Introduction
While companies increasingly adopt cloud-based solutions, one of the key challenges they face is safeguarding their data from potential threats. Google Cloud Platform (GCP) offers a powerful solution to this challenge through its Virtual Private Cloud (VPC) Service Controls. Empowering your organization to enhance its security and compliance measures effectively.
Understanding GCP VPC Service Controls 👨🎓
GCP's VPC Service Controls provide a robust framework for securing data within your cloud environment. It allows you to define folders or a project to protect. Afterward, you can assign service perimeters around specific resources, granting granular access controls for GCP APIs. VPC Service Perimeters function like a firewall for GCP APIs.
Key Benefits of GCP VPC Service Controls 💼
1. Strengthened Data Security
With GCP VPC Service Controls, you can establish security perimeters around sensitive data, applications, and resources. This segmentation ensures that only authorized entities can access and interact with the protected resources, reducing the chances of data breaches and unauthorized access attempts.
2. Compliance with Regulatory Standards
Achieving compliance with various industry-specific regulations can be a complex and challenging task. However, GCP VPC Service Controls offer a solution by enabling you to enforce data access and usage policies consistently.
3. Prevention of Data Exfiltration
Data exfiltration is a critical concern for anyone dealing with sensitive information. GCP VPC Service Controls provide an added layer of protection against data exfiltration attempts. By implementing these controls, you can monitor data movement and establish alerts for any suspicious activities. Therefore mitigating potential data breaches and ensuring early detection.
Implementing GCP VPC Service Controls 🔨
Create VPC Service Control access policy
First, you need to navigate to our Organization account.
Choose Security in the sidebar and navigate to VPC Service Controls. From there you can create your first policy. You can either select a single project or a folder. All resources within the project or folder will adhere to the policy.
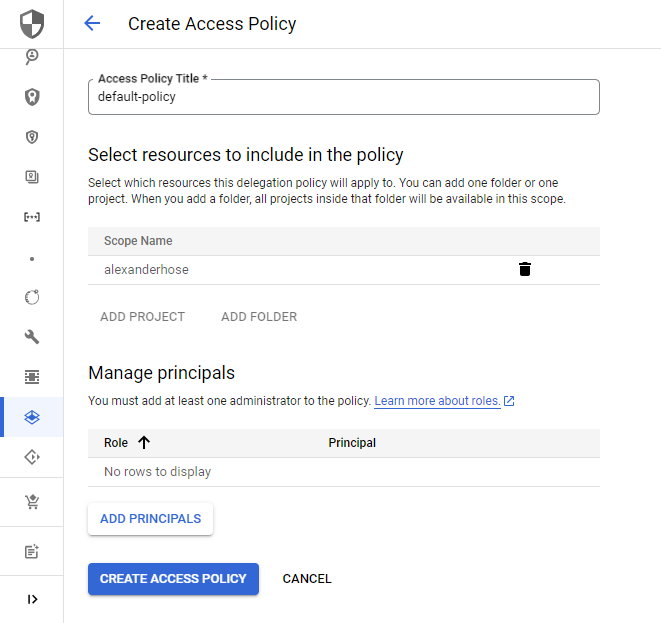
Create VPC Service Perimeters
Now you can navigate to any of the projects in the scope of the previously created Access Policy and create the VPC Service Perimeters. I always recommend trying the permiteres in the dry run mode first, before changing it to enforcement. In the creation process, you can choose between two perimeter types. The regular type protects services in the perimeter and the bridge type facilitates access between different service perimeters.
