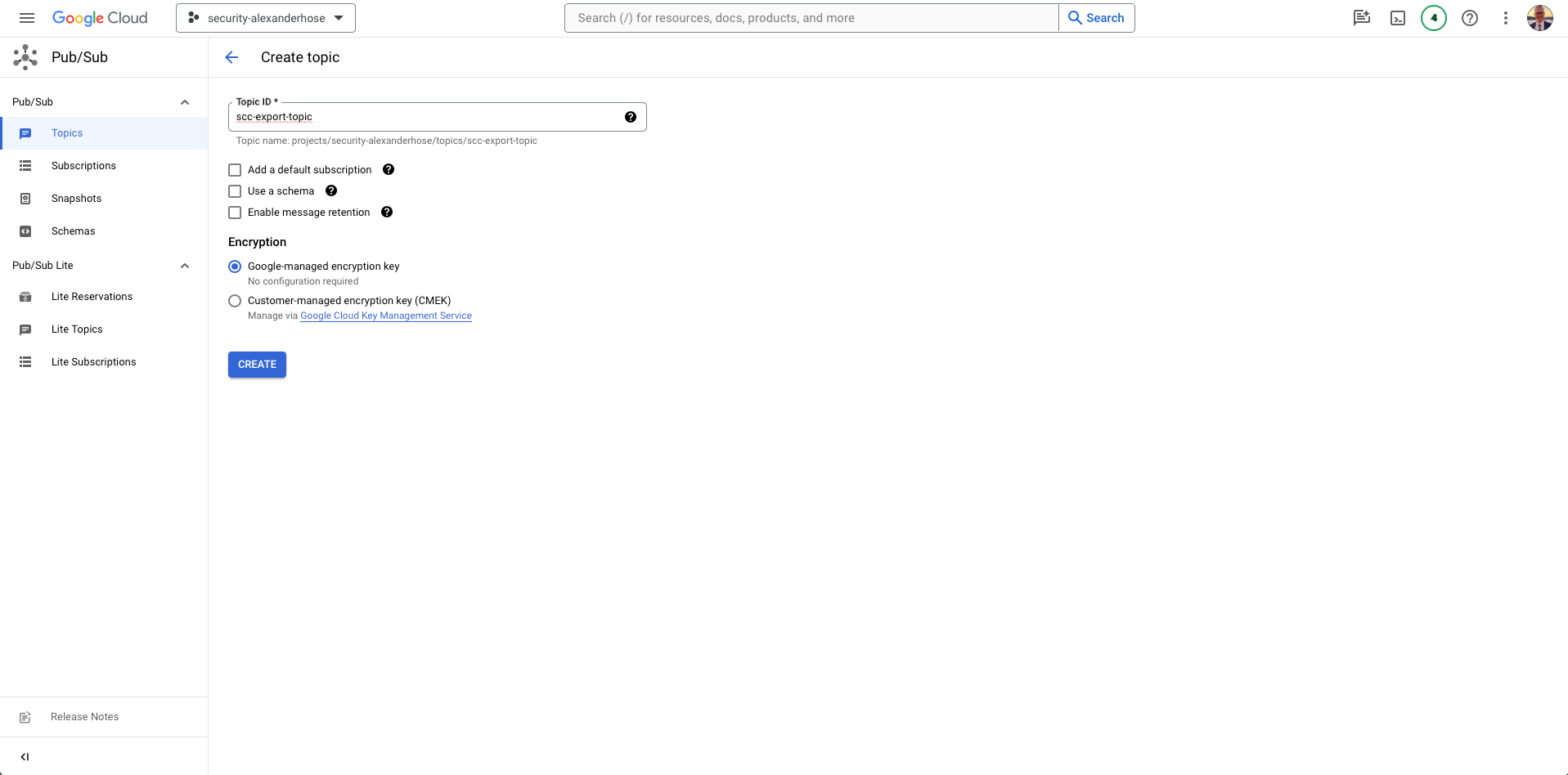
Creating Pub/Sub Topic ✉️
Create a Pub/Sub topic, your gateway to seamlessly exporting GCP Security Command Center findings and consume it by other GCP services.