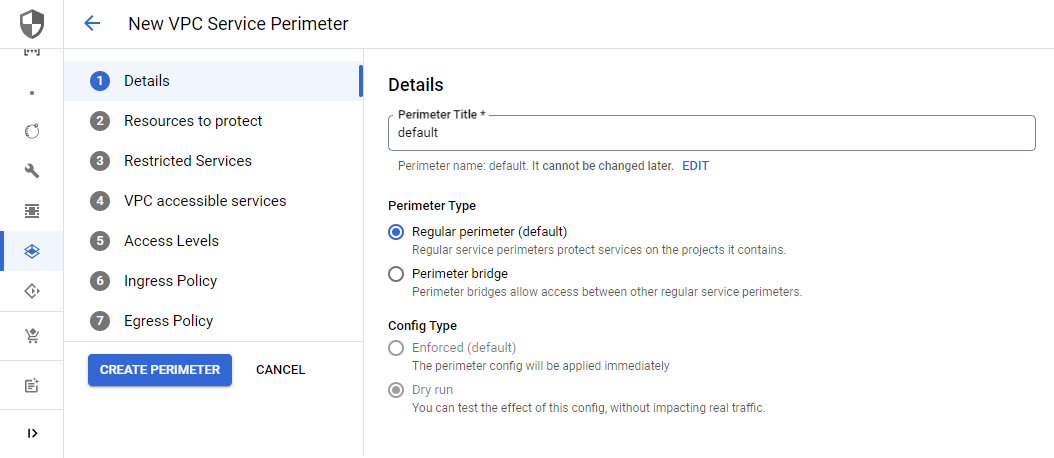
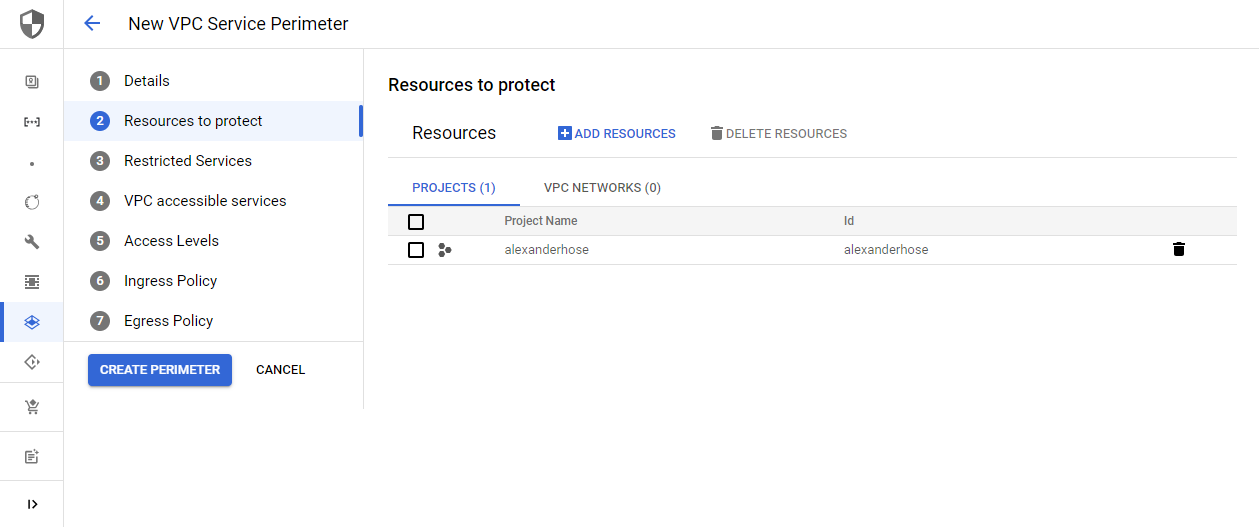
In the next step, you can choose which resources to protect. You can either choose a project within our VPC Service Policy or any VPC network.
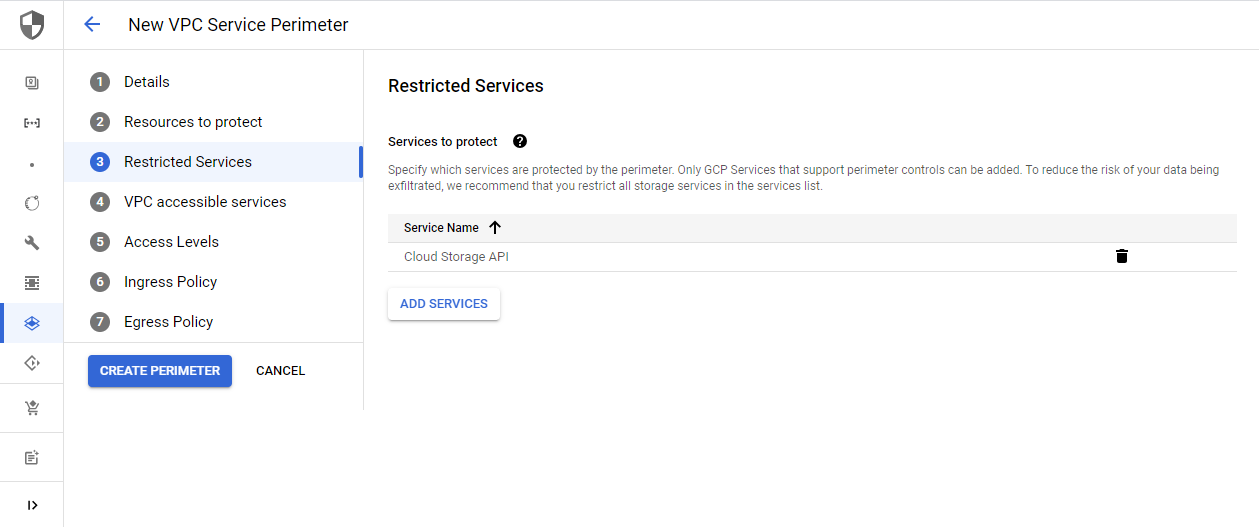
Define the services that you want to protect within the perimeter. One of the main reasons for VPC Service Perimertes is data exfiltration. Therefore I would advise you to restrict all storage services like the Cloud Storage API.
Next, choose the services that should be accessible through Private Google Access. Keep in mind that this only considers Private Google Access. This list does not restrict calls between GCP services.
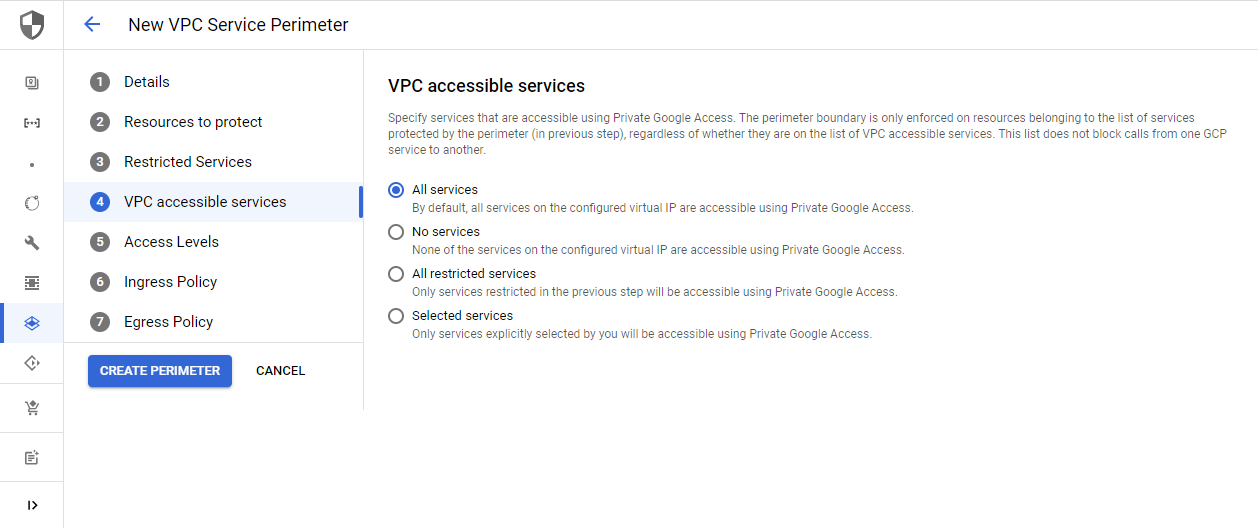
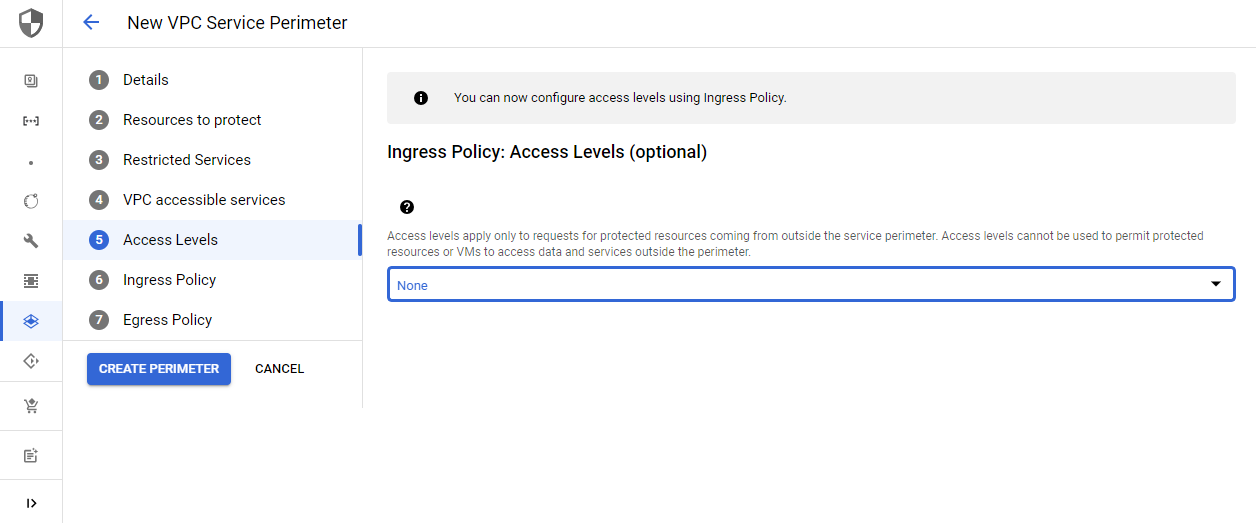
Access levels are limited to external requests targeting protected resources within the