- Navigate to Pub/Sub:
Open your GCP console and head over to the Pub/Sub section in the security project of your organization. - Create a Topic:
- Click on "Topics" in the left navigation menu.
- Hit the "Create Topic" button.
- Give your topic a meaningful name, like
SecurityFindingsTopicorscc-export-topic - Save the configuration.
- Note Down the Topic Name:
- After creation, note down the full topic name (in the format:
projects/[PROJECT_ID]/topics/[TOPIC_NAME]), as you'll need it shortly.
- After creation, note down the full topic name (in the format:
Creating IAM Service Account for Cloud Function 🔑
Create an IAM service account, ensuring the enable your Cloud Function to interact with the pub/sub service.
- Navigate to IAM & Admin:
Go to the IAM & Admin section in your GCP console in the security project of your organization. - Create a New Service Account:
- Click on "Service accounts."
- Hit the "Create Service Account" button.
- Name it as
pubsubor something meaningful - Assign the role
Cloud Run Invokerto the service account.
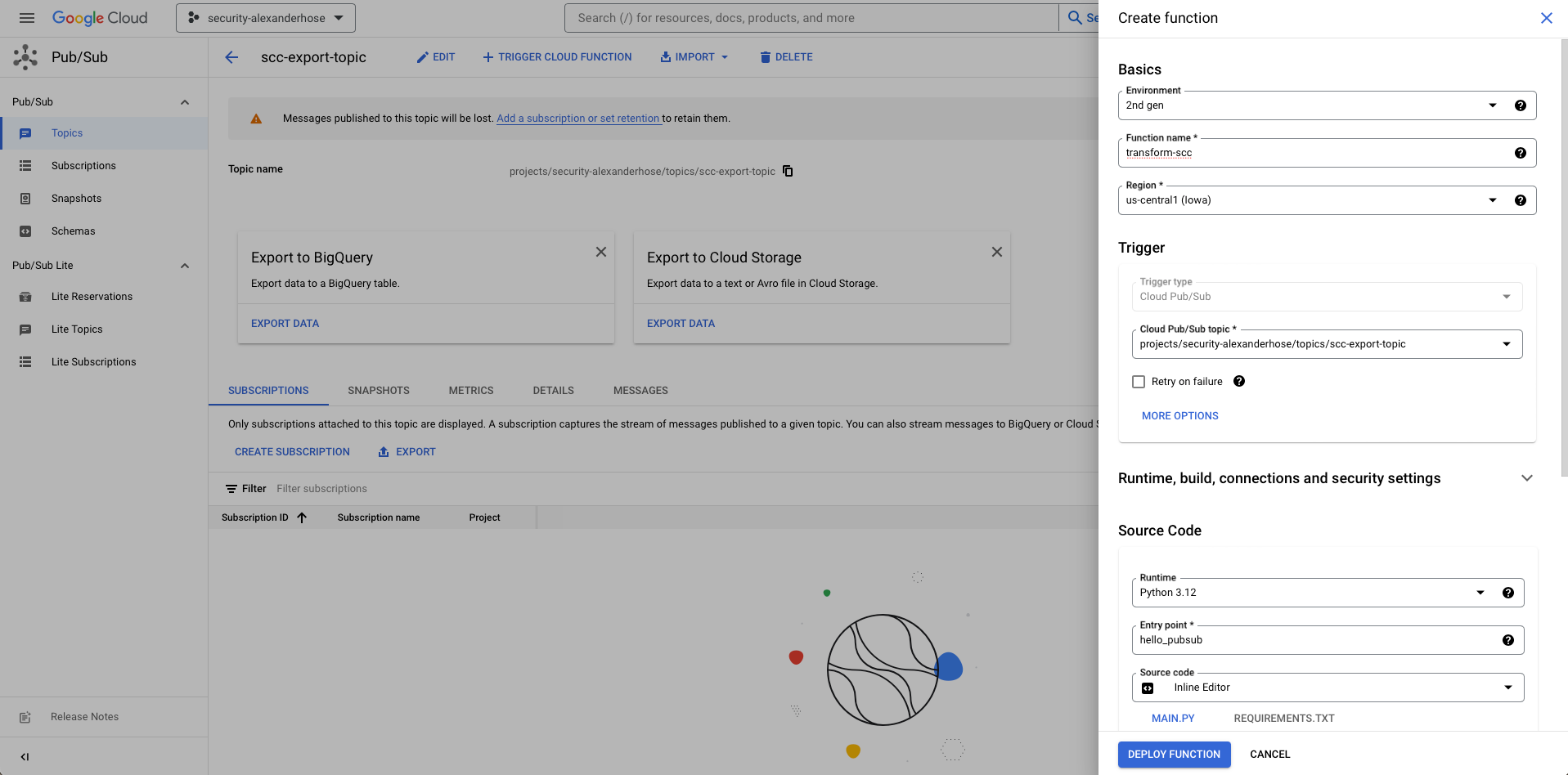
Creating Cloud Function Trigger 🔄
Create a Cloud Function trigger, that transforms GCP Security Command Center findings into actionable insights through our Pub/Sub topic.
- Navigate to Pub/Sub Topics:
Open the Pub/Sub section in your GCP console and select "Topics" from the left navigation menu. - Select Your Topic:
- Click on the Pub/Sub topic you created for Security Command Center findings.
- Add a Trigger:
- At the top, click on "Trigger Cloud Function"
- Create Cloud Function:
- Provide a name for your function, such as "SecurityFindingsProcessor"
- Choose the runtime and allocate resources as needed.
- Now its time to write the logic to access the data from SCC, you can use the following code
import base64
import functions_framework
@functions_framework.cloud_event
def get_scc(cloud_event):
data = base64.b64decode(cloud_event.data["message"]["data"])
print(data)- Add Service Account:
- Scroll down to the "Security" section.
- Under "Service account," choose the service account you created earlier for Pub/Sub authentication.
- Deploy Your Function:
- Hit the "Deploy" button to deploy your Cloud Function.
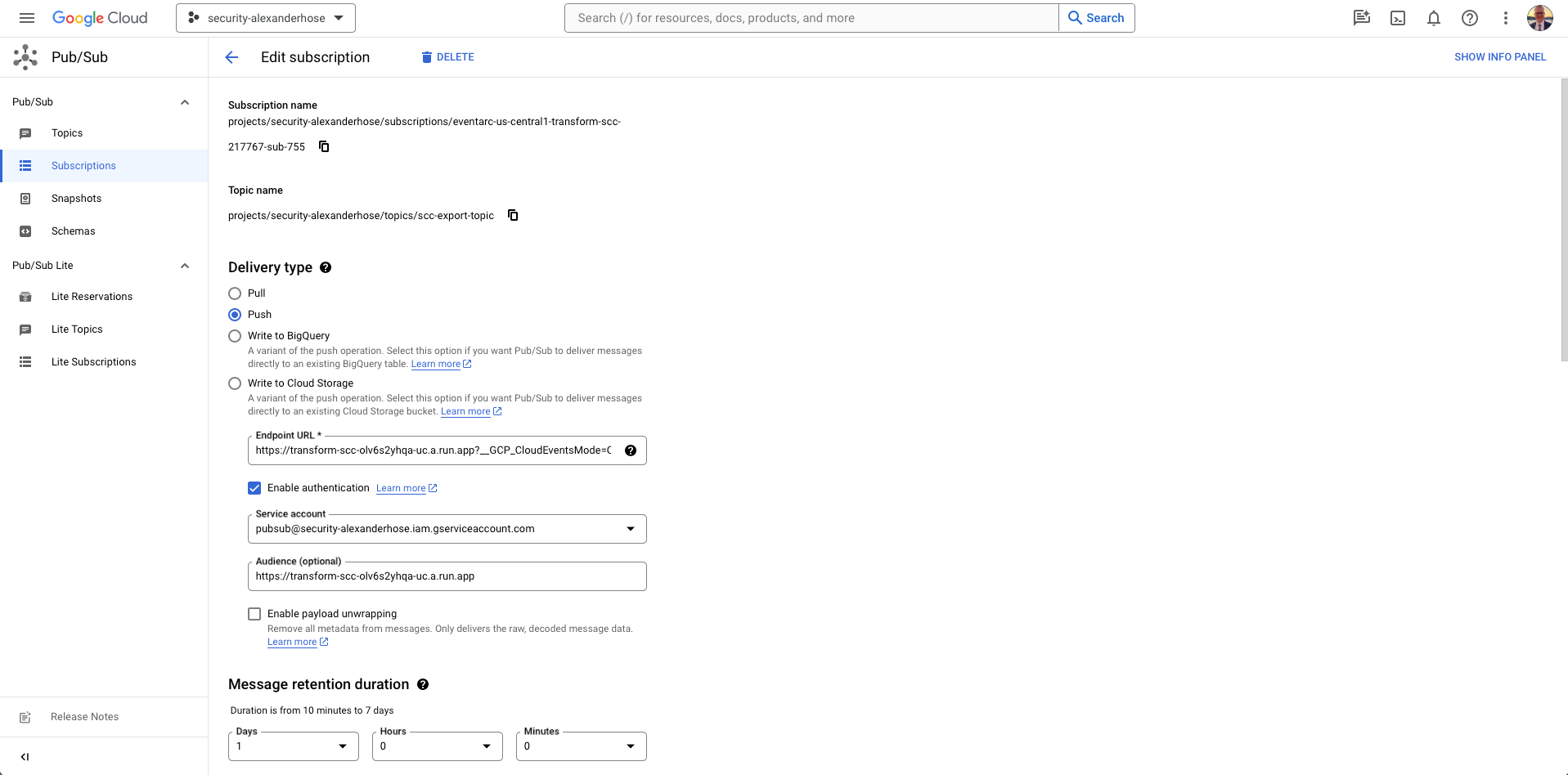
Change Subscription Service Account Authentication 🔒
Ensure your Pub/Sub subscription aligns with the service account trusted by your Cloud Function, eliminating the risk of The request was not authenticated errors.