service perimeter. You can choose geographic locations or IP subnetworks for example. This can be configured via the Access Context Manager, a separate GCP service. You can find all information in my separate guide:

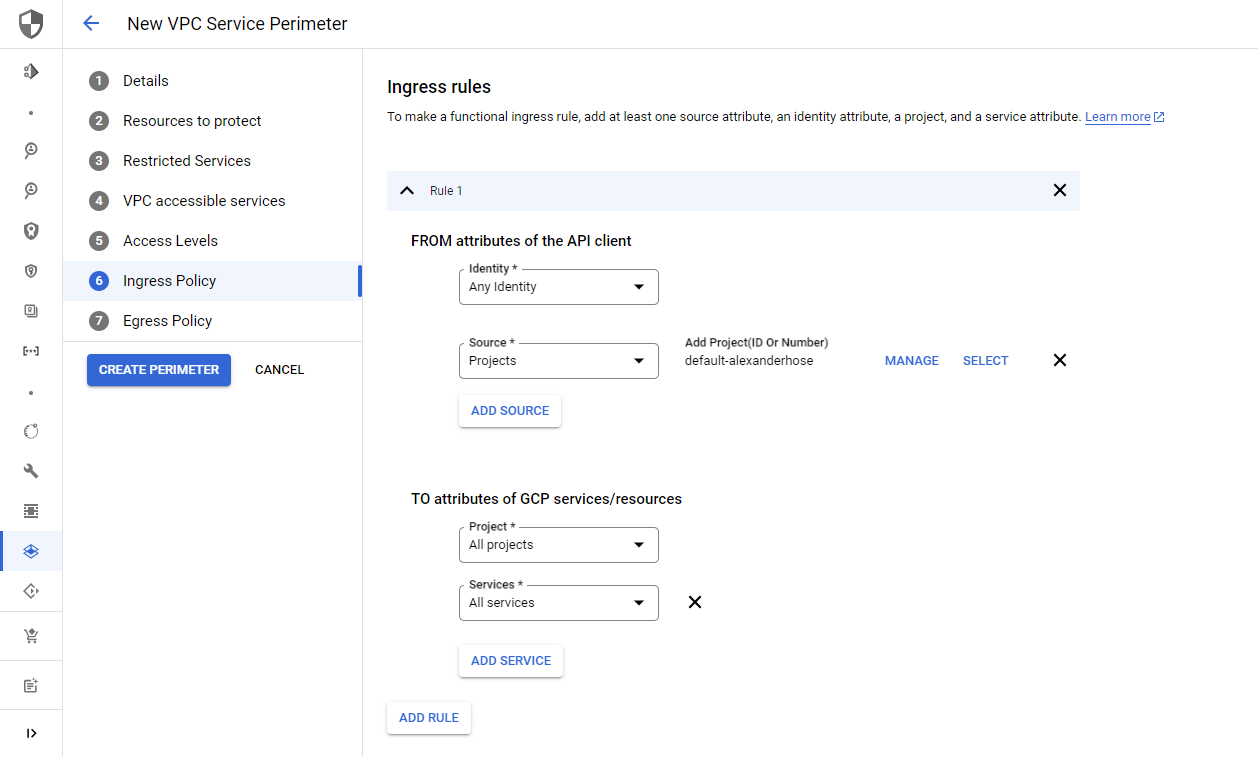
The ingress and egress rules define the direction of allowed access between different identities and resources.
In our case, you want to restrict the Cloud Storage API to Any identities from the default-alexanderhose project. The target is all projects in our previously defined VPC Service Control access policy.
Afterward, you create the service perimeter and will be presented with the configuration. Make sure to hit the enforce button, once you are happy with your configuration and your GCP APIs are protected.
// Projects (project id)
security-alexanderhose (1234567890)
// VPC Networks
// Services
Cloud Storage API
Ingress Rule 1
From:
Identities: ANY_IDENTITY
Projects:
default-alexanderhose
To:
Projects: All projects
Services =
Services name: All services
// No egress policy
// VPC Accessible Services
All services allowed
// Access levels
Testing the setup 🧪
You have restricted access to the Cloud Storage API with the above configuration to identities in your default-alexanderhose project.
Now let's try to list all files in our bucket, from your local computer or any other GCP project. You will receive an error message hinting at an issue with service controls and a unique ID vpcServiceControlsUniqueIdentifier. As expected the call to the GCP API was not successful.
$ gcloud storage ls gs://bucket-alexanderhose/
ERROR: (gcloud.storage.ls) User [[email protected]] does not have permission to access b instance [bucket-alexanderhose] (or it may not exist): Request is prohibited by organization's policy. vpcServiceControlsUniqueIdentifier: bhPfWOMbDqjXm5DjHlaEJnXnEVFheifu67FeobggxnwPoIBOZ41tKQ
Next, we try to run the same command from the default-alexanderhose project. This time we are presented with the content of our bucket. You have successfully protected the Cloud Storage API in your project 🎉
$ gcloud storage ls gs://bucket-alexanderhose/
gs://bucket-alexanderhose/secret.jsonDebug access 🚧
Debugging the implementation of GCP VPC Service Controls is crucial to ensure the security and functionality of your GCP environment. When encountering issues, you can leverage the GCP Logs Explorer. This feature allows you to examine and analyze logs generated by various GCP services, aiding in the identification of potential