- Configure Subscription Details:
- In the newly created subscription details, locate the "Delivery type" section.
- Find the "Service account" field.
- Set Service Account for Subscription:
- Choose the service account that your Cloud Function is configured to use for authentication.
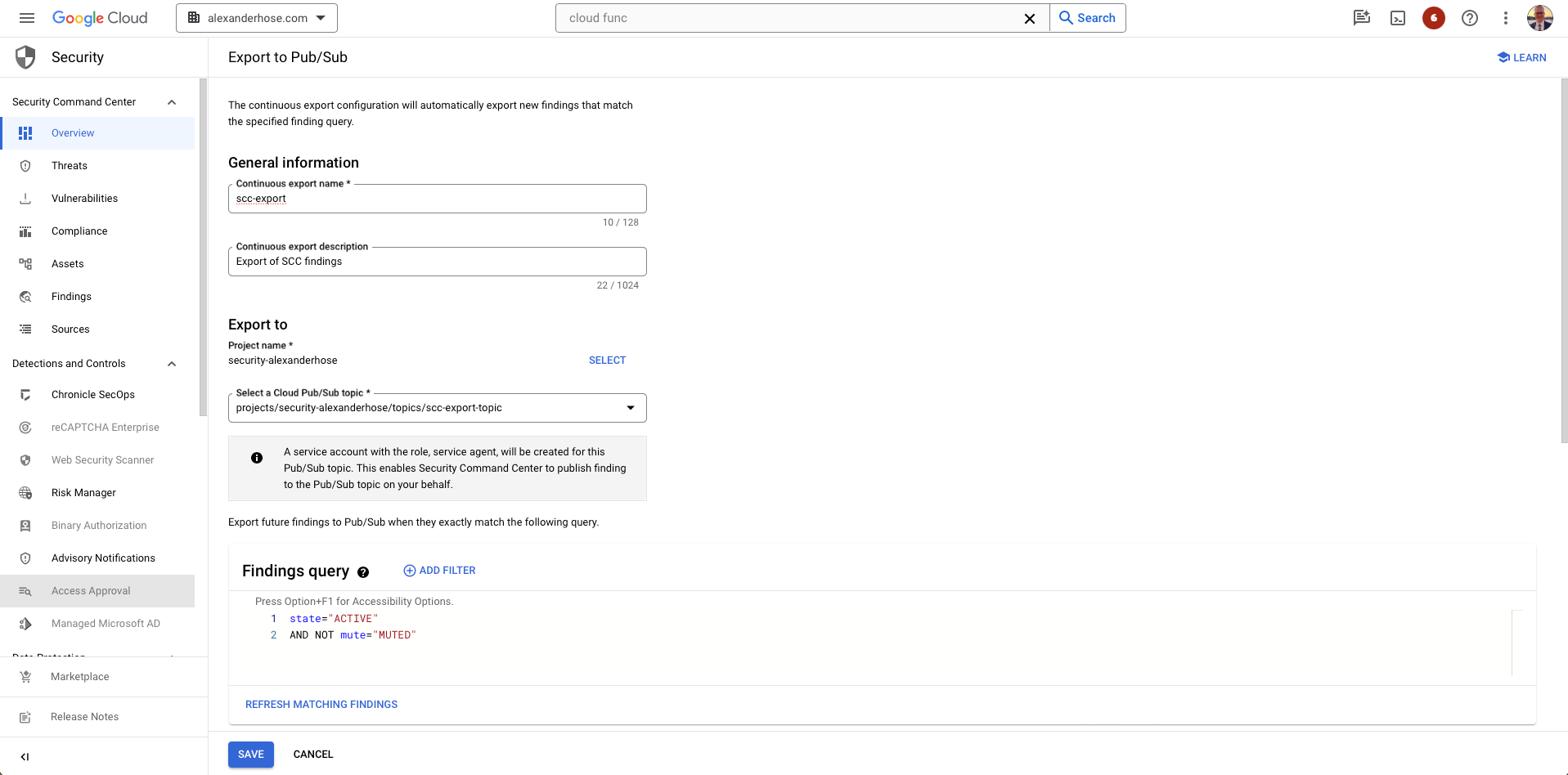
Configuring GCP Security Command Center Continuous Export 📊
Configure continuous export from GCP Security Command Center to Pub/Sub, unleashing real-time insights.
- Navigate to Security Command Center
Go to the Security Command Center service in your GCP console, ensuring you're in the organization account for centralized findings. - Access Settings
- Click on "Settings" in the left navigation menu.
- Choose "Continuous Export" from the dropdown menu.