misconfigurations or access violations within the VPC Service Controls. When investigating problems, focus on filtering logs based on relevant parameters such as time range and the vpcServiceControlsUniqueIdentifier in the error message.
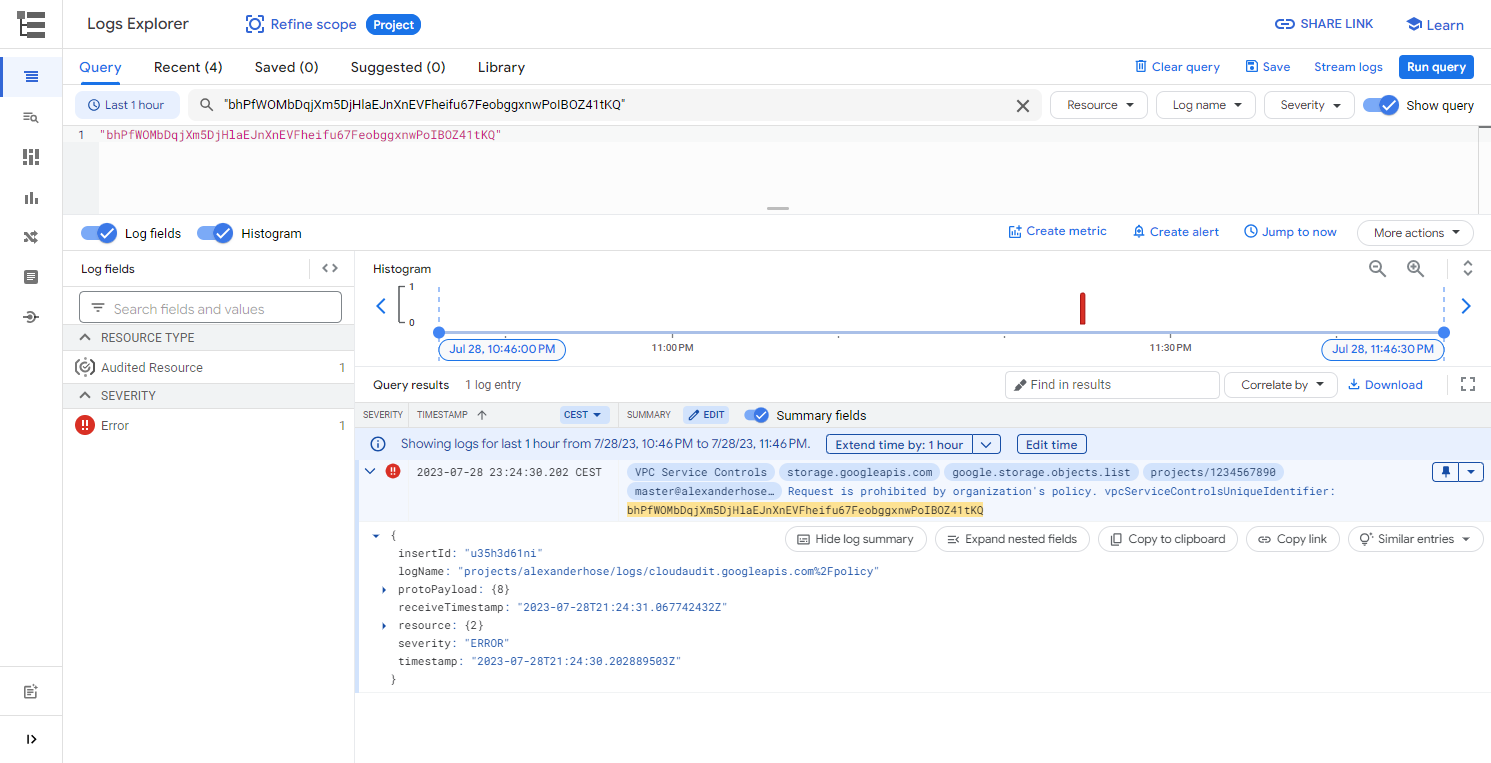
Alternatively, you can also use the VPC Service Controls Troubleshooter. It is accessible from the VPC Service Controls dashboard.
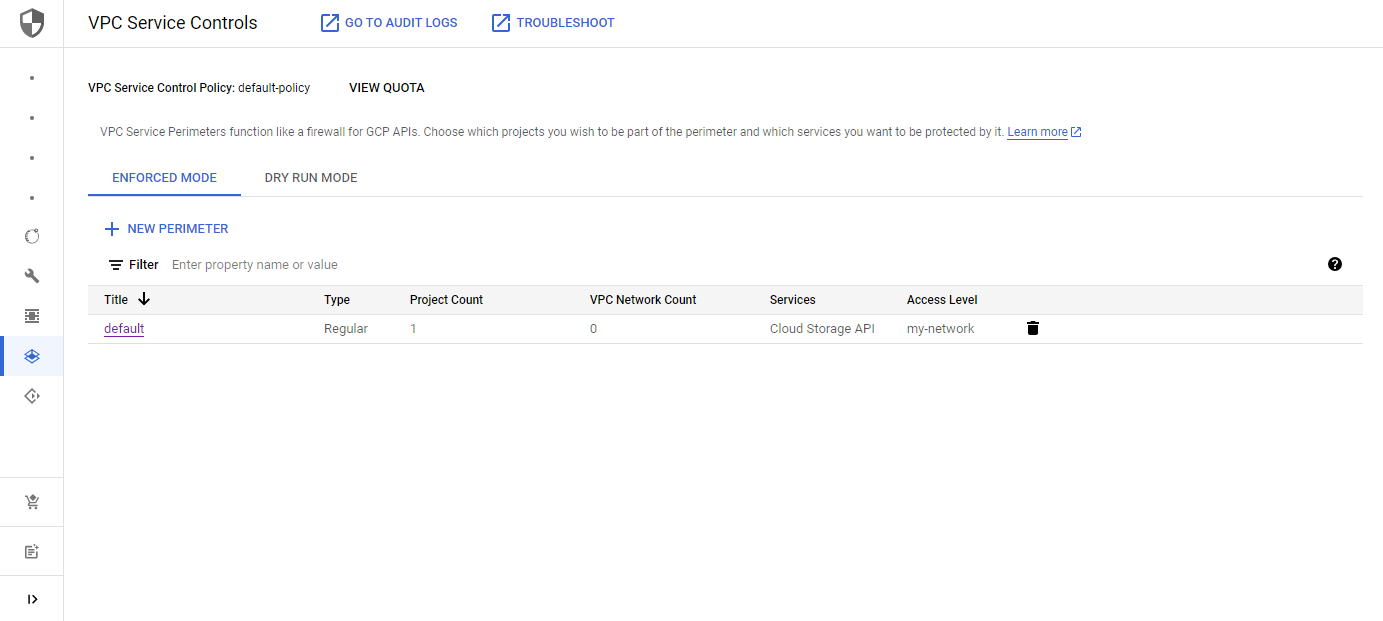
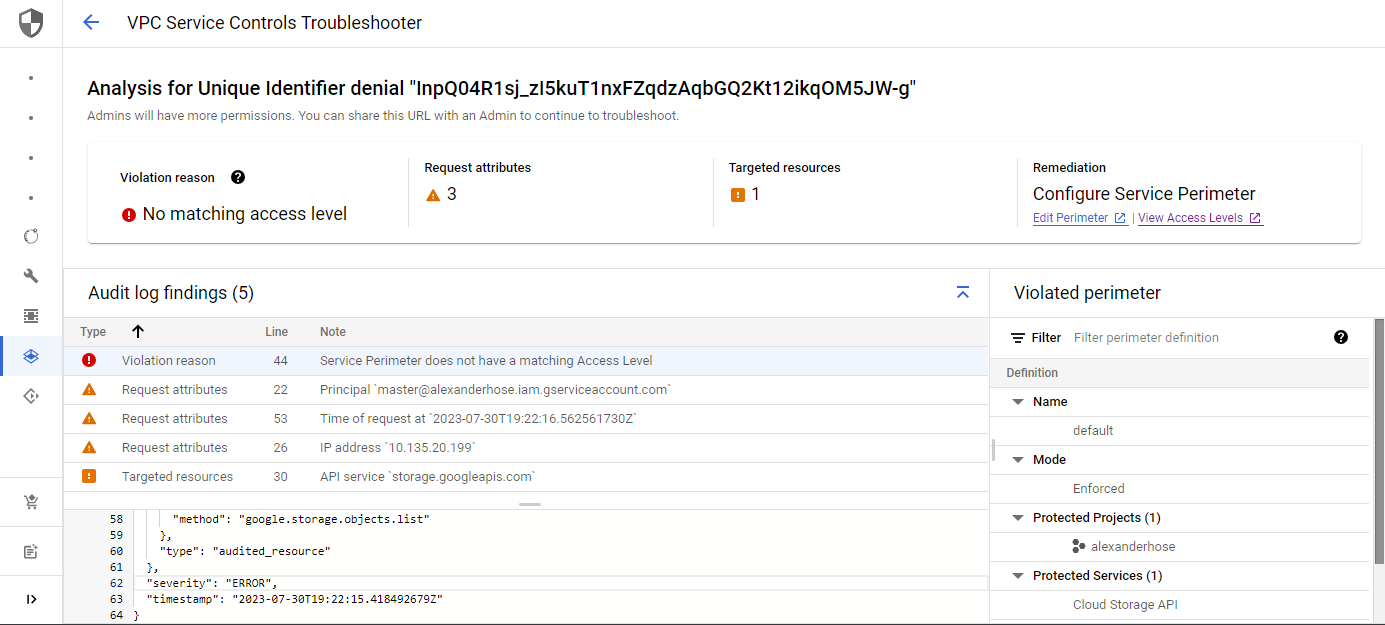
Here we can deep-dive into the request and get a nice overview of the findings of the logs.
Conclusion 🎓
In conclusion, GCP VPC Service Controls offer a robust and efficient means of enhancing security and compliance in the cloud. By strategically implementing these controls, you can improve your data protection strategies, meet regulatory requirements, and safeguard sensitive information.
One consideration you need to take into account is, that you have an additional policy taking care of the authorization of services in your GCP projects.










Member discussion