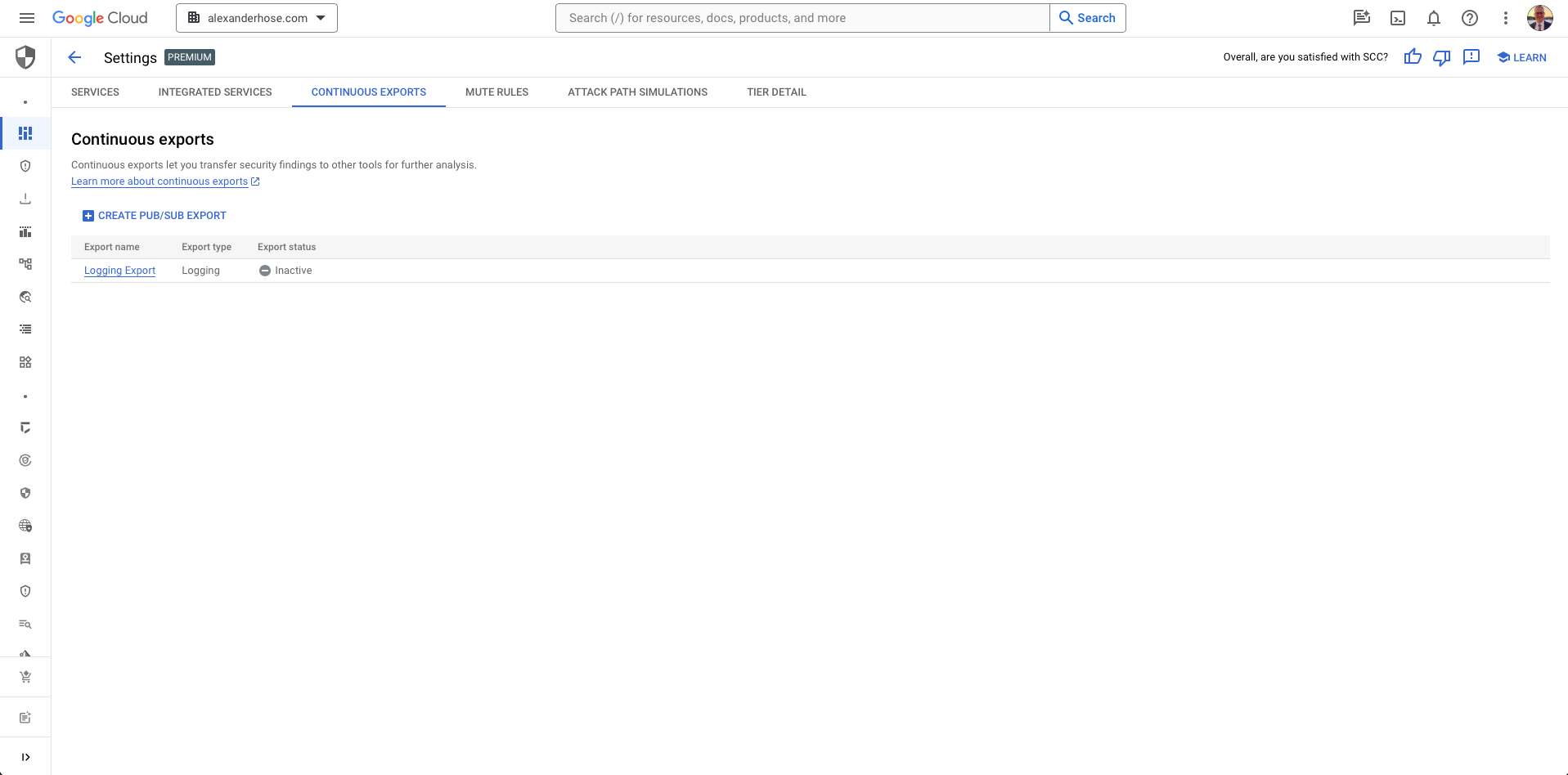
- Choose Pub/Sub Topic
- Select your previously created Pub/Sub topic as the export destination.
- Adjust the query if needed, ensuring only critical findings are exported.
Integrating with Other Systems 🔗
The real power of this setup lies in its ability to integrate with other systems effortlessly. Whether you're using third-party security tools, a custom dashboard, or anything in between, your transformed findings are ready to be consumed.
Conclusion 🎓
By exporting GCP Security Command Center findings to Pub/Sub and transforming them via Cloud Functions, you're not only streamlining your security operations but also opening up a world of possibilities for integration with other systems. So, go ahead, give your cloud security strategy the boost it deserves!
Common issues 🐛
In the process of setting up your Pub/Sub integration with GCP Security Command Center findings and Cloud Functions, you might encounter the The request was not authenticated error. You can fix that by making sure the right service account is set for the pub/sub subscription.
The request was not authenticated. Either allow unauthenticated invocations or set the proper Authorization header. Read more at https://cloud.google.com/run/docs/securing/authenticating Additional troubleshooting documentation can be found at: https://cloud.google.com/run/docs/troubleshooting#unauthorized-client








Member discussion